Abstract
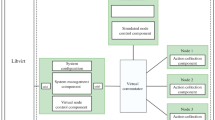
In a complex network as a cloud computing environment, security is becoming increasingly based on deception techniques. To date, the static nature of cyber networks offers to adversaries good opportunities to systematically study the network environment, launch a cyber-attack effortlessly and wide-spread and finally defeat the target system. In order to resolve the limitations of the traditional security measures as intrusion prevention or detection systems, firewall, access list, etc., which did not change the attack surface and cannot avoid zero-days attacks, technics that provide dynamic defense, such virtual machine migration and honeypot should be deployed. Despite this, with a virtual machine migration technique, not all virtual machines’ migration between servers enhances security considerably. In this paper, we propose an integrated defense system combining virtual machine migration and honeypot. The effectiveness of the proposed system is discussed in terms of security policies. In addition, our proposed model determines the potential attack paths quantitatively then classifies them into two sub-sets: attack paths explored only and attack paths explored and exploited based on the black box intrusion steps. Thus, to model the interaction attacker–defender, the attack graph combined with the stochastic game theory is used. Finally, we carry out some numerical results to demonstrate the effectiveness of the proposed security game model.












Similar content being viewed by others
References
Adili, M. T., Mohammadi, A., Manshaei, M. H., & Rahman, M. A. (2017). A cost-effective security management for clouds: A game-theoretic deception mechanism. In 2017 IFIP/IEEE symposium on integrated network and service management (IM) (pp. 98–106). New York: IEEE.
Al-Shaer, E., Wei, J., Hamlen, K. W., & Wang, C (Eds.), (2019). Honeypot deception tactics. In Autonomous cyber deception (pp. 35–45). Berlin: Springer.
Arghavani, A., Arghavani, M., Ahmadi, M., & Crane, P. (2018). Attacker-manager game tree (AMGT): A new framework for visualizing and analysing the interactions between attacker and network security manager. Computer Networks, 133, 42–58.
Azab, M., & Eltoweissy, M. (2016). Migrate: Towards a lightweight moving-target defense against cloud side-channels. In 2016 IEEE security and privacy workshops (SPW) (pp. 96–103). New York: IEEE.
Bar, A., Shapira, B., Rokach, L., & Unger, M. (2016). Identifying attack propagation patterns in honeypots using Markov chains modeling and complex networks analysis. In 2016 IEEE international conference on software science, technology and engineering (SWSTE) (pp. 28–36). New York: IEEE.
Baykara, M., & Das, R. (2018). A novel honeypot based security approach for real-time intrusion detection and prevention systems. Journal of Information Security and Applications, 41, 103–116.
Beckery, S., Seibert, J., Zage, D., Nita-Rotaru, C., & Statey, R. (2011). Applying game theory to analyze attacks and defenses in virtual coordinate systems. In 2011 IEEE/IFIP 41st international conference on dependable systems and networks (DSN) (pp. 133–144). New York: IEEE.
Beham, M., Vlad, M., & Reiser, H. P. (2013). Intrusion detection and honeypots in nested virtualization environments. In 2013 43rd annual IEEE/IFIP international conference on dependable systems and networks (DSN) (pp. 1–6). New York: IEEE.
Boulaiche, A., & Adi, K. (2018). An auto-learning approach for network intrusion detection. Telecommunication Systems, 68(2), 277–294.
Cai, G., Wang, B., Wang, X., Yuan, Y., & Li, S. (2016). An introduction to network address shuffling. In 2016 18th international conference on advanced communication technology (ICACT) (pp. 185–190). New York: IEEE.
Carroll, T. E., Crouse, M., Fulp, E. W., & Berenhaut, K. S. (2014). Analysis of network address shuffling as a moving target defense. In 2014 IEEE international conference on communications (ICC) (pp. 701–706). New York: IEEE.
Cho, J. H., & Ben-Asher, N. (2018). Cyber defense in breadth: Modeling and analysis of integrated defense systems. The Journal of Defense Modeling and Simulation, 15(2), 147–160.
Debroy, S., Calyam, P., Nguyen, M., Stage, A., & Georgiev, V. (2016). Frequency-minimal moving target defense using software-defined networking. In 2016 international conference on computing, networking and communications (ICNC) (pp. 1–6). EEE.
Dongxia, L., & Yongbo, Z. (2012). An intrusion detection system based on honeypot technology. In 2012 international conference on computer science and electronics engineering (Vol. 1, pp. 451–454). New York: IEEE.
El Mir, I., Kandoussi, E. M., Hanini, M., Haqiq, A., & Kim, D. S. (2017). A game theoretic approach based virtual machine migration for cloud environment security. International Journal of Communication Networks and Information Security, 9(3), 345–357.
