Abstract
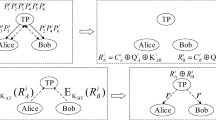
Based on EPR pairs, this paper proposes a different quantum private comparison (QPC) protocol enabling two parties to compare the equality of their information without revealing the information content. Due to the use of quantum entanglement of Bell state as well as one-way quantum transmission, the new protocol provides easier implementation as well as better qubit efficiency (near 50%) than the other QPCs. It is secure against Trojan horse attack and other well-known attacks.
Similar content being viewed by others
References
Bennett, C.H., Brassard, G.: Quantum cryptography: public-key distribution and coin tossing. In: Proceedings of IEEE International Conference on Computers, Systems and Signal Processing, New York, Bangalore, India, 175–179 (1984)
Lo H.K., Chau H.F.: Unconditional security of quantum key distribution over arbitrarily long distances. Science 283(5410), 2050–2056 (1999)
Long G.L., Liu X.S.: Theoretically efficient high-capacity quantum-key distribution scheme. Phys. Rev. A 65(3), 032302 (2002)
Gao G.: Quantum key distribution by comparing Bell states. Opt. Commun. 281(4), 876–879 (2008)
Yuan H., Song J., Han L.F., Hou K., Shi S.H.: Improving the total efficiency of quantum key distribution by comparing Bell states. Opt. Commun. 281(18), 4803–4806 (2008)
Bennett C.H., Brassard G., Crépeau C., Jozsa R., Peres A., Wootters W.K.: Teleporting an unknown quantum state via dual classical and Einstein–Podolsky–Rosen channels. Phys. Rev. Lett. 70(13), 1895–1899 (1993)
Furusawa A., Sørensen J.L., Braunstein S.L., Fuchs C.A., Kimble H.J., Polzik E.S.: Unconditional quantum teleportation. Science 282(5389), 706–709 (1998)
Zhang Z.J., Man Z.X.: Many-agent controlled teleportation of multi-qubit quantum information. Phys. Lett. A 341(1–4), 55–59 (2005)
Zhang W., Liu Y.M., Liu J., Zhang Z.J.: Teleportation of arbitrary unknown two atom state with cluster state via thermal cavity. Chin. Phys. B 17(9), 3203–3208 (2008)
Zhang Z.Y., Liu Y.M., Zuo X.Q., Zhang W., Zhang Z.J.: Transformation operator and criterion for perfectly teleporting arbitrary three-qubit state with six-qubit channel and Bell-state measurement. Chin. Phys. Lett. 26(12), 120303 (2009)
Tsai C.W., Hwang T.: Teleportation of a pure EPR state via GHZ-like state. Int. J. Theor. Phys. 49(8), 1969–1975 (2010)
Hillery M., Buzek V., Berthiaume A.: Quantum secret sharing. Phys. Rev. A 59(3), 1829–1834 (1999)
Xiao L., Long G.L., Deng F.G., Pan J.W.: Efficient multiparty quantum secret sharing schemes. Phys. Rev. A 69(5), 052307 (2004)
Zhang Z.J., Man Z.X.: Multiparty quantum secret sharing of classical messages based on entanglement swapping. Phys. Rev. A 72(2), 022303 (2005)
Deng F.G., Long G.L., Zhou H.Y.: An efficient quantum secret sharing scheme with Einstein–Podolsky–Rosen pairs. Phys. Lett. A 340(1–4), 43–50 (2005)
Deng F.G., Zhou H.Y., Long G.L.: Circular quantum secret sharing. J. Phys. A: Math. Gen. 39(45), 14089–14099 (2006)
Han L.F., Liu Y.M., Liu J., Zhang Z.J.: Multiparty quantum secret sharing of secure direct communication using single photons. Opt. Commun. 281(9), 2690–2694 (2008)
Deng F.G., Li X.H., Zhou H.Y.: Efficient high-capacity quantum secret sharing with two-photon entanglement. Phys. Lett. A 372(12), 1957–1962 (2008)
Sun Y., Wen Q.Y., Gao F., Chen X.B., Zhu F.C.: Multiparty quantum secret sharing based on Bell measurement. Opt. Commun. 282(17), 3647–3651 (2009)
Shi R.H., Huang L.S., Yang W., Zhong H.: Multiparty quantum secret sharing with Bell states and Bell measurements. Opt. Commun. 283(11), 2476–2480 (2010)
Bostroem K., Felbinger T.: Deterministic secure direct communication using entanglement. Phys. Rev. Lett. 89(18), 187902 (2002)
