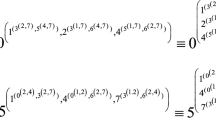Abstract
Recently, several researches have suggested an application of formal methods for identifying configuration errors, unveiling design problems and predicting network behavior. In this paper, we contribute to this research area by defining a method able to efficiently check reachability properties in dynamically routed networks. We define a notion of network state that captures different network conditions. Each network state represents a unique combination of link availability. The naive enumeration of network states leads quickly to intractability even for small networks as the number of possible combinations grows exponentially. Instead, we enumerate all available paths and, for each path, we search for state aggregation, in which this path is active.
Similar content being viewed by others
References
(2006). Ospf design guide. (Tech. rep.) Available at url: http://www.cisco.com/warp/public/104/1.pdf.
Acharya, S., Wang, J., Ge, Z., Znati, T., & Greenberg, A. (2006). Simulation study of firewalls to aid improved performance. In 39th annual, simulation symposium, 2006 (p. 8).
Bartal, Y., Mayer, A., Nissim, K., & Wool, A. (1999). Firmato: a novel firewall management toolkit. In IEEE symposium on security and privacy (pp. 17–31). citeseer.ist.psu.edu/article/bartal99firmato.html.
Bera, P., Ghosh, S., & Dasgupta, P. (2009). Formal analysis of security policy implementations in enterprise networks. International Journal of Computer Networks and Communications, 1(2), 56–73.
Bera, P., Ghosh, S., & Dasgupta, P. (2009). Formal verification of security policy implementations in enterprise networks. In ICISS ’09: Proceedings of the 5th international conference on information systems security (pp. 117–131). Berlin: Springer.
Christiansen, M., & Fleury, E. (2004). An interval decision diagram based firewall. In 3rd international conference on networking (ICN’04). Los Alamitos: IEEE Comput. Soc.
Hedrick, C. L. (1988). Routing information protocol. RFC 1058.
Gan, Q., & Helvik, B. (2006). Dependability modelling and analysis of networks as taking routing and traffic into account. In 2nd conference on next generation internet design and engineering, NGI ’06 (pp. 8–32).
Gouda, M., Liu, A. X., & Jafry, M. (2008). Verification of distributed firewalls. In Proceedings of the IEEE global communications conference (GLOBECOM), New Oreleans, Louisiana.
Guttman, J. D. (1997). Filtering postures: local enforcement for global policies. In Proceedings, 1997 IEEE symposium on security and privacy (pp. 120–129). Los Alamitos: IEEE Computer Society.
Guttman, J. D. (1997). Filtering postures: local enforcement for global policies. In IEEE symposium on security and privacy (pp. 120–129).
Doyle, J. (2006). CCIE professional development routing TCP/IP, vol. 1. Cisco Systems, Inc.
Jeffrey, A., & Samak, T. (2009). Model checking firewall policy configurations. In IEEE international workshop on policies for distributed systems and networks (pp. 60–67).
Liu, A. X. (2008). Formal verification of firewall policies. In Proceedings of the 2008 IEEE international conference on communications (ICC), Beijing, China.
Matoušek, P., Ráb, J., Ryšavý, O., & Švéda, M. (2008). A formal model for network-wide security analysis. In 15th IEEE symposium and workshop on ECBS.
Menth, M., Duelli, M., Martin, R., & Milbrandt, J. (2009). Resilience analysis of packet-switched communication networks. IEEE/ACM Transactions on Networking 17(6).
Mitre: Common vulnerabilities and exposures database. Available from http://cve.mitre.org/; accessed on Feb 2008.
Moy, J. (1998). OSPF Version 2. RFC 2328.
Pozo, S., Ceballos, R., & Gasca, R. (2008). Fast algorithms for consistency-based diagnosis of firewalls rule sets. In Proceedings of the 3rd international conference on availability, reliability and security (ARES).
Ritchey, R. W., & Ammann, P. (2000). Using model checking to analyze network vulnerabilities. In IEEE symposium on security and privacy, Washington, USA.
Rubin, F. (1978). Enumerating all simple paths in a graph. IEEE Transactions on Circuits and Systems, 25(8), 641–642.
Shahriari, H. R., Sadoddin, R., Jalili, R., Zakeri, R., & Omidian, A. R. (2005). Network vulnerability analysis through vulnerability take-grant model (VTG). In LNCS: Vol. 3783. Proceedings of 7th international conference on information and communications security (ICICS2005) (pp. 256–268). Berlin: Springer. citeseer.ist.psu.edu/749214.html.
de Silva, G., Sveda, M., Matousek, P., & Rysavy, O. (2010). Formal analysis approach on networks with dynamic behaviours. In Proceeding of the 2nd international workshop on reliable networks design and modeling.
Tidwell, T., Larson, R., Fitch, K., & Hale, J. (2001). Modeling Internet attacks. In Proc. of the IEEE workshop on information assurance and security, West Point, NY.
Xie, G. G., Zhan, J., Maltz, D. A., Zhang, H., Greenberg, A., Hjalmtysson, G., & Rexford, J. (2005). On static reachability analysis of IP networks. In Proc. IEEE INFOCOM.
Ou, X., Govindavajhala, S., & Appel, A. W. (2005). MulVAL: a logic-based network security analyzer. In Proc. of the 14th USENIX security symposium, Baltimore. citeseer.ist.psu.edu/article/bartal99firmato.html.
Yuan, L., & Chen, H. (2006). Fireman: a toolkit for firewall modeling and analysis. In Proceedings of IEEE symposium on security and privacy (pp. 199–213).
Zakeri, R., Shahriari, H., Jalili, R., & Sadoddin, R. (2005). Modeling TCP/IP networks topology for network vulnerability analysis. In 2nd int. symposium of telecommunications (pp. 653–658). citeseer.ist.psu.edu/749214.html.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
de Silva, G., Ryšavý, O., Matoušek, P. et al. On formal reachability analysis in networks with dynamic behavior. Telecommun Syst 52, 919–929 (2013). https://doi.org/10.1007/s11235-011-9585-2
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11235-011-9585-2