Abstract
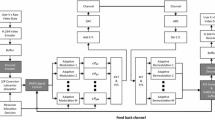
Recently, there has been a rapid progress in the field of wireless networks and mobile communications which makes the constraints on the used links clearly unconcealed. Wireless links are characterized by limited bandwidth and high latencies. Moreover, the bit-error-rate (BER) is very high in such environments for various reasons out of which weather conditions, cross-link interference, and mobility. High BER causes corruption in the data being transmitted over these channels. Therefore, convolutional encoding has been originated to be a professional means of communication over noisy environments. Sequential decoding, a category of convolutional codes, represents an efficient error detection and correction mechanism which attracts the attention for most of current researchers as for having a complexity that is dependent to the channel condition. In this paper, we propose a new queuing study over networking systems that make use of sequential decoders. Hence, the adopted flow and error control refer to stop-and-wait hybrid automatic repeat request. However, our queuing study is a novel extension to our prior work in which the lowest decoding complexity was fixed and did not account for the channel state. In other words, our proposed closed-form expression of the average buffer occupancy is totally generic and parameterized by not only channel condition and packet incoming rate, but also those that are automatically adapted to the channel conditions which include lower and upper bound decoding limits.








Similar content being viewed by others
References
Darabkh, K. A., Jafar, I., Al Sukkar, G., Abandah, G., & Al-Zubi, R. (2012). An improved queuing model for packet retransmission policy and variable latency decoders. IET Communications Journal, 6(18), 3315–3328.
Darabkh, K. A., Abu-Jaradeh, B., & Jafar, I. (2011). Incorporating automatic repeat request and thresholds with variable complexity decoding algorithms over wireless networks: Queuing analysis. IET Communications Journal, 5(10), 1377–1393.
Tafazolli, R., Palazzo, S., Payaró, M., & Heath, R. W, Jr. (2015). Enabling 5G: Energy and spectrally efficient communication systems. Transactions on Emerging Telecommunications Technologies, 26(1), 1–2.
Xiaohui, X., Wang, H., Feng, H., & Xing, C. (2015). Analysis of device-to-device communications with exclusion regions underlaying 5G networks. Transactions on Emerging Telecommunications Technologies, 26(1), 93–101.
Wang, H., Zhao, Q., Guan, X., Jia, Q.-S., & Li, L. (2013). Reconfiguring networked infrastructures by adding wireless communication capabilities to selected nodes. IEEE Transactions on Wireless Communications, 12(9), 4518–4528.
Wang, C.-X., Haider, F., Gao, X., You, X.-H., Yang, Yang, Yuan, D., et al. (2014). Cellular architecture and key technologies for 5G wireless communication networks. IEEE Communications Magazine, 52(2), 122–130.
Farhad Hossain, Md, Munasinghe, K. S., & Jamalipour, A. (2014). Traffic-aware two-dimensional dynamic network provisioning for energy-efficient cellular systems. Transactions on Emerging Telecommunications Technologies. doi:10.1002/ett.2872.
Hossain, E., Rasti, M., Tabassum, H., & Abdelnasser, A. (2014). Evolution toward 5G multi-tier cellular wireless networks: An interference management perspective. IEEE Wireless Communications, 21(3), 118–127.
Doré, J.-B., Berg, V., & Kténas, D. (2015). Channel estimation techniques for 5G cellular networks: FBMC and multiuser asynchronous fragmented spectrum scenario. Transactions on Emerging Telecommunications Technologies, 26(1), 15–30.
Dinh-Van, S., Shin, Y., & Shin, O.-S. (2015). Resource allocation and power control based on user grouping for underlay device-to-device communications in cellular networks. Transactions on Emerging Telecommunications Technologies. doi:10.1002/ett.2920.
Radack, S., & Kuhn, R. (2012). Protecting wireless local area networks. IT Professional, 14(6), 59–61.
Al-Zubi, R., Hawa, M., Al-Sukkar, G., & Darabkh, K. A. (2014). Markov-based distributed approach for mitigating self-coexistence problem in IEEE 802.22 WRANs. The Computer Journal, 57(12), 1765–1775.
