Abstract
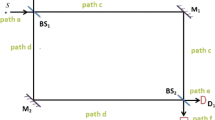
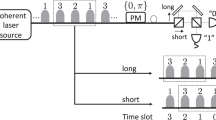
A protocol for secure key distribution using classical light is proposed. The method relies on white-light interferometric measurements by one of the communicating parties and the random choice of delays by the other party. In this way, securely shared random keys are created, thereby enabling secure data transmission. In contrast to quantum key distribution, only classical waves are used. Single photons (and the practical problems associated with them) are avoided. The security of the method cannot be proven at the moment but different attacks are described and briefly analyzed.
Similar content being viewed by others
References
Shannon CE (1949) Communication theory of secrecy systems. Bell Syst Tech J 28(4):656
Delfs H, Knebl H (2007) Introduction to cryptography: principles and applications. Springer, Berlin
Mermin ND (2007) Quantum computer science. Cambridge University Press, Cambridge
Haist T, Osten W (2009) Proposal for secure key distribution using classical optics. Lect Notes Comput Sci 5882:99–101
Bennett CH (1992) Quantum cryptography using any two nonorthogonal states. Phys Rev Lett 21:3121–3124
Ekert AK, Huttner B, Palma GM, Peres A (1994) Eavesdropping on quantum-cryptographical system. Phys Rev A 50:1047–1055
Huttner B, Imoto N, Gisin N, Mor T (1995) Quantum cryptography with coherent states. Phys Rev A 51:1863–1869
Hirano T, Yamanaka H, Asikaga M, Konishi T, Namiki R (2003) Quantum cryptography using pulsed homodyne detection. Phys Rev A 68:042331
Maurer EM, Wolf S (1999) Unconditionally secure key agreement and the intrinsic conditional information. IEEE Trans Inf Theory 45:499–514
Yuen HP, Kim AM (1998) Classical noise-based cryptography similar to two-state quantum cryptography. Phys Lett A 241:135–138
Liu S, Van Tilborg HCA, Van Dijk M (2003) A practical protocol for advantage distillation and information reconciliation. Design Codes Cryptogr 30:39–62
Watanabe Y (2007) Privacy amplification for quantum key distribution. J Phys A 40:F99–104
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Haist, T., Osten, W. White-light interferometric method for secure key distribution. J Supercomput 62, 656–662 (2012). https://doi.org/10.1007/s11227-010-0488-x
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11227-010-0488-x