Abstract
Compared with symmetric Gaussian-modulated coherent state protocol, the unidimensional continuous-variable quantum key distribution (UCVQKD) only modulates one of the quadratures in phase space of coherent state, thereby simplifying its implementation. Although UCVQKD does reduce the system’s complexity, its performance is reduced. In this work, we suggest an improved approach for UCVQKD using zero-photon quantum catalysis (ZPQC) technology. By taking advantage of this non-Gaussian operation, both secret key rate and maximal transmission distance of UCVQKD can be enhanced. Moreover, compared with another well-studied non-Gaussian operation, i.e., photon subtraction, ZPQC has higher success possibility, so that it would be beneficial for improving the amount of information acquired by legitimate users. Numerical simulation shows that the performance of UCVQKD can be improved by properly applying ZPQC. In particular, we find out that the performance of ZPQC-based UCVQKD outperforms that of photon subtraction-based UCVQKD, thereby providing an alternative way to better improve UCVQKD system. Furthermore, by taking finite-size effect into account, we derive more practical secure bound of ZPQC-based UCVQKD.












Similar content being viewed by others
References
Grosshans, F., Grangier, P.: Continuous variable quantum cryptography using coherent states. Phys. Rev. Lett. 88, 057902 (2002)
Grosshans, F., Van Assche, G., Wenger, J., Brouri, R., Cerf, N.J., Grangier, P.: Quantum key distribution using Gaussian-modulated coherent states. Nature 421, 238–241 (2003)
Weedbrook, C., Lance, A.M., Bowen, W.P., Symul, T., Ralph, T.C., Lam, P.K.: Quantum cryptography without switching. Phys. Rev. Lett. 93, 170504 (2004)
Lo, H.K., Curty, M., Tamaki, K.: Secure quantum key distribution. Nat. Photon. 8(8), 595604 (2014)
Liao, Q., Xiao, G., Xu, C.G., Xu, Y., Guo, Y.: Discretely modulated continuous-variable quantum key distribution with an untrusted entanglement source. Phys. Rev. A 102(3), 032604 (2020)
Braunstein, S.L., Van Loock, P.: Quantum information with continuous variables. Rev. Mod. Phys. 77, 513577 (2005)
Laudenbach, F., Pacher, C., Fung, C.H.F., Poppe, A., Peev, M., Schrenk, B., Hentschel, M., Walther, P., Hübel, H.: Continuous-variable quantum key distribution with Gaussian modulation: the theory of practical implementations. Adv. Quant. Technol. 1, 1800011 (2018)
Liao, Q., Xiao, G., Zhong, H., Guo, Y.: Multi-label learning for improving discretely-modulated continuous-variable quantum key distribution. New J. Phys. 22(8), 083086 (2020)
Gerhardt, I., Liu, Q., Lamas-Linares, A., Skaar, J., Kurtsiefer, C., Makarov, V.: Full-field implementation of a perfect eavesdropper on a quantum cryptography system. Nat. Commun. 2, 349 (2011)
Liao, Q., Guo, Y., Xie, C., Huang, D., Huang, P., Zeng, G.: Composable security of unidimensional continuous-variable quantum key distribution. Quant. Inf. Process. 17(5), 113 (2018)
Guo, Y., Liao, Q., Wang, Y., Huang, D., Huang, P., Zeng, G.: Performance improvement of continuous-variable quantum key distribution with an entangled source in the middle via photon subtraction. Phys. Rev. A 95, 032304 (2017)
Wu, X.D., Wang, Y.J., Zhong, H., Liao, Q., Guo, Y.: Plug-and-play dual-phase-modulated continuous-variable quantum key distribution with photon subtraction. Front. Phys. 14(4), 41501 (2019)
Ghalaii, M., Ottaviani, C., Kumar, R., Pirnadola, S., Razavi, M.: Long-distance continuous-variable quantum key distribution with quantum scissors. IEEE J. Select. Top. Quant. Electron. (2020)
Wang, P., Wang, X., Li, Y.: Security analysis of unidimensional continuous-variable quantum key distribution using uncertainty relations. Entropy 20(3), 157 (2018)
Ye, W., Zhong, H., Wu, X., Hu, L., Guo, Y.: Continuous-variable measurement-device independent quantum key distribution via quantum catalysis. Quant. Inf. Process. 19(10), 1–22 (2020)
