Abstract
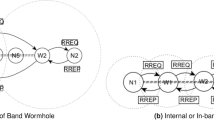
Wireless ad hoc networks are envisioned to be randomly deployed in versatile and potentially hostile environments. Hence, providing secure and uninterrupted communication between the un-tethered network nodes becomes a critical problem. In this paper, we investigate the wormhole attack in wireless ad hoc networks, an attack that can disrupt vital network functions such as routing. In the wormhole attack, the adversary establishes a low-latency unidirectional or bi-directional link, such as a wired or long-range wireless link, between two points in the network that are not within communication range of each other. The attacker then records one or more messages at one end of the link, tunnels them via the link to the other end, and replays them into the network in a timely manner. The wormhole attack is easily implemented and particularly challenging to detect, since it does not require breach of the authenticity and confidentiality of communication, or the compromise of any host. We present a graph theoretic framework for modeling wormhole links and derive the necessary and sufficient conditions for detecting and defending against wormhole attacks. Based on our framework, we show that any candidate solution preventing wormholes should construct a communication graph that is a subgraph of the geometric graph defined by the radio range of the network nodes. Making use of our framework, we propose a cryptographic mechanism based on local broadcast keys in order to prevent wormholes. Our solution does not need time synchronization or time measurement, requires only a small fraction of the nodes to know their location, and is decentralized. Hence, it is suitable for networks with the most stringent constraints such as sensor networks. Finally, we believe our work is the first to provide an analytical evaluation in terms of probabilities of the extent to which a method prevents wormholes.
Similar content being viewed by others
References
C. Balanis, Antenna Theory (John Wiley & Sons, 1982).
D. Bertsekas and R. Gallager, Data Networks (2nd ed.) (Prentice Hall, NJ, 1992).
C. Bettstetter, On the minimum node degree and connectivity of a wireless multihop network, in: Proceedings of the Third ACM International Symposium on Mobile Ad Hoc Networking & Computing, (Oct. 2002) pp. 80–91.
R.V. Boppana and S. Konduru, An adaptive distance vector routing algorithm for mobile Ad Hoc Networks, in: Proceedings of INFOCOM (April 2001) pp. 1753–1762.
S. Brands and D. Chaum, Distance-bounding protocols, in: Proceedings of Cryptography (Aug. 1994) Vol. 839 of Lecture Notes in Computer Science, pp. 344–359.
S. Çapkun, L. Buttyan, J. Hubaux, SECTOR: Secure tracking of node encounters in multi-hop wireless networks, in: Proceedings of Security of Ad Hoc and Sensor Networks (Oct. 2003) pp. 21–32.
S. Çapkun, and J.P. Hubaux, Secure positioning of wireless devices with application to sensor networks, in: IEEE INFOCOM 2005 (March 2005).
D. Carman, P. Kruus and B. Matt, Constraints and Approaches for Distributed Sensor Network Security, NAI Labs Technical Report No. 00-010 (2002).
H. Chan, A. Perrig and D. Song, Random key pre-distribution schemes for sensor networks, in: Proceedings of the IEEE Symposium on Research in Security and Privacy (May 2003) pp. 197–213.
D. Coppersmith and M. Jakobsson, Almost optimal hash sequence traversal, in: Proceedings of the Financial Cryptography (March 2002) Lecture Notes in Computer Science, IFCA, Springer-Verlag, Berlin, Germany.
N. Cressie, Statistics for Spatial Data (John Wiley & Sons, NY 1993).
W. Diffie and M.E. Hellman, New directions in cryptography, IEEE Transactions on Information Theory 22 (Nov. 1976) 644–654.
J. Douceur, The Sybil attack, in: Proceedings of IPTPS 2002 (March 2002).
L. Eschenauer and V. D. Gligor, A key-management scheme for distributed sensor networks, in: Proceedings of the Ninth ACM Conference on Computer and Communications Security (Nov. 2002) pp. 41–47.
