Abstract
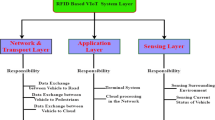
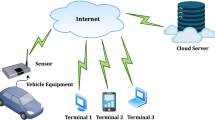
The new era of the Internet of Things is driving the evolution of conventional vehicle ad hoc networks into the Internet of vehicles (IoV). Radio frequency identification (RFID) is a reliable and advanced instrument used for automated data collection, processing and tracking, which is widely used in IoV. One of the important features of an RFID system is its ability to search for a particular tag among a group of tags. Since the RFID tags used in vehicles are commonly resource-constrained, the purpose is to propose a lightweight tag searching protocol that meets the security requirements while at the same time it is respecting the requirements for efficient implementation. In this regard, a lightweight tag search protocol, which is based on permutation matrices, has recently been proposed by Fan et al. and claimed to be secure against various attacks. In this paper, we analyze the security of this protocol and show that this scheme is vulnerable to de-synchronization and disclosure attacks. The latter attack can disclose all the secret information stored in a tag such as the identity, the shared secret key and the two secret permutation matrices that are used as encryption functions. To address these vulnerabilities, we propose an improved lightweight tag search protocol based on maximum distance separable matrices. As a result of security analysis, we can see that the improved scheme is secure against passive and active attacks, including disclosure and de-synchronization attack. Finally, we implement the improved protocol in ISE 14.6 environment for Virtex-7 FPGAs and compare the performance with some related protocols. The implementation results show that the improved scheme is particularly well suited for use in RFID systems.




Similar content being viewed by others
References
Aadil F, Ahsan W, Rehman Z, Shah PA, Rho S, Mehmood I (2018) Clustering algorithm for internet of vehicles (IOV) based on dragonfly optimizer (CAVDO). J Supercomput 74(9):4542–4567
Abbasian A, Safkhani M (2020) CNCAA: a new anti-collision algorithm using both collided and non-collided parts of information. Comput Netw 172:107159
CAESAR (2013) CAESAR: Competition for Authenticated Encryption: Security, Applicability, and Robustness. http://competitions.cr.yp.to/caesar.html. Accessed 5 Apr 2020
Chen M, Luo W, Mo Z, Chen S, Fang Y (2013) An efficient tag search protocol in large-scale RFID systems. In: 2013 Proceedings IEEE INFOCOM, pp 899–907
Chen M, Luo W, Mo Z, Chen S, Fang Y (2016) An efficient tag search protocol in large-scale RFID systems with noisy channel. IEEE/ACM Trans Netw 24(2):703–716
Chun JY, Hwang JY, Lee DH (2011) RFID tag search protocol preserving privacy of mobile reader holders. IEICE Electron Express 8(2):50–56
Daemen J (1995) Cipher and hash function design, strategies based on linear and differential cryptanalysis. PhD thesis, Katholieke Universiteit Leuven
Doss R, Trujillo-Rasua R, Piramuthu S (2020) Secure attribute-based search in RFID-based inventory control systems. Decis Support Syst 132:113270
Eslamnezhad Namin M, Hosseinzadeh M, Bagheri N, Khademzadeh A (2018) RSPAE: RFID search protocol based on authenticated encryption. J Electr Comput Eng Innov 6(2):179–192
Eslamnezhad Namin M, Hosseinzadeh M, Bagheri N, Khademzadeh A (2018) A secure search protocol for lightweight and low-cost RFID systems. Telecommun Syst 67(4):539–552
Fan K, Kang J, Zhu S, Li H, Yang Y (2019) Permutation matrix encryption based ultralightweight secure RFID scheme in internet of vehicles. Sensors 19(1):152
Hoque ME, Rahman F, Ahamed SI, Park JH (2010) Enhancing privacy and security of RFID system with serverless authentication and search protocols in pervasive environments. Wirel Pers Commun 55(1):65–79
Jannati H, Bahrak B (2016) Security analysis of an rfid tag search protocol. Inf Process Lett 116(10):618–622
Kim Z, Kim J, Kim K, Choi I, Shon T (2011) Untraceable and serverless RFID authentication and search protocols. In: 2011 IEEE Ninth International Symposium on Parallel and Distributed Processing with Applications Workshops, pp 278–283
Kulseng L, Yu Z, Wei Y, Guan Y (2009) Lightweight secure search protocols for low-cost RFID systems. In: 2009 29th IEEE International Conference on Distributed Computing Systems, pp 40–48
