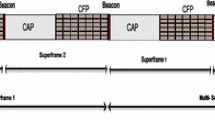
Abstract
This paper introduces a new 4D Markov chain model for IEEE 802.15.4 wireless transmission, which corrects and extends an existing 3D model, providing more accurate and comprehensive results. It also introduces an analytical technique for calculating both the pdf and mean of the number of timeslots required to complete all transmissions, when a set of nodes contend for the channel at the beginning of a superframe. It is assumed that transmission takes place in beacon mode but without acknowledgement (NACK mode). The model can be used to determine the optimum value of the MAC attribute macSuperframeOrder (SO) required for saving energy, and the shortest delay required to receive all transmitted packets with a specified probability. It can also specify an upper threshold on the number of nodes and the packet length required, in order to achieve acceptable end-to-end delay. The potential creation of a traffic model for the aggregated data generated by the coordinating node is also discussed.









Similar content being viewed by others
References
Bender, M. A., Farach-Colton, M., He, S., Kuszmaul, B. C., & Leiserson, C. E. (2005). Adversarial contention resolution for simple channels, ACM Symposium on parallelism in algorithms and architectures (SPAA), pp. 325–332.
Foh, C., & Zukerman, M. (2001). Performance evaluation of IEEE 802.11, IEEE vehicular technology conference (VTC) (pp. 841–845), Spring, vol. 2.
Yedavalli, K., & Krishnamachari, B. (2006). Enhancement of the IEEE 802.15.4 MAC protocol for scalable data collection in dense sensor networks, Technical report CENG-2006-14, University of Southern California, Computer Engineering.
Tay, Y. C., Jamieson, K., & Balakrishnan, H. (2004). Collision-minimizing CSMA and its applications to wireless sensor networks. IEEE Journal on Selected Areas in Communications, 22(6), 1048–1057.
Szewczyk, R., Osterweil, E., Polastre, J., Hamilton, M., Mainwaring, A., & Estrin, D. (2004). Habitat monitoring with sensor networks. Communications of the ACM, 47(6), 34–40.
Wu, Y., Fahmy, S., & Shroff, N. B. (2006). Optimal sleep/wake scheduling for time-synchronized sensor networks with QoS guarantees, IEEE international workshop on quality of service (IWQoS).
IEEE Standard 802.15.4-2006. (2006). IEEE, New York, NY.
Kim, T. H., & Choi, S. (2006). Priority-based delay mitigation for event monitoring IEEE 802.15.4 LR-WPANs. IEEE Communications Letters, 10(3), 213–215.
Ramachandran, I., Das, A. K., Roy, S. Analysis of the contention access period of IEEE 802.15.4 MAC, ACM Transactions on Sensor Networking, vol. 3, no. 1 (article 4).
Lu, G., Krishnamachari, B., & Raghavendra, C. (2004). Performance evaluation of the IEEE 802.15.4 MAC for low-rate low-power networks, IEEE ICPCC.
Bougard, B., Catthoor, F., Daly, D. C., Chandrakasan, A.,& Dehaene, W. (2005). Energy efficiency of the IEEE 802.15.4 standard in dense wireless microsensor networks: modeling and improvement perspectives, Design Automation and Test in Europe, pp. 196–201.
Zheng, J., & Lee, M. J. (2004). Will IEEE 802.15.4 make ubiquitous networking a reality? A discussion on a potential low power, low bit rate standard. IEEE Communications Magazine, 42, 140–146.
Ling, X., Cheng, Y., Mark, J. W., & Shen, X. (2008). A renewal theory based analytical model for the contention access period of IEEE 802.15.4 MAC, IEEE Transactions on Wireless Communications, vol. 7, no. 6.
Pollin, S., Ergen, M., Ergen, S., Bougard, B., Der Perre, L., Moerman, I., et al. (2008). Performance analysis of slotted carrier sense IEEE 802.15.4 medium access layer. IEEE Transactions on Wireless Communications, 7(9), 3359–3371.
Tao,Z., Panwar, S., Gu, D., & Zhang, J. (2006). Performance analysis and a proposed improvement for the IEEE 802.15.4 contention access period, IEEE WCNC, pp. 1811–1818.
Park, T. R., Kim, T. H., Choi, J. Y., Choi, S., & Kwon, W. H. (2005). Throughput and energy consumption analysis of IEEE 802.15.4 Slotted CSMA/CA, Electronics Letters.
Ramachandran, I., Das, A. K., & Roy, S. (2006). Analysis of the contention access period of IEEE 802.15.4 MAC, University of Washington technical report UWEETR-2006-0003.
Misic, J., Shafi, S., & Misic, V. B. (2005). The impact of MAC parameters on the performance of 802.15.4 PAN. Ad-hoc Networks, 3(5), 509–528.
Bianchi, G. (2000). Performance analysis of the IEEE 802.11 distributed coordination function. IEEE Journal on Selected Areas in Communications, 18, 535–547.
Shu, F., Sakurai, T., Zukerman, M., & Vu, H. L. (2007). Packet loss analysis of the IEEE 802.15.4 MAC without acknowledgements, IEEE Communications Letters, vol. 11, no. 1.
Open-ZB (2010). OpenSource toolset for IEEE 802.15.4 and ZigBee, http://www.open-zb.net. Accessed 10 Nov 2010.
Li, X., Bleakley, C. J., & Bober, W. (2011). Enhanced beacon enabled mode for improved IEEE 802.15.4 low data rate performance, To appear in Springer wireless networks. doi:10.1007/s11276-011-0387-y.
Molle, M. (1994). A new binary logarithmic arbitration method for ethernet, technical report CSRI-298, Canada: Computer Systems Research Institute, University of Toronto.
Acknowledgments
This work was funded by the UK Engineering and Physical Sciences Research Council (EPSRC) under the TRAMSNOD project.
Author information
Authors and Affiliations
Corresponding author
Appendix
Appendix
The attempt probability has been successfully used to analyze the truncated binary exponential backoff algorithm in both Ethernet [23] and in the IEEE 802.11 Distributed Coordination Function. This is the probability that an IEEE 802.15.4 node senses the channel or makes an attempt to access it in a particular slot n. Assuming the channel is always busy before the current timeslot n, it can be approximated as [20]:
where M is equal to macMaxCSMABackoffs, and P n (m) denotes the attempt probability that a node chooses slot n for its mth attempt:
where W min = 2macMinBE, and W = min(2m W min, 2macMaxBE). Figure 10 shows P n for macMinBE = 2 and macMinBE = 3, with macMaxBE = 5. Figure 11 shows P n (m) and P n for macMinBE = 3 and macMaxBE = 5.
Rights and permissions
About this article
Cite this article
Li, X., Hunter, D.K. Four-dimensional Markov chain model of single-hop data aggregation with IEEE 802.15.4 in wireless sensor networks. Wireless Netw 18, 469–479 (2012). https://doi.org/10.1007/s11276-011-0412-1
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-011-0412-1