Abstract
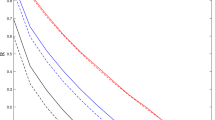
The finite-key security of the standard three-intensity decoy-state quantum key distribution (QKD) protocol in the presence of information leakage has been analyzed (Wang et al. in New J Phys 20:083027, 2018). On the other hand, the 1-decoy state QKD protocol has been proved to be able to achieve higher secret key rate than the three-intensity decoy-state QKD protocol in the finite-key regime by using only two different intensity settings (Davide et al. in Appl Phys Lett 112:171104, 2018). In this work, we analyze the finite-key security of the 1-decoy state QKD protocol with a leaky intensity modulator, which is used to generate the decoy state. In particular, we simulate the secret key rate under three practical cases of Trojan-horse attacks. Our simulation results demonstrate that the 1-decoy state QKD protocol can be secure over long distances within a reasonable time frame given that the intensity modulator is sufficiently isolated. By comparing the simulation results to those presented in Wang et al. (2018), we find that, as expected, the 1-decoy state QKD protocol is more robust against information leakage from the intensity modulator for all achievable distances.






Similar content being viewed by others
References
Bennett, C.H., Brassard, G.: Quantum cryptography: public key distribution and coin tossing. In: International Conference on Computer System and Signal Processing, pp. 175–179. IEEE (1984)
Scarani, V., Bechmann-Pasquinucci, H., Cerf, N.J., Dušek, M., Lütkenhaus, N., Peev, M.: The security of practical quantum key distribution. Rev. Mod. Phys. 81, 1301 (2009)
Lo, H.-K., Curty, M., Tamaki, K.: Secure quantum key distribution. Nat. Photonics 8, 595 (2014)
Liao, S.-K., et al.: Satellite-to-ground quantum key distribution. Nature 549, 43 (2017)
Lucamarini, M., Choi, I., Ward, M.B., Dynes, J.F., Yuan, Z., Shields, A.J.: Practical security bounds against the Trojan-horse attack in quantum key distribution. Phys. Rev. X 5, 031030 (2015)
Tamaki, K., Curty, M., Lucamarini, M.: Decoy-state quantum key distribution with a leaky source. New J. Phys. 18, 065008 (2016)
Wang, W., Tamaki, K., Curty, M.: Finite-key security analysis for quantum key distribution with leaky sources. New J. Phys. 20, 083027 (2018)
Hwang, W.-Y.: Quantum key distribution with high loss: toward global secure communication. Phys. Rev. Lett. 91, 057901 (2003)
Lo, H.-K., Ma, X., Chen, K.: Decoy state quantum key distribution. Phys. Rev. Lett. 94, 230504 (2005)
Wang, X.-B.: Beating the photon-number-splitting attack in practical quantum cryptography. Phys. Rev. Lett. 94, 230503 (2005)
Zhao, Y., Qi, B., Ma, X., Lo, H.-K., Qian, L.: Experimental quantum key distribution with decoy states. Phys. Rev. Lett. 96, 070502 (2006)
Peng, C.-Z., Zhang, J., Yang, D., Gao, W.-B., Ma, H.-X., Yin, H., Zeng, H.-P., Yang, T., Wang, X.-B., Pan, J.-W.: Experimental long-distance decoy-state quantum key distribution based on polarization encoding. Phys. Rev. Lett. 98, 010505 (2007)
Schmitt-Manderbach, T., et al.: Experimental demonstration of free-space decoy-state quantum key distribution over 144 km. Phys. Rev. Lett. 98, 010504 (2007)
Yuan, Z., Sharpe, A., Shields, A.: Unconditionally secure one-way quantum key distribution using decoy pulses. Appl. Phys. Lett. 90, 011118 (2007)
Rosenberg, D., Harrington, J.W., Rice, P.R., Hiskett, P.A., Peterson, C.G., Hughes, R.J., Lita, A.E., Nam, S.W., Nordholt, J.E.: Long-distance decoy-state quantum key distribution in optical fiber. Phys. Rev. Lett. 98, 010503 (2007)
Liu, Y., et al.: Decoy-state quantum key distribution with polarized photons over 200 km. Opt. Express 18, 8587 (2010)
Fröhlich, B., Lucamarini, M., Dynes, J.F., Comandar, L.C., Tam, W.W.-S., Plews, A., Sharpe, A.W., Yuan, Z., Shields, A.J.: Long-distance quantum key distribution secure against coherent attacks. Optica 4, 163 (2017)
Davide, R., Baron, A., Grünenfelder, F., Martin, A., Zbinden, H.: Finite-key analysis for the 1-decoy state QKD protocol. Appl. Phys. Lett. 112, 171104 (2018)
Mizutani, A., Curty, M., Lim, C.C.W., Imoto, N., Tamaki, K.: Finite-key security analysis of quantum key distribution with imperfect light sources. New J. Phys. 17, 093011 (2015)
Nielsen, M.A., Chuang, I.L.: Quantum Information and Quantum Computation. Cambridge University Press, Cambridge (2000)
Azuma, K.: Weighted sums of certain dependent random variables. Tohoku Math. J. 19, 357 (1967)
Lim, C.C.W., Curty, M., Walenta, N., Xu, F., Zbinden, H.: Concise security bounds for practical decoy-state quantum key distribution. Phys. Rev. A 89, 022307 (2014)
Serfling, R.J.: Probability inequalities for the sum in sampling without replacement. Ann. Stat. 2, 39 (1974)
Tomamichel, M., Lim, C.C.W., Gisin, N., Renner, R.: Tight finite-key analysis for quantum cryptography. Nat. Commun. 3, 634 (2012)
Curty, M., Xu, F., Cui, W., Lim, C.C.W., Tamaki, K., Lo, H.-K.: Finite-key analysis for measurement-device-independent quantum key distribution. Nat. Commun. 5, 3732 (2014)
Acknowledgements
This work was supported by the National Natural Science Foundation of China (Grant Nos. 61701539, 61972413, 61901525) and the National Cryptography Development Fund (mmjj20180107, mmjj20180212). WLW and XDM contributed equally to this work.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Wang, W., Meng, X., Fei, Y. et al. Finite-key security analysis of the 1-decoy state QKD protocol with a leaky intensity modulator. Quantum Inf Process 19, 196 (2020). https://doi.org/10.1007/s11128-020-02694-6
Published:
DOI: https://doi.org/10.1007/s11128-020-02694-6