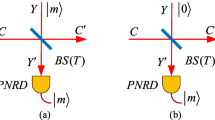
Zhong, H., Guo, Y., Mao, Y., Ye, W., Huang, D.: Virtual zero-photon catalysis for improving continuous-variable quantum key distribution via Gaussian post-selection. Sci. Rep. 10(1), 1–12 (2020)
Lo, H.K., Chau, H.F., Ardeli, M.: Efficient quantum key distribution scheme and a proof of its unconditional security. J. Cryptol. 18, 133 (2005)
Grosshans, F., Grangier, Ph., Proceedings of the 6th International Conference on Quantum Communications Measurement and Computing, pp. 155–160 (2009)
Guo, Y., Ye, W., Zhong, H., Liao, Q.: Continuous-variable quantum key distribution with non-gaussian quantum catalysis. Phys. Rev. A 99, 032327 (2019)
Zhou, W., Ye, W., Liu, L., Hu, Y., Liu, S.: Entanglement improvement of entanglement improvement of entangled coherent state via multiphoton catalysis. Laser Phys. Lett. 15, 065203 (2018)
Hu, L., Wu, J., Liao, Z., Zubairy, M.S.: Multiphoton catalysis with coherent state input: Nonclassicality and decoherence. J. Phys. B: At. Mol. Phys. 49, 175504 (2016)
Usenko, V.C.: Unidimensional continuous-variable quantum key distribution using squeezed states. Phys. Rev. A 98, 032321 (2018)
Leverrier, A., Grosshans, F., Grangier, P.: Finite-size analysis of a continuous-variable quantum key distribution. Phys. Rev. A 81, 062343 (2010)
Usenko, V.C., Grosshans, F.: Unidimensional continuous-variable quantum key distribution. Phys. Rev. A 92(6), 062337 (2015)
Acknowledgements
This work is supported by the National Natural Science Foundation of China (Grants No. 61871407), the Hunan Provincial Natural Science Foundation of China (Grant No. 2020JJ5088) and the Fundamental Research Funds for the Central Universities (Grant No. 531118010371).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendices
A Derivation of covariance matrixes
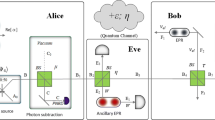
To acquire the analytical expression of security key rate, we propose the covariance matrix \(\varGamma _{AB_3}\) of the inequivalent EB-based version of our scheme. Firstly, the covariance matrix of the EPR state that Alice prepared can be given by the following expression
where \({\mathbb {I}}=diag(1, 1)\) and \(\sigma _z=diag(1, -1)\). After applying ZPQC operation on mode B, the covariance matrix of the yield state \(\varGamma _{AB_1}\) can be expressed as
where
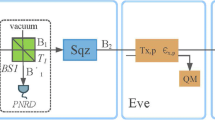
As stated above, to modulate a single quadrature x, the coherent states should be squeezed after Alice performs a heterodyne measurement on the mode A, and finally, the coherent state is sent to the trusted side, Bob. According to the EPR scheme shown in Fig. 3, the coherent states along the x quadrature can be replaced by the variance \(V_M=V_A^2-1\) [24] through unidimensional modulation.
As for unidimensional protocol, the scheme can be built by two-mode squeezed vacuum state of variance \(V_A\) and squeeze one of the coherent state modes with the squeezing parameter \(-\log {\sqrt{V_A}}\), resulting in the following matrix:
with
As stated above, mode A is measures by Alice using a homodyne detector and mode B is squeezed on the squeezer and sent to the channel. As the states travel through the noisy and lossy public channel, the covariance matrix is transferred to according to the channel parameters; thus, there is no modulation in the p quadrature after being squeezed by squeezer, which is defined as the ZPQC-based unidimensional modulation. Thus, the covariance matrix is redefined by the variance \(V_M\) in the unidimensional modulation [24]. The covariance matrix is rewritten as follows
1.1 A.1 Asymptotic case
After transmission through the channel characterized by transmittance efficiency \(T_C\) and excess noise \(\epsilon _{x,y}\), the covariance matrix is written as follows
where \(\chi _\mathrm{line}=\frac{1}{T_C}-1+\xi \), \(C_2=\sqrt{T_C}C_1\).
