Abstract
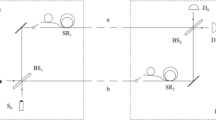
As is known, quantum key distribution could achieve information-theoretical security under several basic requirements, one of which is reliable identity authentications between the participants. Compared with classical identity authentication, quantum identity authentication (QIA) is considered to be more secure and more efficient to combine with quantum key distribution (QKD), and therefore, more and more scholars are involved in the study of QIA. During the last 3 decades, various types of QKD protocols have been proposed utilizing different kinds of quantum technologies. One of the most special QKD protocols is the orthogonal-state-encoding QKD protocol proposed by Goldenberg and Vaidman (Phys Rev Lett 75:1239–1243, 1995), which is usually called GV95 protocol. Almost all of the QKD protocols employ nonorthogonal states to prevent and detect eavesdropping, and the most famous exception is GV95. In this paper, we present a QIA protocol based on the GV95 technology, which can be performed in a revised circuit of the GV95 protocol. And we also analyze the security of both Alice’s and Bob’s identities.





Similar content being viewed by others
References
Bennett, C.H., Brassard, G.: Quantum cryptography: public key distribution and coin tossing. In: Proceedings of the IEEE International Conference on Computers, Systems, and Signal Processing, pp. 175–179. IEEE, New York (1984)
Ekert, A.K.: Quantum cryptography based on Bell theorem. Phys. Rev. Lett. 67, 661–663 (1991)
Bennett, C.H.: Quantum cryptography using any two nonorthogonal states. Phys. Rev. Lett. 68, 3121–3124 (1992)
Goldenberg, L., Vaidman, L.: Quantum cryptography based on orthogonal states. Phys. Rev. Lett. 75, 1239–1243 (1995)
Sun, Y., Wen, Q.-Y., Gao, F., Zhu, F.-C.: Robust variations of the Bennett–Brassard 1984 protocol against collective noise. Phys. Rev. A 80, 032321 (2009)
Song, T.-T., Wen, Q.-Y., Guo, F.-Z., Tan, X.-Q.: Finite-key analysis for measurement-device independent quantum key distribution. Phys. Rev. A 86, 022332 (2012)
Lin, S., Guo, G.-D., et al.: Quantum key distribution: defeating collective noise without reducing efficiency. Quantum Inf. Comput. 14, 845–856 (2014)
Li, Y.-B.: Analysis of counterfactual quantum key distribution using error correcting theory. Quantum Inf. Process. 13, 2325–2342 (2014)
Cleve, R., Gottesman, D., Lo, H.K.: How to share a quantum secret. Phys. Rev. Lett. 83, 648–651 (1999)
Hillery, M., Buzek, V., Berthiaume, A.: Quantum secret sharing. Phys. Rev. A 59, 1824–1829 (1999)
Yang, Y.-G., Wen, Q.-Y., Zhang, X.: Multiparty simultaneous quantum identity authentication with secret sharing. Sci. China Phys. Mech. Astron. 51, 321–327 (2008)
Qin, S.-J., Gao, F., Wen, Q.-Y., Zhu, F.-C.: Security of quantum secret sharing with two-particle entanglement against individual attacks. Quantum Inf. Comput. 9, 0765–0772 (2009)
Lin, S., Wen, Q.-Y., Qin, S.-J., et al.: Multiparty quantum secret sharing with collective eavesdropping-check. Opt. Commun. 282, 4455–4459 (2009)
Wang, T.-Y., Wen, Q.-Y.: Security of a kind of quantum secret sharing with single photons. Quantum Inf. Comput. 11, 0434–0443 (2011)
Long, G.-L., Liu, X.: Theoretically efficient high-capacity quantum key distribution scheme. Phys. Rev. A 65, 032302 (2002)
Deng, F.G., Long, G.L.: Controlled order rearrangement encryption for quantum key distribution. Phys. Rev. A 68, 042315 (2003)
Bostrom, K., Felbinger, T.: Deterministic secure direct communication using entanglement. Phys. Rev. Lett. 89, 187902 (2002)
Lin, S., Wen, Q.-Y., Zhu, F.-C.: Quantum secure direct communication with x-type entangled states. Phys. Rev. A 78, 064304 (2008)
Gao, F., Qin, S.-J., Wen, Q.-Y., Zhu, F.-C.: Cryptanalysis of multiparty controlled quantum secure direct communication using Greenberger–Horne–Zeilinger state. Opt. Commun. 283, 192 (2010)
Huang, W., Wen, Q.-Y., Jia, H.-Y., Qin, S.-J., Gao, F.: Fault tolerant quantum secure direct communication with quantum encryption against collective noise. Chin. Phys. B 21(10), 100308 (2012)