Al-Mistarihi, M. F., Mohaisen, R., Sharaqa, A., Shurman, M. M., & Darabkh, K. A. (2015). Performance evaluation of multiuser diversity in multiuser two-hop cooperative multi-relay wireless networks using MRC over rayleigh fading channels. International Journal of Communication Systems, 28(1), 71–90.
Politis, A., Hilas, C. S., & Papatsoris, A. D. (2014). Optimising no acknowledgment policy on WLANs supporting voice over internet protocol. Electronics Letters, 50(1), 51–52.
Liou, Y.-S., Gau, R.-H., & Chang, C.-J. (2014). Dynamically tuning aggression levels for capacity-region-aware medium access control in wireless networks. IEEE Transactions on Wireless Communications, 13(4), 1766–1778.
Al-Zubi, R., Krunz, M., Al-Sukkar, G., Hawa, M., & Darabkh, K. A. (2014). Packet recycling and delayed ACK for improving the performance of TCP over MANETs. Wireless Personal Communications, 75(1), 943–963.
Darabkh, K. A., Ismail, S., Al-Shurman, M., Jafar, I., Alkhader, E., & Al-Mistarihi, M. (2012). Performance evaluation of selective and adaptive heads clustering algorithms over wireless sensor networks. International Journal of Network and Computer Applications, 35(6), 2068–2080.
Li, R., Zhao, Z., Yuan, Z., Palicot, J., & Zhang, H. (2014). Adaptive multi-task compressive sensing for localisation in wireless local area networks. IET Communications, 8(10), 1736–1744.
Rezha, F. P., & Shin, S. Y. (2014). Performance analysis of ISA100.11a under interference from an IEEE 802.11b wireless network. IEEE Transactions on Industrial Informatics, 10(2), 919–927.
Darabkh, K. A., Awad, A. M., & Khalifeh, A. F. (2015). New video discarding policies for improving UDP performance over wired/wireless networks. International Journal of Network Management, 25(3), 181–202.
Darabkh, K. A., Awad, A. M., & Khalifeh, A. F. (2014). Efficient PFD-based networking and buffering models for improving video quality over congested links. Wireless Personal Communications, 79(1), 293–320.
Darabkh, K. A., & Aygun, R. (2011). Improving UDP performance using intermediate QoD-aware hop system for wired/wireless multimedia communication systems. International Journal of Network Management, 21(5), 432–454.
Darabkh, K. A., Awad, A. M., & Khalifeh, A. F. (2013). Intelligent and selective video frames discarding policies for wireless networks, In Proceedings of the 2013 IEEE international symposium on multimedia (ISM 2013), Anaheim, California (pp. 297–300).
Darabkh, K. A., & Alsukour, O. (2015). Novel protocols for improving the performance of ODMRP and EODMRP over mobile Ad hoc networks. International Journal of Distributed Sensor Networks 2015, Article ID, 348967, 1–18.
Hawa, M., Darabkh, K. A., Khalaf, L. D. & Rahhal, J. S. Dynamic resource allocation using load estimation in distributed cognitive radio systems, AEÜ-International Journal of Electronics and Communications, In press.
Darabkh, K. A. (2011). Evaluation of channel adaptive access point system with fano decoding. International Journal of Computer Mathematics, 88(5), 916–937.
Darabkh, K. A., & Aygün, R. S. (2007). TCP traffic control evaluation and reduction over wireless networks using parallel sequential decoding mechanism, EURASIP. Journal on Wireless Communications and Networking, 2007, Article ID, 52492, 1–16.
Davoli, F., & Mongelli, M. (2015). Neural approximations of analog joint source-channel coding. IEEE Signal Processing Letters, 22(4), 421–425.
Fresnedo, O., Vazquez-Araujo, F. J., Castedo, L., & Garcia-Frias, J. (2014). Analogue joint source-channel coding for multiple input multiple output-orthogonal frequency division multiplexing systems. Transactions on Emerging Telecommunications Technologies. doi:10.1002/ett.2908.
Johnson, S. J., Ong, L., & Kellett, C. M. (2011). Joint channel-network coding strategies for networks with low-complexity relays. Transactions on Emerging Telecommunications Technologies, 22(7), 396–406.
