Abstract
Underlay mechanism allows concurrent communications of primary users and secondary users in cognitive radio networks (CRNs), causing mutual interference between them. However, current literature neglects primary interference or considers it as Gaussian noise. In addition, artificial noise, which is intentionally generated to interfere eavesdroppers, can improve security performance of CRNs. This paper analyzes security performance of CRNs, accounting for artificial noise and considering primary interference as non-Gaussian noise, under maximum transmit power constraint, interference power constraint, and Rayleigh fading channels. The security performance is evaluated through proposed exact expressions of secrecy outage probability, non-zero achievable secrecy rate probability, and intercept probability, which are verified by Monte-Carlo simulations. Various results demonstrate that CRNs suffer security performance saturation in the range of large maximum transmit power or large maximum interference power, and primary interference significantly deteriorates security performance while artificial noise is useful in enhancing this performance.





Similar content being viewed by others
Notes
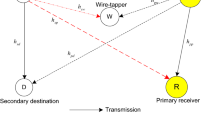
\(h_{tr} \sim \mathcal {CN}(0,\lambda _{tr})\) denotes a circular symmetric complex Gaussian random variable (CSCGRV) \(h_{tr}\) with zero mean and variance \(\lambda _{tr}\).
This can be alternatively interpreted that artificial noise is transmitted in the null space to D or shared with D (e.g., use the seed of the artificial noise generator in a secure manner). Such interpretations are widely accepted in open literature (e.g., [10,11,12,13, 15, 20,21,22] and references therein).
References
Panwar, N., Sharma, S., & Singh, A. K. (2016). A survey on 5G: The next generation of mobile communication. Elsevier Physical Communication, 18(2), 64–84.
Tavana, M., Rahmati, A., Shah-Mansouri, V., & Maham, B. (2017). Cooperative sensing with joint energy and correlation detection in cognitive radio networks. IEEE Communications Letters, 21(1), 132–135.
Darsena, D., Gelli, G., & Verde, F. (2017). An opportunistic spectrum access scheme for multicarrier cognitive sensor networks. IEEE Sensors Journal, 17(8), 2596–2606.
Liu, Y., Chen, H. H., & Wang, L. (2017). Physical layer security for next generation wireless networks: Theories, technologies, and challenges. IEEE Communications Surveys & Tutorials, 19(1), 347–376.
Hu, J., Cai, Y., Yang, N., Zhou, X., & Yang, W. (2017). Artificial-noise-aided secure transmission scheme with limited training and feedback overhead. IEEE Transactions on Wireless Communications, 16(1), 193–205.
Wang, C., & Wang, H. M. (2014). On the secrecy throughput maximization for MISO cognitive radio network in slow fading channels. IEEE Transactions on Information Forensics and Security, 9(11), 1814–1827.
Ho-Van, K. (2016). Exact outage probability analysis of proactive relay selection in cognitive radio networks with MRC receivers. IEEE/KICS Journal of Communications and Networks, 18(3), 288–298.
Wang, D., Ren, P., Du, Q., Sun, L., & Wang, Y. (2016). Cooperative relaying and jamming for primary secure communication in cognitive two-way networks. In Proceedings of IEEE VTC (pp. 1–5). Nanjing, China, May 15–18, 2016.
Fang, B., Qian, Z., Zhong, W., & Shao, W. (2015). AN-aided secrecy precoding for SWIPT in cognitive MIMO broadcast channels. IEEE Communications Letters, 19(9), 1632–1635.
Nguyen, V. D., Duong, T. Q., Dobre, O. A., & Shin, O. S. (2016). Joint information and jamming beamforming for secrecy rate maximization in cognitive radio networks. IEEE Transactions on Information Forensics and Security, 11(11), 2609–2623.
Fang, B., Qian, Z., Shao, W., & Zhong, W. (2016). Precoding and artificial noise design for cognitive MIMOME wiretap channels. IEEE Transactions on Vehicular Technology, 65(8), 6753–6758.