Kaaniche, M., Deswarte, Y., Alata, E., Dacier, M., & Nicomette, V. (2007). Empirical analysis and statistical modeling of attack processes based on honeypots. Preprint arXiv:0704.0861.
Kamhoua, C.A., Kwiat, L., Kwiat, K.A., Park, J.S., Zhao, M., & Rodriguez, M. (2014). Game theoretic modeling of security and interdependency in a public cloud. In 2014 IEEE 7th international conference on cloud computing (pp. 514–521). New York: IEEE.
Kandoussi, E. M., El Mir, I., Hanini, M., & Haqiq, A. (2017). Modeling an anomaly-based intrusion prevention system using game theory. In International conference on innovations in bio-inspired computing and applications (pp. 266–276). Berlin: Springer.
Khan, M. E., & Khan, F., et al. (2012). A comparative study of white box, black box and grey box testing techniques. International Journal of Advanced Computer Science and Applications, https://doi.org/10.14569/IJACSA.2012.030603
Kiennert, C., Ismail, Z., Debar, H., & Leneutre, J. (2018). A survey on game-theoretic approaches for intrusion detection and response optimization. ACM Computing Surveys (CSUR), 51(5), 90.
Lei, C., Ma, D. H., & Zhang, H. Q. (2017). Optimal strategy selection for moving target defense based on Markov game. IEEE Access, 5, 156–169.
Lei, C., Ma, D. H., Zhang, H. Q., & Wang, L. M. (2016). Moving target network defense effectiveness evaluation based on change-point detection. Mathematical Problems in Engineering, https://doi.org/10.1155/2016/6391502
Lei, C., Zhang, H. Q., Wan, L. M., Liu, L., & Ma, D. (2018). Incomplete information Markov game theoretic approach to strategy generation for moving target defense. Computer Communications, 116, 184–199.
Liu, Y., Xu, C., Zhan, Y., Liu, Z., Guan, J., & Zhang, H. (2017). Incentive mechanism for computation offloading using edge computing: A stackelberg game approach. Computer Networks, 129, 399–409.
Maleki, H., Valizadeh, S., Koch, W., Bestavros, A., & van Dijk, M. (2016). Markov modeling of moving target defense games. In Proceedings of the 2016 ACM workshop on moving target defense (pp. 81–92). New York: ACM.
Manadhata, P. K. (2013). Game theoretic approaches to attack surface shifting. In S. Jajodia, A. K. Ghosh, V.S. Subrahmanian, V. Swarup, C. Wang and X. S. Wang (Eds.), Moving target defense II (pp. 1–13). Berlin: Springer.
Mehdi, M. M., Raza, I., & Hussain, S. A. (2017). A game theory based trust model for vehicular ad hoc networks (vanets). Computer Networks, 121, 152–172.
Mun, H. J., & Han, K. H. (2016). Blackhole attack: User identity and password seize attack using honeypot. Journal of Computer Virology and Hacking Techniques, 12(3), 185–190.
Ou, X., Govindavajhala, S., & Appel, A. W. (2005). MulVAL: A logic-based network security analyzer. In USENIX security symposium (Vol. 8, pp. 113–128). Baltimore, MD.
Sheyner, O., & Wing, J. (2003). Tools for generating and analyzing attack graphs. In International symposium on formal methods for components and objects (pp. 344–371). Berlin: Springer.
Speicher, P., Steinmetz, M., Backes, M., Hoffmann, J., & Künnemann, R. (2018). Stackelberg planning: Towards effective leader–follower state space search. In 32nd AAAI conference on artificial intelligence.
Thongthua, A., & Ngamsuriyaroj, S. (2016). Assessment of hypervisor vulnerabilities. In 2016 International conference on cloud computing research and innovations (ICCCRI) (pp. 71–77). New York: IEEE.
Venkatesan, S., Albanese, M., Amin, K., Jajodia, S., & Wright, M. (2016). A moving target defense approach to mitigate DDoS attacks against proxy-based architectures. In 2016 IEEE conference on communications and network security (CNS) (pp. 198–206). New York: IEEE.
Wang, K., Du, M., Maharjan, S., & Sun, Y. (2017). Strategic honeypot game model for distributed denial of service attacks in the smart grid. IEEE Transactions on Smart Grid, 8(5), 2474–2482.
Yusoh, Z. I. M., & Tang, M. (2010). A penalty-based genetic algorithm for the composite SaaS placement problem in the cloud. In IEEE congress on evolutionary computation (pp. 1–8). New York: IEEE.