Karbalayghareh, A., Nasiri-Kenari, M., & Hejazi, M. (2014). Convolutional network-coded cooperation in multi-source networks with a multi-antenna relay. IEEE Transactions on Wireless Communications, 13(8), 4323–4333.
Gadioli La Guardia, G. (2014). On classical and quantum MDS-convolutional BCH codes. IEEE Transactions on Information Theory, 60(1), 304–312.
Baldi, M., Cancellieri, G., & Chiaraluce, F. (2014). Array convolutional low-density parity-check codes. IEEE Communications Letters, 18(2), 336–339.
Maymon, S., & Eldar, Y. C. (2015). The viterbi algorithm for subset selection. IEEE Signal Processing Letters, 22(5), 524–528.
Zhuoran, X., Kam, P.-Y., & Changyuan, Y. (2014). Adaptive maximum likelihood sequence detection for QPSK coherent optical communication system. IEEE Photonics Technology Letters, 26(6), 583–586.
Ben Slimane, E., Jarboui, S., & Bouallegue, A. (2013). An improved differential space-time block coding scheme based on viterbi algorithm. IEEE Communications Letters, 17(9), 1707–1709.
Pelchat, E., & Poulin, D. (2013). Degenerate viterbi decoding. IEEE Transactions on Information Theory, 59(6), 3915–3921.
Lin, S., & Costello, D. J. (2004). Error control coding: Fundamentals and applications. Englewood Cliffs: Pearson Education.
Moreira, J. C., & Farrell, P. G. (2006). Essentials of error-control coding. Chichester: Wiley.
Abediseid, W. & Alouini, M.-S. (2013). Performance-complexity tradeoff in sequential decoding for the unconstrained AWGN channel, In Proceedings of 2013 IEEE international conference on communications (ICC), Budapest (pp. 3090–3094).
Abediseid, W., & Alouini, M. (2013). On lattice sequential decoding for the unconstrained AWGN channel. IEEE Transactions on Communications, 61(6), 2446–2456.
Gridasov, R., Bakhtin, A., Pertsev, L. & Timoshenko, A. (2013). Analisys of the behavior of sequential Fano decoder for convolutional codes, In Proceedings of 2013 5th international congress on ultra modern telecommunications and control systems and workshops (ICUMT), Almaty (pp. 100–105).
Xu, R., & Morris, K. (2012). High throughput sequential decoding with state estimation. IET Communications, 6(13), 2033–2039.
Darabkh, K.A. & Pan, W.D. (2006) Stationary queue-size distribution for variable complexity sequential decoders with large timeout. In Proceedings of the 44th ACM Southeast Conference, Melbourne, Florida (pp. 331–336).
Darabkh, K. A. & Aygun, R. S. (June 2006). Performance evaluation of sequential decoding system for UDP-based systems for wireless multimedia networks, Proceedings of 2006 international conference on wireless networks (ICWN’06), Las Vegas, Nevada (pp. 365–371).
Makki, B. & Eriksson, T. (2012) Interference-free spectrum sharing using a sequential decoder at the primary user, In Proceedings of 2012 IEEE 13th international workshop on signal processing advances in wireless communications (SPAWC), Cesme (pp.154–158).
Li, T., Leith, D., & Malone, D. (2011). Buffer sizing for 802.11-based networks. IEEE/ACM Transactions on Networking, 19(1), 156–169.
Jagannathan, K., & Modiano, E. (2013). The impact of queue length information on buffer overflow in parallel queues. IEEE Transactions on Information Theory, 59(10), 6393–6404.
Chan, S. C. F., Chan, K. M., Liu, K., & Lee, J. Y. B. (2014). On queue length and link buffer size estimation in 3G/4G mobile data networks. IEEE Transactions on Mobile Computing, 13(6), 1298–1311.
Darabkh, K. A. (2010). Queuing analysis and simulation of wireless access and end point systems using fano decoding. Journal of Communications, 5(7), 551–561.
Darabkh, K. A. & Abu-Jaradeh, B. (2010). Bounded fano decoders over intermediate hops excluding packet retransmission, In Proceedings of IEEE 24th international conference on advanced information networking and applications (AINA 2010), Perth (pp. 299–303).