Wu, Y., Chen, X., & Chen, X. (2015). Secure beamforming for cognitive radio networks with artificial noise. In IEEE WCSP (pp. 1–5). Nanjing, China, Oct 15–17, 2015.
Hu, X., Zhang, X., Huang, H., & Li, Y. (2016). Secure transmission via jamming in cognitive radio networks with possion spatially distributed eavesdroppers. In Proceedings of IEEE PIMRC (pp. 1–6). Valencia, Spain, Sept 4–7, 2016.
Cai, Y., Xu, X., & Yang, W. (2016). Secure transmission in the random cognitive radio networks with secrecy guard zone and artificial noise. IET Communications, 10(15), 1904–1913.
Li, Z, Jing, T., Cheng, X., Huo, Y., Zhou, W., & Chen, D. (2015). Cooperative jamming for secure communications in MIMO cooperative cognitive radio networks. In Proceedings of IEEE ICC (pp. 7609–7614). London, UK, Jun 8–12, 2015.
W. Liu, L. Guo, T. Kang, J. Zhang, & J. Lin, (2015) Secure cognitive radio system with cooperative secondary networks. In Proceedings of IEEE ICT, (pp. 6–10). Sydney, Australia, April 27–29, 2015.
He, T., Chen, H., & Liu, Q. (2013). QoS-based beamforming with cooperative jamming in cognitive radio networks. In Proceedings of ICCCAS (pp. 42–45). Chengdu, China, Nov 15–17, 2013.
Liu, W., Sarkar, M. Z. I., Ratnarajah, T. (2014). On the security of cognitive radio networks: Cooperative jamming with relay selection. In Proceedings of EuCNC (pp. 1–5), Bologna, Italy, June 23–26, 2014.
Liu, W., Sarkar, M. Z. I., Ratnarajah, T., & Du, H. (2017). Securing cognitive radio with a combined approach of beamforming and cooperative jamming. IET Communications, 11(1), 1–9.
Zou, Y. (2017). Physical-layer security for spectrum sharing systems. IEEE Transactions on Communications, 16(2), 1319–1329.
Liu, Y., Wang, L., Duy, T. T., Elkashlan, M., & Duong, T. Q. (2015). Relay selection for security enhancement in cognitive relay networks. IEEE Wireless Communications Letters, 4(1), 46–49.
Chakraborty, P., & Prakriya, S. (2017). Secrecy performance of an idle receiver assisted underlay secondary network. IEEE Transactions on Vehicular Technology, 66(10), 9555–9560.
Biglieri, E., Proakis, J., & Shamai, S. (1998). Fading channels: Information-theoretic and communications aspects. IEEE Transactions on Information Theory, 44(6), 2619–2692.
Wyner, A. D. (1975). The wire-tap channel. Bell Labs Technical Journal, 54(8), 1355–1387.
Gradshteyn, I. S., & Ryzhik, I. M. (2000). Table of integrals, series and products (6th ed.). San Diego, CA: Academic.
Zou, Y., Wang, X., & Shen, W. (2013). Physical-layer security with multiuser scheduling in cognitive radio networks. IEEE Transactions on Communications, 61(12), 5103–5113.
Ahmed, N, Khojastepour, M., & Aazhang, B. (2004). Outage minimization and optimal power control for the fading relay channel. In Proceedings IEEE information theory workshop (pp. 458–462). San Antonio, TX, USA, Oct 2004.
Acknowledgements
This research is funded by Vietnam National Foundation for Science and Technology Development (NAFOSTED) under grant number 102.04-2017.01
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Ho-Van, K., Do-Dac, T. Joint effect of artificial noise and primary interference on security performance of cognitive radio networks. Telecommun Syst 68, 593–603 (2018). https://doi.org/10.1007/s11235-017-0381-5
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11235-017-0381-5