Zheng, J., Cai, Y., Wu, Y., & Shen, X. (2018). Dynamic computation offloading for mobile cloud computing: A stochastic game-theoretic approach. IEEE Transactions on Mobile Computing, 18(4), 771–786.
Zheng, J., & Siami Namin, A. (2018). A Markov decision process to determine optimal policies in moving target. In Proceedings of the 2018 ACM SIGSAC conference on computer and communications security (pp. 2321–2323). New York: ACM.
Zhu, Q., & Başar, T. (2013). Game-theoretic approach to feedback-driven multi-stage moving target defense. In International conference on decision and game theory for security (pp. 246–263). Berlin: Springer.
Zhuang, R., DeLoach, S. A., & Ou, X. (2014). Towards a theory of moving target defense. In Proceedings of the 1st ACM workshop on moving target defense (pp. 31–40). New York: ACM.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendices
A Appendix
Proof of Theorem 1
For a fixed value of \(u_{s}\) we have:
If \(M_{s}\) is played by the defender then the best response of the attacker is \(AP_{i_{0}}\) with: \(i_{0}=\underset{i \in \{1, \ldots , m\}}{argmax} u_{s} \alpha _{i} L_{i}-\beta _{i} C_{i}\).
If \({\overline{M}}\) is played by the defender than then best response of the defender is \(AP_{m}\).
Therefore, the Nash equilibrium are given as follows:
If \(i_{0}=m\):
If \(u_{s}<1-\frac{C^{M}}{\alpha _{m} L_{m}}\): \(NE_{pure}=\left( M_{s}, AP_{m}\right) \),
If \(u_{s} \ge 1-\frac{C^{M}}{\alpha _{m} L_{m}}\): \(NE_{pure}=\left( {\overline{M}}, AP_{m}\right) \).
If \(i_{0} \ne m\):
If \(u_{s} \le 1-\frac{C^{M}}{\alpha _{i_{0}} L_{i_{0}}}\): \(NE_{pure}=\left( M_{s}, AP_{i_{0}}\right) \),
If \(u_{s} \ge 1-\frac{C^{M}}{\alpha _{m} L_{m}}\): \(NE_{pure}=\left( {\overline{M}}, AP_{m}\right) \),
If \(1-\frac{C^{M}}{\alpha _{i_{0}} L_{i_{0}}}<u_{s}<1-\frac{C^{M}}{\alpha _{m} L_{m}}\): we have a mixed Nash equilibrium
\(NE_{\text{ mixed }}=\left( x \times A P_{i_{0}}+(1-x) \times AP_{m}, y \times M_{s}\right. \)\(\left. +(1-y) \times {\overline{M}}\right) \) Indeed x and y are computed as follows:
\({\mathcal {E}}_{{ Def}}(M_{s})={\mathcal {E}}_{{ Def}}({\overline{M}}) \Leftrightarrow x=\frac{\alpha _{m} L_{m}\left( 1-u_{s}\right) -C^{M}}{\left( \alpha _{m} L_{m}-\alpha _{i_{0}} L_{i_{0}}\right) \left( 1-u_{s}\right) }\)
\({\mathcal {E}}_{At}\left( AP_{m}\right) ={\mathcal {E}}_{At}\left( AP_{i_{0}}\right) \Leftrightarrow y=\frac{1}{1-u_{s}}\)\( \times \left( 1-\frac{\beta _{m} C_{m}-\beta _{i_{0}} C_{i_{0}}}{\alpha _{m} L_{m}-\alpha _{i_{0}} L_{i_{0}}}\right) \).
\(\square \)
B Appendix
-
1.
Proof that the strategy \(M_{{\overline{s}}}\) is a strictly dominated by \(M_{s}\):
For \(i \in \{1, \ldots , n\}\): \(u_{s}<u_{{\overline{s}}} \Leftrightarrow u_{s} \alpha _{i} L_{i}<u_{{\overline{s}}} \alpha _{i} L_{i} \Leftrightarrow -u_{{\overline{s}}} \alpha _{i} L_{i}<-u_{s} \alpha _{i} L_{i}\).
Thereby: \(-u_{{\overline{s}}} \alpha _{i} L_{i}-C^{M}<-u_{s} \alpha _{i} L_{i}-C^{M}\)
Then the strategy \(M_{{\overline{s}}}\) is strictly dominated by \(M_{s}\).
-
2.