Giovannetti, V., Lloyd, S., Maccone, L.: Quantum private queries. Phys. Rev. Lett. 100, 230502 (2008)
Jakobi, M., Simon, C., Gisin, N., et al.: Practical private database queries based on a quantum-key-distribution protocol. Phys. Rev. A 83, 022301 (2011)
Gao, F., Liu, B., Huang, W., Wen, Q.Y.: Postprocessing of the oblivious key in quantum private query. IEEE J. Sel. Top. Quantum 21(3), 6600111 (2015)
Liu, B., Gao, F., Huang, W., et al.: QKD-based quantum private query without a failure probability. Sci. China Phys. Mech. Astron. 58, 100301 (2015)
Wei, C.-Y., Cai, X.-Q., Liu, B., Wang, T.-Y., Gao, F.: A generic construction of quantum-oblivious-transfer-based private query with ideal database security and zero failure. IEEE Trans. Comput. 67(1), 2–8 (2018)
Wegman, M.N., Carter, J.L.: New hash functions and their use in authentication and set equality. J. Comput. Syst. Sci. 22, 265 (1981)
Dusek, M., Haderka, O., Hendrych, M., Myska, R.: Quantum identification system. Phys. Rev. A 60, 149–156 (1999)
Curty, M., Santos, D.J.: Quantum authentication of classical messages. Phys. Rev. A 64, 062309 (2001)
Zhang, Z.-S., Zeng, G.-H., Zhou, N.-R., Xiong, J.: Quantum identity authentication based on ping–pong technique for photons. Phys. Lett. A 356, 199–205 (2006)
Shi, B.-S., Li, J., Liu, J.-M., Fan, X.-F., Guo, G.-C.: Quantum key distribution and quantum authentication based on entangled state. Phys. Lett. A 281, 83–87 (2001)
Yuan, H., Liu, Y.-M., Pan, G.-Z., Zhang, G., et al.: Quantum identity authentication based on ping–pong technique without entanglements. Quantum Inf. Process. 13, 2535–2549 (2014)
Ma, H.-X., Huang, P., Bao, W.-S., et al.: Continuous-variable quantum identity authentication based on quantum teleportation. Quantum Inf. Process. 15, 2605–2620 (2016)
Liao, L.-X., Peng, X.-Q., Shi, J.-J., et al.: Graph state-based quantum authentication scheme. Int. J. Mod. Phys. B 31, 1750067 (2017)
Hong, C.-H., Heo, J., Jang, J.-G.: Quantum identity authentication with single photon. Quantum Inf. Process. 16, UNSP 236 (2017)
Ljunggren, D., Bourennane, M., Karlsson, A.: Authority-based user authentication in quantum key distribution. Phys. Rev. A 62, 022305 (2000)
Wang, J., Zhang, Q., Tang, C.-J.: Multiparty simultaneous quantum identity authentication based on entanglement swapping. Chin. Phys. Lett. 23, 2360–2363 (2006)
Niu, P.-H., Yuan, C., Li, Chong: Quantum authentication scheme based on entanglement swapping. Int. J. Theor. Phys. 55, 302–312 (2016)
Xu, S.-W., Sun, Y., Lin, S.: Quantum private query based on single-photon interference. Quantum Inf. Process. 15, 3301–3310 (2016)
Shimizu, K., Imoto, N.: Single-photon-interference communication equivalent to Bell-state-basis cryptographic quantum communication. Phys. Rev. A 62, 054303 (2000)
Liu, B., Xiao, D., Huang, W., et al.: Quantum private comparison employing single-photon interference. 16, UNSP 180 (2017)
Barnett, S.M., Croke, S.: Quantum state discrimination. Adv. Opt. Photonics 1, 238–278 (2009)
Acknowledgements
This work is supported by National Natural Science Foundation of China (Grant Nos. 61702061, 61702469, 61771439, 61501414), China Postdoctoral Science Foundation Funded Project (Grant No. 2017M612912), Chongqing Postdoctoral Science Foundation funded project (Grant No. Xm2017041), Fundamental Research Funds for the Central Universities (Grant Nos. 106112016CDJXY180001, 2018CDJSK04XK09), National Cryptography Development Fund (Grant No. MMJJ20170120), Sichuan Youth Science and Technology Foundation (Grant No. 2017JQ0045) and Natural Science Foundation Project of CQ (Grant No. cstc2017rgzn-zdyfX0042).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Liu, B., Gao, Z., Xiao, D. et al. Quantum identity authentication in the orthogonal-state-encoding QKD system. Quantum Inf Process 18, 137 (2019). https://doi.org/10.1007/s11128-019-2255-0
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-019-2255-0