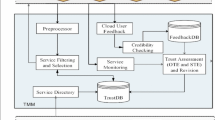
Abstract
Cloud computing, a new paradigm in distributed computing, has gained wide popularity in a relatively short span of time. With the increase in the number, functionality and features of cloud services, it is more and more mind-boggling for the cloud users to find a trustworthy provider. Cloud users need to have confidence in cloud providers to migrate their critical data to cloud computing. There must be some means to determine reliability of service providers so that users can choose services with the assurance that the provider will not act malignantly. An effort has been made in this paper to formulate a hybrid model to calculate the trustworthiness of service providers. Cloud services are evaluated and trust value is calculated based on compliance and reputation. Service logs based compliance reflects dynamic trust. The reputation has been computed from collective user feedback. Feedback rating is the view of each user about the invoked services. The discovered services that fulfill the user requirements are ranked based on their trust values and top-k cloud services are recommended to the user. The proposed approach is efficient and considerably improves service-selection process in cloud applications.







Similar content being viewed by others
References
Mashayekhy, L., Nejad, M. M., Grosu, D., & Vasilakos, A. V. (2014) Incentive-compatible online mechanisms for resource provisioning and allocation in clouds. In IEEE 7th international conference on cloud computing (CLOUD) (pp. 312–319).
Mashayekhy, L., Nejad, M. M., Grosu, D., & Vasilakos, A. (2015). An online mechanism for resource allocation and pricing in clouds. IEEE Transactions on Computers. doi:10.1109/TC.2015.2444843.
Rahimi, M. R., Ren, J., Liu, C. H., Vasilakos, A. V., & Venkatasubramanian, N. (2014). Mobile cloud computing: A survey, state of art and future directions. Mobile Networks and Applications, 19(2), 133–143.
Wei, L., Zhu, H., Cao, Z., Dong, X., Jia, W., Chen, Y., & Vasilakos, A. V. (2014). Security and privacy for storage and computation in cloud computing. Information Sciences, 258, 371–386.
Ali, M., Khan, S. U., & Vasilakos, A. V. (2015). Security in cloud computing: Opportunities and challenges. Information Sciences, 305, 357–383.
Jøsang, A., Ismail, R., & Boyd, C. (2007). A survey of trust and reputation systems for online service provision. Decision Support Systems, 43(2), 618–644.
Noor, T. H., Sheng, Q. Z., Yao, L., Dustdar, S., & Ngu, A. H. H. (2015). CloudArmor: Supporting reputation-based trust management for cloud services. IEEE Transactions on Parallel and Distributed Systems. doi:10.1109/TPDS.2015.2408613.
Noor, T. H., Sheng, Q. Z., Zeadally, S., & Jian, Y. (2013). Trust management of services in cloud environments: Obstacles and solutions. ACM Computing Surveys, 46(1), 12.
Firdhous, M., Ghazali, O., & Hassan, S. (2011) Trust and trust management in cloud computing: A survey. InterNetWorks Research Group, University Utara Malaysia, Technical Report No: UUM/CAS/InterNetWorks/TR2011-01.
Habib, S. K., Ries, S., & Muhlhauser, M. (2011) Towards a trust management system for cloud computing. In Proceedings of IEEE 10th international conference on trust, security. Privacy Comput. Commun., (pp. 933–939).
Deng, S., Bin, W., & Zhaohui, W. (2013). Efficient planning for Top-K web service composition. Knowledge and Information Systems, 36(3), 579–605.
Yan, Z., Zhang, P., & Vasilakos, A. V. (2014). A survey on trust management for internet of things. Journal of Network and Computer Applications, 42, 120–134.
Khan, K., & Malluhi, Q. (2010). Establishing trust in cloud computing. IT Professional, 12(5), 20–27.
Huang, J., & Nicol, D. M. (2013). Trust mechanisms for cloud computing. Journal of Cloud Computing, 2(1), 1–14.
Alhamad, M., Dillon, T., & Chang, E. (2010) Sla-based trust model for cloud computing. In 13th international conference on network-based information systems (NBiS) (pp. 321–324).
Sato, H., Kanai, A., & Tanimoto, S. (2010). A cloud trust model in a security aware cloud. In 10th IEEE/IPSJ international symposium on applications and the internet (SAINT), Seoul, South Korea (pp. 121–124).
Chen, C., Li, X., & Bai, Z. (2012) A BPNN-based dynamic trust predicting model for distributed systems. In 3rd IEEE international conference on network infrastructure and digital content (ICNIDC), Beijing (pp. 601–605).