The Bayesian sub-game \(g^{i}_{{\overline{m}}}\) is resolved by using the mathematical expression related to compute the Bayesian Nash equilibrium. Hence, we obtain:
$$\begin{aligned} {\left\{ \begin{array}{ll} \mu _{{ Def}}({\overline{M}}|Hp)=1 \\ \mu _{{ Def}}(.|Rn) \in {{\,\mathrm{argmax}\,}}_{\gamma \in \varDelta \left( A^{Rn}_{{ Def}}\left( g^{i}_{{\overline{m}}} \right) \right) } \in \\ \left[ \gamma \left( M_{s} \right) \left( -C^{M}+\mu _{At}\left( A|Ml \right) \left( 1-u_{s} \right) \left( 1-\alpha _{i} \right) L_{i}\right) \right. \\ \quad \left. -h-\mu _{At}\left( A|Ml \right) \left( 1-\alpha _{i} \right) L_{i} \right] \\ \mu _{At}(.|Ml) \in {{\,\mathrm{argmax}\,}}_{\gamma \in \varDelta \left( A^{Ml}_{At}\left( g^{i}_{{\overline{m}}} \right) \right) } \in \\ \gamma \left( A \right) \left[ \theta \left( 1-\alpha _{i} \right) L_{i}\left( 1-\left( 1-\mu _{s} \right) \mu _{{ Def}}\left( M|Rn \right) \right) -\left( 1-\beta _{i} \right) C_{i} \right] \end{array}\right. } \end{aligned}$$Then, the probability distributions \(\mu _{{ Def}}(.|Rn)\) and \(\mu _{At}(.|Ml)\) are defined as follows:
If \(\left( 1-\alpha _{i}\right) L_{i} \ge u_{s}\left( 1-\alpha _{i}\right) L_{i}+C^{M}\):
If \(\theta \left( 1-\alpha _{i}\right) L_{i} \ge \theta u_{s}\left( 1-\alpha _{i}\right) L_{i} \ge \left( 1-\beta _{i}\right) C_{i}\): \({\left\{ \begin{array}{ll} \mu _{{ Def}}(M_{s}|Rn)=1 \\ \mu _{At}(A|Ml)=1 \end{array}\right. }\)
If \(\theta \left( 1-\alpha _{i}\right) L_{i} \ge \left( 1-\beta _{i}\right) C_{i} \ge \theta u_{s}\left( 1-\alpha _{i}\right) L_{i}\):
\({\left\{ \begin{array}{ll} \mu _{{ Def}}(M_{s}|Rn)=\frac{1}{1-u_{s}}\left( 1-\frac{\left( 1-\beta _{i}\right) C_{i}}{\theta \left( 1-\alpha _{i}\right) L_{i}}\right) \\ \mu _{At}(A|Ml)=\frac{C^{M}}{\left( 1-u_{s}\right) \left( 1-\alpha _{i}\right) L_{i}} \end{array}\right. }\)
If \(\left( 1-\beta _{i}\right) C_{i} \ge \theta \left( 1-\alpha _{i}\right) L_{i} \ge \theta u_{s}\left( 1-\alpha _{i}\right) L_{i}\):
\({\left\{ \begin{array}{ll} \mu _{{ Def}}(M_{s}|Rn)=0 \\ \mu _{At}(A|Ml)=0 \end{array}\right. }\)
If \(u_{s}\left( 1-\alpha _{i}\right) L_{i}+C^{M}>\left( 1-\alpha _{i}\right) L_{i}\):
If \(\theta \left( 1-\alpha _{i}\right) L_{i} \ge \theta u_{s}\left( 1-\alpha _{i}\right) L_{i} \ge \left( 1-\beta _{i}\right) C_{i}\) or \(\theta \left( 1-\alpha _{i}\right) L_{i} \ge \left( 1-\beta _{i}\right) C_{i} \ge \theta u_{s}\left( 1-\alpha _{i}\right) L_{i}\):
\({\left\{ \begin{array}{ll} \mu _{{ Def}}(M_{s}|Rn)=0 \\ \mu _{At}(A|Ml)=1 \end{array}\right. }\)
If \(\left( 1-\beta _{i}\right) C_{i} \ge \theta \left( 1-\alpha _{i}\right) L_{i} \ge \theta u_{s}\left( 1-\alpha _{i}\right) L_{i}\):
\({\left\{ \begin{array}{ll} \mu _{{ Def}}(M_{s}|Rn)=0 \\ \mu _{At}(A|Ml)=0 \end{array}\right. }\)
Secondly, the Bayesian sub-game \(g_{m}^{i}\) is resolved below by using the same approach presented above. Then, we obtain:
