Abstract
In this paper, we study the throughput stability, mean queueing delay and energy consumption issues of IEEE 802.15.4 MAC protocol. We model the network as a multi-queue single-server system and derive the service time distribution of head-of-line packets from a Markov Chain of beacon-enable mode in an unsaturated traffic environment. Two transmission schemes of uplink traffic, the non-acknowledged transmission and acknowledged transmission, are studied with probabilistic exponential backoff scheduling algorithm. We obtain the characteristic equation of network throughput and power consumptions of each node in closed form, from which the stable throughput region and bounded mean delay region are specified with respect to the retransmission factor. Furthermore, we also show that the energy consumption of each node can be kept small within the stable throughput region. All analytical results presented in this paper are verified by simulations.












Similar content being viewed by others
References
Yick, J., Mukherjee, B., & Ghosal, D. (2008). Wireless sensor network survey. Computer Networks, 52(12), 2292–2330.
Zheng, J., & Lee, M. J. (2004). Will IEEE 802.15.4 make ubiquitous networking a reality? A discussion on a potential low power, low bit rate standard. IEEE Communications Magazine, 42(6), 140–146.
Zheng, J., & Lee, M. J. (2004). A comprehensive performance study of IEEE 802.15.4. Piscataway: IEEE Press Book.
Golmie, N., & Cypher, D. (2005). Performance analysis of low rate wireless technologies for medical applications. Computer Communications, 28, 1266–1275.
Chen, F., Wang, N., German, R., & Dressler, F. (2010). Simulation study of IEEE 802.15.4 LR-WPAN for industrial applications. Wireless Communications & Mobile Computing, 10(5), 609–621.
Lu, G., Krishnamachari, B., & Raghavendra, C. S. (2004). Performance evaluation of the IEEE 802.15.4 MAC for low-rate low-power wireless networks. In Proceedings of workshop on energy-efficient wireless communications and networks (EWCN’04).
Bianchi, G. (2000). Performance analysis of the IEEE 802.11 distributed coordination function. IEEE Journal of selected areas in COMMUN, 18(3), 535–547.
Park, T. R., Kim, T. H., Choi, J. Y., Choi, S., & Kwon, W. H. (2005). Throughput and energy consumption analysis of IEEE 802.15.4 slotted CSMA/CA. Electronics Letters, 41, 1017–1019.
Tao, Z. et al. (2006). Performance analysis and a proposed improvement for the IEEE 802.15.4 contention access period. In Proceedings of the IEEE WCNC.
He, J., Tang, Z., Chen, H.H., & Wang, S. (2008). An accurate Markov model for slotted CSMA/CA algorithm in IEEE 802.15.4 networks. IEEE Communication Letters, 12(6), 420–422.
He, J., Tang, Z., Chen, H.-H., & Zhang, Q. (2009). An accurate and scalable analytical model for IEEE 802.15.4 slotted CSMA/CA networks. IEEE Transactions on Wireless Communications, 8(1), 440–448.
Ramachandran, I., Das, A. K., Roy, S. (2006). Analysis of the contention access period of IEEE 802.15.4 MAC. University of Washington, technical report. UWEETR-2006-0003.
Misic, J., Shafi, S., & Misic, V. B. (2005). The impact of MAC parameters on the performance of 802.15.4 PAN. Ad Hoc Networks, 3(5), 509–528.
Misic, J., Shafi, S., & Misic, V. B. (2006). Performance of a beacon enabled 802.15.4 cluster with downlink & uplink traffic. IEEE Transactions on Parallel Distribution System, 17(4), 361–374.
Pollin, S., Ergen, M., Ergen, S., Bougard, B., Van der Perre, L., Moerman, I., et al. (2008). Performance analysis of slotted carrier sense IEEE 802.15.4 medium access layer. IEEE Transactions on Wireless Communications, 7(9), 3359–3371.
Park, P., Marco, P. D., Soldati, P., Fischione, C., & Johansson, K. H. (2009). A generalized Markov Chain model for effective analysis of slotted IEEE 802.15.4. In Proceedings of IEEE MASS.
Park, P., Fischione, C., & Johansson, K. H. (2010). Adaptive IEEE 802.15.4 protocol for energy efficient, reliable and timely communications. In Proceedings of ACM/IEEE IPSN.
Zhu, J., Tao, Z., & Lv, C. (2011). Performance evaluation of IEEE 802.15. 4 CSMA/CA scheme adopting a modified LIB model. Wireless Personal Communications, 65(1), 25–51.
King Wong, P., Yin, D., & Lee, T. T. (2011). Analysis of non-persistent CSMA protocols with exponential backoff scheduling. IEEE Transactions on Communications, 59(8), 2206–2214.
Kwok, B.-J., Song, N.-O., & Miller, L. E. (2003). Analysis of the stability and performance of exponential backoff. IEEE Wireless Communications and Networking, 3, 1754–1759.
Song, N. O., Kwak, B. J., & Miller, L. E. (2003). On the stability of exponential backoff. Journal of Research of the National Institute of Standards and Technology, 108, 289–297.
Goodman, J., Greenberg, A. G., Madras, N., & March, P. (1988). Stability of binary exponential backoff. Journal of ACM, 35, 579–602.
Hastad, J., Leighton, T., & Rogoff, B. (1996). Analysis of backoff protocols for multiple access channels. SIAM Journal on Computing, 25, 740–744.
Al-Ammal, H., Goldberg, L. A., & MacKenzie, P. (2001). An improved stability bound for binary exponential backoff. Theory Computing Systems, 30, 229–244.
Cali, F., Conti, M., & Gregori, E. (2000). Dynamic tuning of the IEEE 802.11 protocol to achieve a theoretical throughput limit. IEEE/ACM Transactions on Networking, 8, 785–799.
Cinlar, E., & Agnew, R. A. (1968). On the superposition of point processes. Journal of the Royal Statistical Society: Series B, 30(3), 576–581.
Takagi, H. (1993). Queueing analysis: Discrete-time systems (Vol. 3). North-holland: A Foundation of Performance Evaluation.
Author information
Authors and Affiliations
Corresponding author
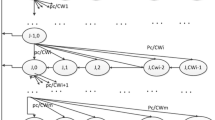
Appendix 1: Service time distribution for IEEE 802.15.4
Appendix 1: Service time distribution for IEEE 802.15.4
Since the service of each HOL packet starts from state \( CCA_{0}^{1} \), therefore the first and second moments of service time, E[X] and E[X 2], can be derived from the generating function \( CCA_{0}^{1} (z). \) We take the first and second derivatives of (12), and then can solve the set of simultaneous equations for the first and second moments of the service time of HOL packets with exponential backoff scheme as follows:
where
and
Rights and permissions
About this article
Cite this article
Yin, D., Lee, T.T. Performance analysis of markov modulated IEEE 802.15.4 beacon-enable mode. Wireless Netw 19, 1709–1724 (2013). https://doi.org/10.1007/s11276-013-0565-1
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-013-0565-1