Abstract
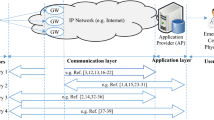
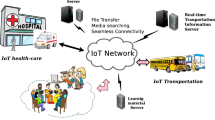
In this paper, we proposed an secure IoT framework to ensure an End-To-End security from an IoT application to IoT devices. The proposed IoT framework consists of the IoT application, an IoT broker and the IoT devices. The IoT devices can be deployed along a board line or a boundary of the area of IoT broker. The IoT broker manages their own devices and aggregates their sensing data. The IoT application provides users with IoT services. To use the IoT services, it needs to access to sensing data. Especially, the case of real-time healthcare services should consider intermediate security issues because medical information of patients is one of very sensitive privacy information. However, most of IoT protocols such as CoAP and MQTT have no concern about the End-To-End security, they only depended on the security of DTLS. Therefore, we proposed a new IoT framework to satisfy the End-To-End security feature under the CoAP communication. The proposed framework encrypts sensitive data by a symmetric encryption and an attribute-based encryption for efficiencies of communication and computation costs. In addition, each IoT device has a unique identification used as one of their attributes. Consequently, although the IoT broker is one of the intermediate nodes, it decrypts and shows data only if it satisfies all attributes.


Similar content being viewed by others
Change history
05 December 2016
An erratum to this article has been published.
References
Bethencourt J, Sahai A, Waters B (2007) Ciphertext-policy attribute-based encryption. In: IEEE symposium on security and privacy, SP’07. IEEE, pp 321–334 (2007)
Chase M (2007) Multi-authority attribute based encryption. In: Theory of cryptography. Springer, pp 515–534
Chuankun W (2010) A preliminary investigation on the security architecture of the internet of things [j]. Bull. Chin. Acad. Sci. 4:009
Cirani S, Picone M, Veltri L (2015) Mjcoap: an open-source lightweight java coap library for internet of things applications. In: Interoperability and open-source solutions for the internet of things. Springer, pp 118–133
Dierks T (2008) The transport layer security (tls) protocol version 1.2. Technical report, RFC 5246, July 2008
Gerdes S, Bergmann O, Bormann C (2014) Delegated coap authentication and authorization framework (dcaf). IETF draftgerdes-core-dcaf-authorize-02
Goyal V, Jain A, Pandey O, Sahai A (2008) Bounded ciphertext policy attribute based encryption. In: Automata, languages and programming. Springer, pp 579–591
Goyal V, Pandey O, Sahai A, Waters B (2006) Attribute-based encryption for fine-grained access control of encrypted data. In: Proceedings of the 13th ACM conference on computer and communications security. ACM, pp 89–98
Heer T, Garcia-Morchon O, Hummen R, Keoh SL, Kumar SS, Wehrle K (2011) Security challenges in the ip-based internet of things. Wirel Pers Commun 61(3):527–542
Hunkeler U, Truong HL, Stanford-Clark A (2008) Mqtt-s—a publish/subscribe protocol for wireless sensor networks. In: 3rd international conference on communication systems software and middleware and workshops, 2008. comsware 2008. IEEE, pp 791–798
Liu Y, Hu W, Du J (2011) Network Information Security Architecture Based on Internet of Things. ZTE Technol J. 17(1):17–20
Khoo B (2011) Rfid as an enabler of the internet of things: issues of security and privacy. In: Internet of things (iThings/CPSCom), 2011 international conference on and 4th international conference on cyber, physical and social computing. IEEE, pp 709–712
Lee JY, Lin WC, Huang YH (2014) A lightweight authentication protocol for internet of things. In: 2014 international symposium on next-generation electronics (ISNE). IEEE, pp 1–2
Li X, Xuan Z, Wen L (2011) Research on the architecture of trusted security system based on the internet of things. In: 2011 international conference on Intelligent computation technology and automation (ICICTA), vol. 2. IEEE, pp 1172–1175
Banks A, Gupta R (2014) MQTT version 3.1.1. OASIS standard
McGrew D, Bailey D (2012) Aes-ccm cipher suites for transport layer security (tls). Technical report, RFC 6655, Aug 2012
McGrew D, Rescorla E (2010) Datagram transport layer security (dtls) extension to establish keys for secure real-time transport protocol (srtp). Technical report, RFC 5764, May 2010
Medaglia CM, Serbanati A (2010) An overview of privacy and security issues in the internet of things. In: The internet of things. Springer, pp 389–395
Ning H, Liu H et al (2012) Cyber-physical-social based security architecture for future internet of things. Adv Internet Things 2(01):1
Pesonen LI, Eyers DM, Bacon J (2007) Encryption-enforced access control in dynamic multi-domain publish/subscribe networks. In: Proceedings of the 2007 inaugural international conference on distributed event-based systems. ACM, pp 104–115
Raza S, Voigt T, Jutvik V (2012) Lightweight ikev2: a key management solution for both the compressed ipsec and the ieee 802.15. 4 security. In: Proceedings of the IETF workshop on smart object security
Riahi A, Challal Y, Natalizio E, Chtourou Z, Bouabdallah A (2013) A systemic approach for iot security. In: 2013 IEEE international conference on distributed computing in sensor systems (DCOSS). IEEE, pp 351–355
Shelby Z, Hartke K, Bormann C (2014) The constrained application protocol (coap). Technical report, RFC 7252, June 2014
Wang G, Liu Q, Wu J (2010) Hierarchical attribute-based encryption for fine-grained access control in cloud storage services. In: Proceedings of the 17th ACM conference on computer and communications security. ACM, pp 735–737
Waters B (2011) Ciphertext-policy attribute-based encryption: an expressive, efficient, and provably secure realization. In: Public key cryptography-PKC 2011. Springer, pp 53–70
Weber RH (2010) Internet of things-new security and privacy challenges. Comput Law Secur Rev 26(1):23–30
Wei R (2012) A study of security architecture and technical approaches in internet of things. Netinfo Secur 5:025
Zhao K, Ge L (2013) A survey on the internet of things security. In: 2013 9th international conference on computational intelligence and security (CIS). IEEE, pp 663–667
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Choi, J., In, Y., Park, C. et al. Secure IoT framework and 2D architecture for End-To-End security. J Supercomput 74, 3521–3535 (2018). https://doi.org/10.1007/s11227-016-1684-0
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11227-016-1684-0