$$\begin{aligned} {\left\{ \begin{array}{ll} \mu _{{ Def}}({\overline{M}}|Hp)=1 \\ \mu _{{ Def}}(.|Rn) \in {{\,\mathrm{argmax}\,}}_{\gamma \in \varDelta \left( A^{Rn}_{{ Def}}\left( g^{i}_{m} \right) \right) }\in \\ \gamma \left( M_{s} \right) \left[ -C^{M}+\mu _{At}\left( A|Ml \right) u_{s}\left( 1-v_{s} \right) \left( 1-\alpha _{i} \right) L_{i} \right] \\ \quad -h-\mu _{At}\left( A|Ml \right) u_{s}\left( 1-\alpha _{i} \right) L_{i}\\ \mu _{At}(.|Ml) \in {{\,\mathrm{argmax}\,}}_{\gamma \in \varDelta \left( A^{Ml}_{At}\left( g^{i}_{m} \right) \right) } \in \\ \gamma \left( A \right) \left[ \theta u_{s}\left( 1-\alpha _{i} \right) L_{i}\left( 1-\left( 1-v_{s} \right) \mu _{{ Def}}\left( M|Rn \right) \right) \right. \\ \quad \left. -\left( 1-\beta _{i} \right) C_{i} \right] \end{array}\right. } \end{aligned}$$Then, the probability distributions \(\mu _{{ Def}}(.|Rn)\) and \(\mu _{At}(.|Ml)\) are defined as follows:
If \(u_{s}\left( 1-\alpha _{i}\right) L_{i} \ge v_{s} u_{s}\left( 1-\alpha _{i}\right) L_{i}+C^{M}\):
If \(\theta u_{s}\left( 1-\alpha _{i}\right) L_{i} \ge \theta u_{s} v_{s}\left( 1-\alpha _{i}\right) L_{i} \ge \left( 1-\beta _{i}\right) C_{i}\): \({\left\{ \begin{array}{ll} \mu _{{ Def}}(M_{s}|Rn)=1\\ \mu _{At}(A|Ml)=1 \end{array}\right. }\)
If \(\theta u_{s}\left( 1-\alpha _{i}\right) L_{i} \ge \left( 1-\beta _{i}\right) C_{i} \ge \theta u_{s} v_{s}\left( 1-\alpha _{i}\right) L_{i}\):
\({\left\{ \begin{array}{ll} \mu _{{ Def}}(M_{s}|Rn)=\frac{1}{1-v_{s}}\left( 1-\frac{\left( 1-\beta _{i}\right) C_{i}}{\theta u_{s}\left( 1-\alpha _{i}\right) L_{i}}\right) \\ \mu _{At}(A|Ml)=\frac{C^{M}}{u_{s}\left( 1-v_{s}\right) \left( 1-\alpha _{i}\right) L_{i}} \end{array}\right. }\)
If \(\left( 1-\beta _{i}\right) C_{i} \ge \theta u_{s}\left( 1-\alpha _{i}\right) L_{i} \ge \theta u_{s} v_{s}\left( 1-\alpha _{i}\right) L_{i}\): \({\left\{ \begin{array}{ll} \mu _{{ Def}}(M_{s}|Rn)=0\\ \mu _{At}(A|Ml)=0 \end{array}\right. }\)
If \(v_{s} u_{s}\left( 1-\alpha _{i}\right) L_{i}+C^{M} \ge u_{s}\left( 1-\alpha _{i}\right) L_{i}\):
If \(\theta u_{s}\left( 1-\alpha _{i}\right) L_{i} \ge \theta u_{s} v_{s}\left( 1-\alpha _{i}\right) L_{i} \ge \left( 1-\beta _{i}\right) C_{i}\) or
\(\theta u_{s}\left( 1-\alpha _{i}\right) L_{i} \ge \left( 1-\beta _{i}\right) C_{i} \ge \theta u_{s} v_{s}\left( 1-\alpha _{i}\right) L_{i}\):
\({\left\{ \begin{array}{ll} \mu _{{ Def}}(M_{s}|Rn)=0\\ \mu _{At}(A|Ml)=1 \end{array}\right. }\)
If \(\left( 1-\beta _{i}\right) C_{i} \ge \theta u_{s}\left( 1-\alpha _{i}\right) L_{i} \ge \theta u_{s} v_{s}\left( 1-\alpha _{i}\right) L_{i}\):
\({\left\{ \begin{array}{ll} \mu _{{ Def}}(M_{s}|Rn)=0\\ \mu _{At}(A|Ml)=0 \end{array}\right. }\).
Rights and permissions
About this article
Cite this article
Kandoussi, E.M., Hanini, M., El Mir, I. et al. Toward an integrated dynamic defense system for strategic detecting attacks in cloud networks using stochastic game. Telecommun Syst 73, 397–417 (2020). https://doi.org/10.1007/s11235-019-00616-1
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11235-019-00616-1