In the EB scheme, the detector can be modeled as a beam splitter with transmission efficiency \(\eta \), the electric noise \(\xi _\mathrm{el}\) can be modeled by the state \(\rho _{AB_2}\), and then, the covariance matrix \(\gamma _{AB_2}\) characterizing the state \(\rho _{AB}\) through the beam splitter is given by
where \(\chi _\mathrm{tot}=\chi _\mathrm{line}+\chi _\mathrm{det}\), \(\chi _\mathrm{det}=(1-\eta +\xi _\mathrm{el})/\eta \) for homodyne detection.
1.2 A.2 Finite-size scenario
Following the derived results from [23], the covariance matrix of the state \(\rho _{AB_3}\) can be represented as follows in the finite-size scenario
Here, \(t_m\) and \(\sigma _m\) are the minimally estimated value of the total transmission and the maximally estimated value of the total noise. For homodyne detection, these two parameters are presented as follows
where \(\sigma =\eta T_c(\chi _\mathrm{line}+\chi _\mathrm{det}/T_c+1)\), \(z_{\epsilon _{EP/2}}\) is such that \([1-erf(z_{\epsilon _{EP/2}}/\sqrt{2})]/2=\epsilon /2\), \(\epsilon _{EP}\) is the failure probability of the parameter estimation and erf represents the error function
B Calculation of the secret key rate
In this section, the secret key rate analysis is mainly carried out under Gaussian collective attacks, simply because they are proved to be optimal in asymptotic cases.
To obtain the lower bound of the secret key rate, the covariance matrix in the asymptotic framework thus should be derived. The secret key rate in the case of asymptotic security reads
where \(\beta \) is the reconciliation efficiency, \(I_{AB}\) refers to the mutual information shared by both Alice and Bob, and \(\chi _{BE}\) represents the Holevo bound between Bob and Eve for reverse reconciliation. The mutual information can be derived by the following expression
Thus, it can be derived by the following expression under the asymptotic cases
where \(V_A\) is the amplitude quadrature variance for Alice, which is the first element of matrix \(\gamma _A\) describing mode A, while the first diagonal element of conditional matrix \(\gamma _{A|B}\), and \(V_{A|B}\) which represents conditional variance in amplitude quadrature, is given by
where MP presents the Moore–Penrose matrix inverse; \(\gamma _A\), \(\gamma _B\) and \(\sigma _{AB}\) refer to submatrices of the covariance matrix \(\gamma _{AB}\) by decomposition, namely
where
and
Lossy information available for Eve can be obtained by
where \(S(\rho )\) is the von Neumann entropy of the quantum state \(\rho \). The calculation of symplectic eigenvalues of covariance matrix \(\gamma \) is applied to evaluate entropy for an n-mode Gaussian state describing \(\rho \) as follows
where
the symplectic eigenvalues \(\lambda _1\), \(\lambda _2\) are given by the square roots of equation using the following equation
Therefore, \(\lambda _{1,2}^2\) can be calculated by the equation
where
namely
where \(\gamma _A\), \(\gamma _B\) and \(\sigma _{AB}\) have been given above.
Since \(S(\rho _E^{x_B})=G(\frac{\lambda _3-1}{2})\), we can calculate S(B|A) using
Thus, \(\lambda _3\) is calculated by
Besides, in the finite-size scenario, the secret key rate is given by [23]
where N refers to the total exchanged information, n is the data employed for generating low raw key (\(m=N-n\)) and \(\varDelta (n)\) is a parameter related to privacy amplification and is given by
where \({\overline{\epsilon }}\) is a smoothing parameter and \(\epsilon _{PA}\) represents the failure probability of the privacy amplification procedure. Similarly, the calculation of \(I_{AB}\) and \(\chi _{BE}\) is identical by replacing \(C_3\) and \(V_{B_3}\).
Rights and permissions
About this article
Cite this article
Hu, J., Liao, Q., Mao, Y. et al. Performance improvement of unidimensional continuous-variable quantum key distribution using zero-photon quantum catalysis. Quantum Inf Process 20, 31 (2021). https://doi.org/10.1007/s11128-020-02973-2
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-020-02973-2