Deng F.G., Long G.L., Liu X.S.: Two-step quantum direct communication protocol using the Einstein–Podolsky–Rosen pair block. Phys. Rev. A 68(4), 042317 (2003)
Man Z.X., Zhang Z.J., Li Y.: Deterministic secure direct communication by using swapping quantum entanglement and local unitary operations. Chin. Phys. Lett. 22(1), 18–21 (2005)
Zhan Y.B., Zhang L.L., Zhang Q.Y.: Quantum secure direct communication by entangled qutrits and entanglement swapping. Opt. Commun. 282(23), 4633–4636 (2009)
Yang C.W., Tsai C.W., Hwang T.: Fault tolerant two-step quantum secure direct communication protocol against collective noises. Sci. China Ser. G: Phys. Mech. Astron. 54(3), 496–501 (2011)
Yang Y.G., Wen Q.Y.: An efficient two-party quantum private comparison protocol with decoy photons and two-photon entanglement. J. Phys. A: Math. Theor. 42(5), 055305 (2009)
Chen X.B., Xu G., Niu X.X., Wen Q.Y., Yang Y.X.: An efficient protocol for the private comparison of equal information based on the triplet entangled state and single particle measurement. Opt. Commun. 283(7), 1561–1565 (2010)
Yao, A.C.: Protocols for secure computations. In: Proceedings of 23rd IEEE Symposium on Foundations of Computer Science (FOCS’ 82), Washington, DC, USA, p. 160 (1982)
Lo H.K.: Insecurity of quantum secure computations. Phys. Rev. A 56(2), 1154–1162 (1997)
Boudot F., Schoenmakers B., Traor’e J.: A fair and efficient solution to the socialist millionaires’ problem. Discr. Appl. Math. (Special issue on coding and cryptology) 111(1–2), 23–36 (2001)
Hillery M., Ziman M., Bužek V., Bieliková M.: Towards quantum-based privacy and voting. Phys. Lett. A 349(1–4), 5–81 (2006)
Vaccaro J.A, Spring J., Chefles A.: Quantum protocols for anonymous voting and surveying. Phys. Rev. A 75(1), 012333 (2007)
Hogg T., Harsha P., Chen K.Y.: Quantum auctions. Int. J. Quantum Inf. 5, 751–780 (2007)
Yang Y.G., Naseri M., Wen Q.Y.: Improved secure quantum sealed-bid auction. Opt. Commun. 282(20), 4167–4170 (2009)
Zhao Z., Naseri M., Zheng Y.: Secure quantum sealed-bid auction with post confirmation. Opt. Commun. 283(16), 3194–3197 (2010)
Deng F.G., Li X.H., Zhou H.Y., Zhang Z.J.: Improving the security of multiparty quantum secret sharing against Trojan horse attack. Phys. Rev. A 72(4), 044302 (2005)
Cai Q.Y.: Eavesdropping on the two-way quantum communication protocols with invisible photons. Phys. Lett. A 351(1–2), 23–25 (2006)
Li X.H., Deng F.G., Zhou H.Y.: Improving the security of secure direct communication based on the secret transmitting order of particles. Phys. Rev. A 74(5), 054302 (2006)
Alain A., Jean D., Gérard R.: Experimental test of Bell’s inequalities using time varying analyzers. Phys. Rev. Lett. 49(25), 1804–1807 (1982)
Ou Z.Y., Pereira S.F., Kimble H.J., Peng K.C.: Realization of the Einstein–Podolsky–Rosen paradox for continuous variables. Phys. Rev. Lett. 68(25), 3663–3666 (1992)
Hagley E., Maître X., Nogues G., Wunderlich C., Brune M., Raimond J.M., Haroche S.: Generation of Einstein–Podolsky–Rosen pairs of atoms. Phys. Rev. Lett. 79(1), 1–5 (1997)
Hald J., Sørensen J.L., Schori C., Polzik E.S.: Spin squeezed atoms: a macroscopic entangled ensemble created by light. Phys. Rev. Lett. 83(7), 1319–1322 (1999)
Howell J.C., Bennink R.S., Bentley S.J., Boyd R.W.: Realization of the Einstein–Podolsky–Rosen paradox using momentum- and position-entangled photons from spontaneous parametric down conversion. Phys. Rev. Lett. 92(21), 210403 (2004)
Schuck C., Huber G., Kurtsiefer C., Weinfurter H.: Complete deterministic linear optics Bell state analysis. Phys. Rev. Lett. 96(19), 190501 (2006)
