Abstract
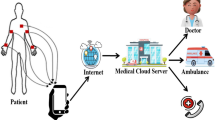
In recent years, wireless medical sensor networks meet the web to enable exciting healthcare applications that require data communication over the Internet. Often these applications suffer from data disclosure due to malicious users’ activities. To prevent such data disclosure in the healthcare systems, many public key cryptographic techniques have been used. However, most of them are too expensive to implement in the web-enabled wireless medical sensor networks. In 2013, Xun et al. introduced a lightweight encryption algorithm to protect communication between the sensor node and the data servers. Their scheme is based on the Sharemind framework. However, Sharemind framework has a limitation on the number of data storage servers (ie., three servers only). In addition, Xun et al’s scheme does not support privacy-preserving patient data analysis for distributed databases of different hospitals. In this paper, we introduce a new practical approach to prevent data disclosure from inside attack. Our new proposal is based on FairplayMP framework which enables programmers who are not experts in the theory of secure computation to implement such protocols. In addition, it support any number of n participants and is suitable for distributed environments. Moreover, in our new scheme, each sensor node needs only one secret key stored in advance to communicate with n different data servers, whereas three secret keys are embedded in advance into each sensor in order to communicate with three data servers in Xun et al’s scheme.



Similar content being viewed by others
Notes
Also known as ”honest but curious” adversaries. Adversaries of this type are assumed to follow the instructions that are prescribed for them by the protocol. They may, however, try to learn additional information from the messages that they receive
The identity of a user may be verified and authorized by verifying a digital signature signed from the user such as RSA signature or via a password based authentication system
References
Atzori, L., Iera, A., & Morabito, G. (2010). The internet of things: a survey. Computer Networks, 54(15), 2787–2805.
Bogdanov, D., Laur, S., & Willemson, J. (2008). Sharemind: a Framework for fast privacy-preserving computations. In Proceedings of 13th European Symposium on Research in Computer Security (ESORICS’08), LNCS, (Vol. 5282 pp. 192–206).
Beaver, D., Micali, S., & Rogaway, P. (1990). The round complexity of secure protocols. In Proceedings of the 22nd STOC conference (pp. 503–513).
Ben-David, A., Nisan, N., & Pinkas, B. (2008). Fairplaymp- a system for secure multi-party computation. In Proceedings of the 15th ACM conference on Computer and Commmunication Security (CCS’08) (pp. 27–31).
Domingo, M.C. (2012). An overview of the internet of things for people with disabilities. Journal of Network and Computer Applications, 35(2), 584–596.
Dagtas, S., Pekhteryev, G., Sahinoglu, Z., Cam, H., & Challa, N. (2008). Real-time and secure wireless health monitoring. International Journal of Telemedicine and Applications. doi:10.1155/2008/135808.
Huang, Y.M., Hsieh, M.Y., Hung, H.C., & Park, J.H. (2009). Pervasive, secure access to a hierarchical sensor-based healthcare monitoring architecuture in wireless heterogeneous networks. IEEE Journal on Selected Areas in Communications, 27, 400–411.
Kukuchi, H., Hashimoto, H., & Yasunaga, H. (2015). Privacy-preserving epidemiological analysis for distributed database of hospitals. In Proceedings of 10th Asia Joint Conference on Information Security (AsiaJCIS, (Vol. 2015 pp. 118–125).
Kumar, P., Lee, Y.D., & Lee, H.J. (2010). Secure health monitoring using medical wireless sensor networks. In Proceedings of 6th International Conference on Networked Computing and Advanced Information Management (pp. 491–494).
Katagi, M., & Shiho, M. (2008). Lightweight cryptography for the internet of things. Sony Corporation, 7–10.
Liu, Z., Day, R.D., & Swildens, E.S.J. (2014). Network traffic load balancing system using IPV6 mobility headers, U.S Patent No. 8, 819, 280.
Liu, Y., Goto, N, Karaoke, A., & Okamoto, E. (2015). Privacy preserved rule-based risk analysis through secure multi-party computation.
Liu, X., Gu, D., Yang, Z., & et al. (2014). Research on the IPv6 and sensor network based terrestrial ecosystem flux research network.
Le, X.H., Khalid, M., Sankar, R., & Lee, S. (2011). An efficient mutual authentication and access control scheme for wireless sensor network in healthcare. Journal of Networks, 27, 355–264.
Manifavas, C., Hatzivasilis, G., Fysarakis, K., & Rantos, K. (2014). Lightweight cryptography for embedded systemsA comparative analysis. In Data Privacy Management and Autonomous Spontaneous Security (pp. 333–349). Berlin, Heidelberg: Springer.
Muhammed, K., Lee, H., Lee, S., & Lee, Y.K. (2010). BARI+: A a biometric based sitributed key management approach for wireless body area networks. Sensors, 10, 3911–3933.
Misic, J., & Misic, V. (2008). Enforcing patient privacy in healthcare WSNs through key distribution algorithms. Security and Communication Networks, 1, 417–429.
Malasri, K., & Wang, L. (2009). Design and implementation of secure wireless mote-based medical sensor network. Sensors, 9, 6273–6297.
Yao, A. (1982). How to generate and exchange secrets. In Proceedings of 27th FOCS (pp. 162–167).
Yick, J., Mukherjee, B., & Ghosal, D. (2008). Wireless sensor network survey. Computer Networks, 52 (12), 2292–2330.
Yi, X., Willemson, J., & Nait-Abdesselam, F. (2013). Privacy-preserving wireless medical sensor network.
Zheng, L., Zhang, H., Han, W., & et al. (2011). Technologies, applications, and governance in the internet of things, Internet of Things-Global Technological and Societal Trends from Smart Environments and Spaces to Green Ict: River Publishers.
FirplayMP, http://www.cs.huji.ac.il/project/Fairplay, 2014.
FIPS PUB 180-4; Secure Hash Standard (SHS) http://csrc.nist.gov/publications/fips/fips180-4/fips-180-4.pdf.
NIST Selects Winner of Secure Hash Algorithm (SHA-3) Competition, http://www.nist.gov/itl/csd/sha-100212.dfm.
Introduction to Sharemind, http://sharemind.cyber.ee/introduction-to-sharemind.
Wiki: Internet of Things, https://en.wikipedia.org/wiki/Internet_of_Things.
Acknowledgments
The authors extend their appreciation to the Deanship of Scientific Research at King Saud University, Riyadh, Saudi Arabia for funding this work through the research group project No. RGP-318. R. Tso’s research was supported in part by Taiwan Information Security Center (TWISC), Academia Sinica, and Ministry of Science and Technology, Taiwan, under the grant MOST 104-2218-E-001-002 and MOST104-2221-E-004-007.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Tso, R., Alelaiwi, A., Mizanur Rahman, S.M. et al. Privacy-Preserving Data Communication Through Secure Multi-Party Computation in Healthcare Sensor Cloud. J Sign Process Syst 89, 51–59 (2017). https://doi.org/10.1007/s11265-016-1198-2
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11265-016-1198-2