Byun, H.-J., & Lim, J.-T. (2005). Explicit window adaptation algorithm over TCP wireless networks. IEE Proceedings-Communications, 152(5), 691–696.
Seferoglu, H., & Markopoulou, A. (2014). Network coding-aware queue management for TCP flows over coded wireless networks. IEEE/ACM Transactions on Networking, 22(4), 1297–1310.
Lee, Jinsung, Lee, Hyang-Won, Yi, Yung, & Chong, Song. (2012). Improving TCP performance over optimal CSMA in wireless multi-hop networks. IEEE Communications Letters, 16(9), 1388–1391.
Hashimoto, M., Hasegawa, G., & Murata, M. (2014). An analysis of energy consumption for TCP data transfer with burst transmission over a wireless LAN. International Journal of Communication Systems. doi:10.1002/dac.2832.
Ren, F., & Lin, C. (2011). Modeling and improving TCP performance over cellular link with variable bandwidth. IEEE Transactions on Mobile Computing, 10(8), 1057–1070.
Shin, K., Kim, J., & Choi, S. B. (2011). Loss recovery scheme for TCP using MAC MIB over wireless access networks. IEEE Communications Letters, 15(10), 1059–1061.
Huang, J., Wang, J., & Ye, J. (2014). A buffer management algorithm for improving up/down transmission congestion protocol fairness in IEEE 802.11 wireless local area networks. International Journal of Communication Systems, 27(10), 2228–2240.
Cheng, R.-S., & Deng, D.-J. (2014). Congestion control with dynamic threshold adaptation and cross-layer response for TCP Vegas over IEEE 802.11 wireless networks. International Journal of Communication Systems, 27(11), 2918–2930.
Darabkh, K. A. Fast and upper bounded fano decoding algorithm: queuing analysis. Transactions on Emerging Telecommunications Technologies (in press)
Darabkh, K. A. & Aygun, R. S. (2006) Quality of service and performance evaluation of congestion control for multimedia networking, In Proceedings of 2006 international conference on internet computing (ICOMP’06), Las Vegas, Nevada (pp. 217–223)
Darabkh K. A. & Abu-Jaradeh, B. (2010). Buffering study over intermediate hops including packet retransmission, In Proceedings of IEEE international conference on multimedia computing and information technology (MCIT-2010), Sharjah (pp. 45–48).
Darabkh, K. A., Khalifeh, A., Naser, M. & Al-Qaralleh, E. (2012). New arriving process for convolutional codes with adaptive behavior, In Proceedings of IEEE/SSD’12 multi-conference on systems, signals, and devices, Chemnitz (pp. 1–6).
Meyn, S. P., & Tweedie, R. L. (2005). Markov chains and stochastic stability. Cambridge: Cambridge University Press.
Darabkh K. A. & Aygun, R. S. (2006) Quality of service evaluation of error control for TCP/IP-based systems in packet switching ATM networks, In Proceedings of 2006 international conference on internet computing (ICOMP’06), Las Vegas, Nevada (pp. 243–248)
Cross, D., & Harris, C. M. (1998). Fundamentals of queuing theory. New York: Wiley.