A. Farago, Scalable analysis and design of ad hoc networks via random graph theory, in: Proceedings of the Sixth International Workshop on Discrete Algorithms and Methods for Mobile Computing and Communications (2002) pp. 43–50.
J. Gao, L. Guibas, J. Hershberger, L. Zhang, and A. Zhu, Geometric spanner for routing in mobile networks, in: Proceedings of the Second ACM International Symposium on Mobile Ad Hoc Networking & Computing (Oct. 2002) pp. 45–55.
T. He, C. Huang, B. Blum, J. Stankovic and T. Abdelzaher, Range-free localization schemes in large scale sensor networks, in: Proceedings of the Fourth ACM International Symposium on Mobile Ad Hoc Networking & Computing (Oct. 2004) pp. 81–95.
B. Hofmann-Wellenhof, H. Lichtenegger and J. Collins, Global Positioning System: Theory and Practice (4th ed.) (Springer-Verlag, Vienna, 1997).
L. Hu and D. Evans, Using directional antennas to prevent wormhole attacks, in: Proceedings of NDSS (Feb. 2004).
Y. Hu, A. Perrig and D. Johnson, Packet leashes: A defense against wormhole attacks in wireless ad hoc networks, in: Proceedings of INFOCOM (April 2003) vol. 2, 1976–1986.
Y. Hu, D. Johnson and A. Perrig, Rushing attacks and defense in wireless ad hoc network routing protocols, in: Proceedings of the ACM Workshop on Wireless Security (Sept. 2003) pp. 30–40.
D.B. Johnson, D.A. Maltz and J. Broch, The dynamic source routing protocol for multihop wireless ad hoc networks, in: Ad Hoc Networking, (Addison-Wesley, 2001), ch. 5, pp. 139–172.
F. Kuhn, R. Wattenhofer, Y. Zhang and A. Zollinger, Geometric routing: of theory and practice, in: Proceedings of the 22nd ACM Symposium on the Principles of Distributed Computing (PODC) (2003).
F. Kuhn, R. Wattenhofer and A. Zollinger, Asymptotically optimal geometric mobile ad-hoc routing, in: Proceedings of the Sixth International Workshop on Discrete Algorithms and Methods for Mobile Computing and Communications (DIAL-M), pp. 24–33.
C. Karlof and D. Wagner, Secure routing in wireless sensor networks: Attacks and countermeasures, in: Proceedings of WSNA (May 2003) pp. 113–127.
L. Lamport, Password authentication with insecure communication, Communications of the ACM, 24, (Nov. 1981), 770–772.
L. Lazos and R. Poovendran, SeRLoc: Secure range-independent localization for wireless sensor networks, in: Proceedings ACM WiSe (Oct. 2004).
L. Lazos, S. Çapkun and R. Poovendran, ROPE: Robust position estimation in wireless sensor networks, in: The Fourth International Conference on Information Processing in Sensor Networks (IPSN 2005) (April 2005).
Z. Li, W. Trappe, Y. Zhang and B. Nath, Robust statistical methods for securing wireless localization in sensor networks, in: The Fourth International Conference on Information Processing in Sensor Networks (IPSN 2005) (April 2005).
D. Liu and P. Ning, Attack-resistant location estimation in sensor networks, in: The Fourth International Conference on Information Processing in Sensor Networks (IPSN 2005) (April 2005).
MICA Wireless Measurement System, available at: http://www.xbow.com/Products/Product_pdf_files/Wireless_pdf/MICA.pdf.
S. Murthy and J.J. Garcia-Luna-Aceves, An efficient routing protocol for wireless networks, ACM Mobile Networks and App. J., Special Issue on Routing in Mobile Communication Networks (Oct. 1996) pp. 183–97.
J. Newsome, E. Shi, D. Song and A. Perrig, The Sybil attack in sensor networks: Analysis and defenses, in: Proceedings of IPSN 2004, Berkeley, CA (April 2004).