Kwon D, Kim J, Park S, Sung SH, Sohn Y, Song JH, Yeom Y, Yoon E-J, Lee S, Lee J, Chee S, Han D, Hong J (2004) New block cipher: Aria. In: Lim J-I, Lee D-H (eds) Information Security and Cryptology (ICISC 2003). Springer, Berlin, pp 432–445
Liu C-G, Liu I-H, Lin C-D, Li J-S (2019) A novel tag searching protocol with time efficiency and searching accuracy in RFID systems. Comput Netw 150:201–216
Liu X, Li K, Liu AX, Guo S, Shahzad M, Wang AL, Wu J (2017) Multi-category RFID estimation. IEEE/ACM Trans Netw 25(1):264–277
Liu X, Xiao B, Zhang S, Bu K, Chan A (2015) Step: a time-efficient tag searching protocol in large RFID systems. IEEE Trans Comput 64(11):3265–3277
Lv C, Li H, Ma J, Niu B (2012) Vulnerability analysis of lightweight secure search protocols for low-cost RFID systems. Int J Radio Freq Identif Technol Appl 4(1):3
MacWilliams FJ, Sloane NJA (1978) The theory of error correcting codes. Mathematical library. Elsevier, Amsterdam
Mtita C, Laurent M, Delort J (2016) Efficient serverless radio-frequency identification mutual authentication and secure tag search protocols with untrusted readers. IET Inf Secur 10(5):262–271
Mtita C, Laurent M, Sauveron D, Akram RN, Markantonakis K, Chaumette S (2017) Serverless protocols for inventory and tracking with a UAV. CoRR, arXiv:1708.05417
NIST (2001) Advanced encryption standard. National Institute of Standards and Technology, FIPS 197
Piramuthu S (2012) Vulnerabilities of RFID protocols proposed in ISF. Inf Syst Front 14(3):647–651
Safkhani M (2018) Cryptanalysis of R2AP an ultralightweight authentication protocol for RFID. J Electr Comput Eng Innov 6(1):107–114
Safkhani M, Peris-Lopez P, Bagheri N, Naderi M, Castro JCH (2013) On the security of tan et al. serverless RFID authentication and search protocols. In: Hoepman J, Verbauwhede I (eds) Radio Frequency Identification. Security and Privacy Issues—8th International Workshop (RFIDSec 2012), Nijmegen, The Netherlands, July 2–3, 2012, Revised Selected Papers, volume 7739 of Lecture Notes in Computer Science. Springer, Berlin, pp 1–19
Sundaresan S, Doss R, Piramuthu S, Zhou W (2015) Secure tag search in RFID systems using mobile readers. IEEE Trans Dependable Secure Comput 12(2):230–242
Sundaresan S, Doss R, Piramuthu S, Zhou W (2017) A secure search protocol for low cost passive RFID tags. Comput Netw 122:70–82
Tan CC, Sheng B, Li Q (2008) Secure and serverless rfid authentication and search protocols. IEEE Trans Wirel Commun 7(4):1400–1407
Wei C-H, Yang C-Y, Hwang M-S (2019) Cryptanalysis of the serverless RFID authentication and search protocols. In: Xhafa F, Patnaik S, Tavana M (eds) Advances in intelligent. Interactive systems and applications. Springer, Cham, pp 842–846
Won T Y, Chun JY, Lee DH (2008) Strong authentication protocol for secure RFID tag search without help of central database. In: 2008 IEEE/IFIP International Conference on Embedded and Ubiquitous Computing, vol 2, pp 153–158
Yoon E-J (2012) Cryptanalysis of an RFID tag search protocol preserving privacy of mobile reader. In: Park JJ, Zomaya A, Yeo S-S, Sahni S (eds) Network and parallel computing. Springer, Berlin, pp 575–580
Yu J, Gong W, Liu J, Chen L, Wang K (2019) On efficient tree-based tag search in large-scale RFID systems. IEEE/ACM Trans Netw 27(1):42–55
Zhang S, He X, Song H, Zhang D (2013) Time efficient tag searching in multiple reader RFID systems. In: 2013 IEEE International Conference on Green Computing and Communications and IEEE Internet of Things and IEEE Cyber, Physical and Social Computing, pp 481–488
Zheng Y, Li M (2013) Fast tag searching protocol for large-scale RFID systems. IEEE/ACM Trans Netw 21(3):924–934
Acknowledgements
The authors gratefully thank all the anonymous reviewers for their valuable comments which helped us to improve the presentation of the work significantly. This work was supported by Shahid Rajaee Teacher Training University.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Adeli, M., Bagheri, N. MDSbSP: a search protocol based on MDS codes for RFID-based Internet of vehicle. J Supercomput 77, 1094–1113 (2021). https://doi.org/10.1007/s11227-020-03302-1
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11227-020-03302-1