Author information
Authors and Affiliations
Corresponding author
Appendices
Appendix 1: Proofs of Lemma 1 and Corollaries 1 and 2
Using (3) in (7), we can write \(p_{1,T-1} \) as
Substituting (52) into (6) (specifically in place of \(p_{1,j} \) where \(T-1=j)\) and using (1), (6) can be written as
After writing for \(p_{1,0} \), (52) can be written as
Substituting (52) into (12) and utilizing (3) give
Extracting \(p_{1,0}\) from (53) and using it in (55) produce
where,
Substituting (54) into (17) provides
Similarly, (18) can be written as
Appendix 2: Proofs of Theorem 1, Corollaries (3)–(5), Lemma 2, and Corollary 6
Referring to (22), we find that
Substituting (9) and (10) into (60) and rearranging yield
Using \(\sum _{n=1}^\infty {p_{n+1,j} z^{n}} =\frac{1}{z}\left( {P_j (z)-p_{1,j} z} \right) \) and accordingly (6) provide
For the derivation of\(P_1 (z)\), we can write (22) as
Substituting (7), (15), and (16) into (63) and rearranging yield
Using \(\sum _{n=2}^\infty {p_{n-1,0} z^{n}} =z\sum _{n=2}^\infty {p_{n-1,0} z^{n-1}} =zP_0 (z)\) gives
As for deriving\(P_2 (z)\), (22) can be written as
Substituting (7) and (11) into (66), rearranging, and simplifying, we acquire
Using (65), we come into the possession of
To derive the general form (i.e., \(P_j (z))\) where \(M-1\ge j\ge 3\) at \(M >3\), we use
Substituting (7) and (8) into (69) and rearranging, we obtain
Using (2), we can write (69) recursively as
Utilizing (68), we attain
About the general form where \(j\ge M\), (22) can be written after using (7) and (8) as
Using (3), we can write (73) recursively as
Using (71), we can find that
Substituting (68) into (75) and consequently into (74), we get
As far as \(P_{0,1,1} (z)\) is concerned, we use (12) and (13) in (23) as follows
Using \(\sum _{n=1}^\infty {p_{n+1,T-1} z^{n}} =\frac{1}{z}\left( {P_{T-1} (z)-p_{1,T-1} z} \right) \) and simplifying yield
Substituting (76) into (78) (particularly in place of \(P_{T-1} (z)\) where \(j=T-1)\) gives
After rearrangement and using (3), (54), and (59), we get
Concerning the derivation of \(P_{1,1,2} (z)\), (24) can be written after considering (19) and (20) as
Using \(\sum _{n=2}^\infty {\lambda p_{n-1,0,1,1} z^{n}=zP_{0,1,1} (z)} \), we obtain
Referring to (62), it can be rewritten as
Simplifying the summation part and using (1) and (76), we achieve
where,
Consequently, (83) can be written as
Substituting (68) into (75) and using it in (86) and considering (82), we come into
Using (1) and (2), we can show that
Presently, substituting (56) and (59) into (80) and accordingly the expression of \(P_{0,1,1} (z)\)into (87) after utilizing (88) reach
where,
and,
Substituting (56), (59), and (89) into (80), we obtain
where,
On the other hand, using (92) in (82) provides
Appendix 3: A Proof of Lemma 3
Alluding to (21) and utilizing the fact that \(P(1)=1\), we get
Substituting \(z=1\) into (89) induces
Having \(z=1\) in (90) gives 0/0, then we apply L’Hospital’s rule as
After reordering and simplifying, we have
where,
Moreover, substituting \(z=1\) into (65), (68), (72), and (76), and accordingly their expressions into (95) along with (25), (27), (28), and (96), we obtain
where,
Appendix 4: A Proof of Preposition 1
The derivative of (30) can be found as follows
where,
and,
Substituting \(z=1\) into (102) yields
Taking into consideration that \(f(1)=1\) and \({f}'(1)=\lambda \) and using (2) and (85), we get
Taking the first derivation of (85) and then substituting for \(z=1\), we obtain
Substituting \(z=1\) into (103)–(107) and utilizing (109)–(110), we write
and,
Substituting (109), (111)–(115) into (108) yields 0/0. Hence, we apply L’Hospital’s rule to (102) as follows
Substituting \(z=1\), we get
Examining the derivative of (103)–(107), applying \(z=1\), and utilizing (109)–(110) give
and,
Substituting (118)–(122) and (109) into (117) lead to 0/0 one more time. By applying L’Hospital’s rule, for the second time, we get
where,
and,
Substituting \(z=1\) into (123) yields
Keeping into account that \({f}''(1)=0\) and referring to (85), we write
and,
Examining the second derivative of (103)–(107), substituting for \(z=1,\) and using (109)–(110) and (128)–(129) provide
and,
Substituting \(z=1\) into (124)–(126), utilizing (109)–(110) and (128), and accordingly substituting them along with (130)–(134) into (127), we ultimately have (after simplifying)
where,
and,
Rights and permissions
About this article
Cite this article
Darabkh, K.A., Ibeid, H., Jafar, I.F. et al. A generic buffer occupancy expression for stop-and-wait hybrid automatic repeat request protocol over unstable channels. Telecommun Syst 63, 205–221 (2016). https://doi.org/10.1007/s11235-015-0115-5
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11235-015-0115-5