P. Papadimitratos and Z.J. Haas, Secure routing for mobile ad hoc networks, in: Proceedings of CNDS 2002 (Jan. 2002).
M. Penrose, Random Geometric Graphs (Oxford University Press, NY, 2003).
C.E. Perkins and P. Bhagwat, Highly dynamic destination-sequenced distance-vector routing (DSDV) for mobile computers, in: Proceedings of the SIGCOMM (Aug. 1994) pp. 234–244.
C.E. Perkins and E.M. Royer, Ad-hoc on-demand distance vector routing, in: Proceedings of WMCSA (Feb. 1999) pp. 90–100.
A. Perrig, R. Canetti, J. Tygar and D. Song, The TESLA broadcast authentication protocol, RSA Cryptobytes, 5(2), Summer 2002.
A. Perrig, R. Szewczyk, V. Wen, D. Culler and J. Tygar, SPINS: Security protocols for sensor networks, in: Proceedings of MOBICOM 2001, Rome, Italy (July 2001).
J. Proakis, Digital Communications (4th ed.) (McGraw Hill Inc., 2001).
R.L. Rivest, The RC5 encryption algorithm, in: Proceedings of the First Workshop on Fast Software Encryption (Dec. 1994) pp. 86–96.
R.L. Rivest, A. Shamir and L.M. Adleman, A method for obtaining digital signatures and public-key cryptosystems, Communications of the ACM 21 (Jan. 1978) 120–126.
A. Savvides, C. Han and M. Srivastava, Dynamic fine-grained localization in ad-hoc networks of sensors, in: Proceedings of MOBICOM (July 2001) pp. 166–179.
Y. Shang, W. Ruml, Y. Zhang and M. Fromherz, Localization from mere connectivity, in: Proceedings of MOBIHOC (June 2003) pp. 201–212.
D. Stinson, Cryptography: Theory and Practice (2nd ed.) (CRC Press, 2002).
S. Zhu, S. Setia and S. Jahodia, LEAP: Efficient security mechanisms for large-scale distributed sensor networks, in: Proceedings of CCS (Oct. 2003) pp. 62–72.
W. Wang and B. Barhgava, Visualization of wormholes in sensor networks, in: Proceedings of WISE 2004 (Oct. 2004).
R. Wattenhofer, L. Li, P. Bahl, and Y.-M. Wang, Distributed topology control for power efficient operation in multihop wireless ad hoc networks, in: Proceedings of the 20th Annual Joint Conference of the IEEE Computer and Communications Societies (INFOCOM) (2001) pp. 1388–1397.
Author information
Authors and Affiliations
Corresponding author
Additional information
Radha Poovendran received the Ph.D. degree in electrical engineering from the University of Maryland, College Park, in 1999. He has been an Assistant Professor in the Electrical Engineering Department, University of Washington, Seattle, since September 2000. His research interests are in the areas of applied cryptography for multiuser environment, wireless networking, and applications of information theory to security. Dr. Poovendran is a recipient of the Faculty Early Career Award from the National Science Foundation (2001), Young Investigator Award from the Army Research Office (2002), Young Investigator Award from the Office of Naval Research (2004), and the 2005 Presidential Early Career Award for Scientists and Engineers, for his research contributions in the areas of wired and wireless multiuser security.
Loukas Lazos received the B.S. and M.S. degrees from the Electrical Engineering Department, National Technical University of Athens, Athens, Greece, in 2000 and 2002, respectively. He is currently working towards the Ph.D. degree in the Electrical Engineering Department, University of Washington, Seattle. His current research interests focus on cross-layer designs for energy-efficient key management protocols for wireless ad-hoc networks, as well as secure localization systems for sensor networks.
Rights and permissions
About this article
Cite this article
Poovendran, R., Lazos, L. A graph theoretic framework for preventing the wormhole attack in wireless ad hoc networks. Wireless Netw 13, 27–59 (2007). https://doi.org/10.1007/s11276-006-3723-x
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-006-3723-x