Saunders D.J., Jones S.J., Wiseman H.M., Pryde G.J.: Experimental EPR steering using Bell-local states. Nat. Phys. 6, 845–849 (2010)
Hwang T., Lee K.C.: EPR quantum key distribution protocols with 100% qubit efficiency. IET Inf. Secur. 1(1), 43–45 (2007)
Chen J.H., Lee K.C., Hwang T.: The enhancement of Zhou et al.’s quantum secret sharing protocol. Int. J. Mod. Phy. C 20(10), 1531–1535 (2009)
Shih H.C., Lee K.C., Hwang T.: New efficient three-party quantum key distribution protocols. IEEE J. Sel. Top. Quantum Electron. 15(6), 1602–1606 (2009)
Chong S.K., Hwang T.: Quantum key agreement protocol based on BB84. Opt. Commun. 283(6), 1192–1195 (2010)
Hsieh C.R., Tsai C.W., Hwang T.: Quantum secret sharing using GHZ-like state. Commun. Theor. Phys. 54(6), 1019–1022 (2010)
Chong S.K., Hwang T.: The enhancement of three-party simultaneous quantum secure direct communication scheme with EPR pairs. Opt. Commun. 284(1), 515–518 (2011)
Lin J., Hwang T.: An enhancement on Shi et al.’s multiparty quantum secret sharing protocol. Opt. Commun. 284(5), 1468–1471 (2011)
Nielsen M.A.: Quantum computation by measurement and quantum memory. Phys. Lett. A 308(2–3), 96–100 (2003)
Jeffrey E., Brenner M., Kwiat P.: Delayed-choice quantum cryptography. Proc. SPIE 5161, 269–279 (2004)
Jeffrey, E., Altepeter, J., Kwiat, P.: Relativistic quantum cryptography. Frontiers in Optics, OSA Technical Digest (CD) (Optical Society of America, 2006), paper FWB1
Jeffrey, E., Altepeter, J., Kwiat, P.: Relativistic quantum cryptography with optical storage. In: International Conference on Quantum Information, OSA Technical Digest (CD) (Optical Society of America, 2007), paper IFE1
Li X.H., Deng F.G., Zhou H.Y.: Efficient quantum key distribution over a collective noise channel. Phys. Rev. A 78(2), 022321 (2008)
Li X.H., Zhao B.K., Sheng Y.B., Deng F.G., Zhou H.Y.: Fault tolerant quantum key distribution based on quantum dense coding with collective noise. Int. J. Quant. Inform. 7(8), 1479–1489 (2009)
Zanardi P., Rasetti M.: Noiseless quantum codes. Phys. Rev. Lett. 79(17), 3306–3309 (1997)
Kempe J., Bacon D., Lidar D.A., Whaley K.B.: Theory of decoherence-free fault-tolerant universal quantum computation. Phys. Rev. A 63(4), 042307 (2001)
Knill E., Laflamme R., Viola L.: Theory of quantum error correction for general noise. Phys. Rev. Lett. 84(11), 2525–2528 (2000)
Gisin N., Ribordy G., Tittel W., Zbinden H.: Quantum cryptography. Rev. Mod. Phys. 74, 145–190 (2002)
Buttler W.T., Lamoreaux S.K., Torgerson J.R., Nickel G.H., Donahue C.H., Peterson C.G.: Fast, efficient error reconciliation for quantum cryptography. Phys. Rev. A 67(5), 052303 (2003)
Wang J., Zhang Q., Tang C.J.: Multiparty quantum secret sharing of secure direct communication using teleportation. Commun. Theor. Phys. 47(3), 454–458 (2007)
Dong L., Xiu X.M., Gao Y.J., Ren Y.P., Liu H.W.: Controlled three-party communication using GHZ-like state and imperfect Bell-state measurement. Opt. Commun. 284(3), 905–908 (2011)
Jennewein T., Simon C., Weihs G., Weinfurter H., Zeilinger A.: Quantum cryptography with entangled photons. Phys. Rev. Lett. 84(20), 4729–4732 (2000)
Hughes R.J., Nordholt J.E., Derkacs D., Peterson C.G.: Practical free-space quantum key distribution over 10 km in daylight and at night. New. J. Phys. 4, 43.1–43.14 (2002)
Gobby C., Yuan Z.L., Shields A.J.: Quantum key distribution over 122 km of standard telecom fiber. Appl. Phys. Lett. 84(19), 3762–3764 (2004)
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Tseng, HY., Lin, J. & Hwang, T. New quantum private comparison protocol using EPR pairs. Quantum Inf Process 11, 373–384 (2012). https://doi.org/10.1007/s11128-011-0251-0
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11128-011-0251-0