Li, X., & Du, J. (2013). Adaptive and attribute-based trust model for service-level agreement guarantee in cloud computing. IET Information Security, 7(1), 39–50.
Muchahari, M. K., & Sinha, S. K. (2012) A new trust management architecture for cloud computing environment. In International symposium on cloud and services computing (pp. 136–140).
Fan, W., Yang, S., & Pei, J. (2014). A novel two-stage model for cloud service trustworthiness evaluation. Expert Systems, 31(2), 136–153.
Noor, T. H., Sheng, Q. (2011) Trust as a service: A framework for trust management in cloud environments. In Web information system engineering WISE 2011, ser. Lecture Notes in Computer Science (Vol. 6997, pp. 314–321). Heidelberg: Springer.
Goyal, M. K., Aggarwal, A., Gupta, P., & Kumar, P. (2012) QoS based trust management model for cloud IaaS. In Proceedings of second IEEE international conference on parallel distributed and grid computing (PDGC) (pp. 843–847).
Zhang, H., Li, B., Jiang, H., Liu, F., Vasilakos, A. V. & Liu, J. (2013) A framework for truthful online auctions in cloud computing with heterogeneous user demands. In Proceedings IEEE of INFOCOM (pp. 1510–1518).
Supriya, M., Venkataramana, L. J., Sangeeta, K., & Patra, G. K. (2012). Estimating trust value for cloud service providers using fuzzy logic. International Journal of Computer Applications, 48(19), 28–34.
Mahbub, H. S., Ries, S., Mühlhäuser, M., & Varikkattu, P. (2014). Towards a trust management system for cloud computing marketplaces: Using caiq as a trust information source. Security and Communication Networks, 7(11), 2185–2200.
Singh, S., & Chand, D. (2014) Trust evaluation in cloud based on friends and third party’s recommendations. In Engineering and computational sciences (RAECS), recent advances in IEEE (pp. 1–6).
Mohammed, A., Dillon, T., & Chang, E. (2011). Trust-evaluation metric for cloud applications. International Journal of Machine Learning and Computing, 1(4), 416–421.
Alabool, H. M., & Mahmood, A. K. (2013). Trust-based service selection in public cloud computing using fuzzy modified VIKOR method. Australian Journal of Basic and Applied Sciences, 7(9), 211–220.
Ghosh, N., Ghosh, S. K., & Das, S. K. (2015). SelCSP: A framework to facilitate selection of cloud service providers. IEEE Transactions on Cloud Computing, 3(1), 66–79.
CSA Cloud Security Alliance) STAR (security, trust and assurance registry) program. https://cloudsecurityalliance.org/star/.
Wei, L., Zhu, H., Cao, Z., & Jia, W., & Vasilakos, A. V. (2010) Seccloud: Bridging secure storage and computation in cloud. In IEEE 30th international conference on distributed computing systems workshops (ICDCSW) (pp. 52–61).
Rahimi, M. R., Venkatasubramanian, N., Mehrotra, S., & Vasilakos, A. V. (2012). MAPCloud: Mobile applications on an elastic and scalable 2-tier cloud architecture. In Proceedings of the 2012 IEEE/ACM fifth international conference on utility and cloud computing, IEEE Computer Society (pp. 83–90).
Liu, B., Bi, J., & Vasilakos, A. V. (2014). Toward incentivizing anti-spoofing deployment. IEEE Transactions on Information Forensics and Security, 9(3), 436–450.
Fadlullah, Z. M., Taleb, T., Vasilakos, A. V., Guizani, M., & Kato, N. (2010). DTRAB: Combating against attacks on encrypted protocols through traffic-feature analysis. IEEE/ACM Transactions on Networking (TON), 18(4), 1234–1247.
Cisar, P., & Cisar, S. M. (2011). Optimization methods of EWMA statistics. Acta Polytechnica Hungarica, 8(5), 73–87.
Roberts, S. W. (2000). Control chart tests based on geometric moving averages. Technometrics, 42(1), 97–101.
Chakraborty. S., & Roy, K. (2012) An SLA-based framework for estimating trustworthiness of a cloud. In IEEE 11th international conference trust, security and privacy in computing and communications (TrustCom) (pp. 937–942).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Viji Rajendran, V., Swamynathan, S. Hybrid model for dynamic evaluation of trust in cloud services. Wireless Netw 22, 1807–1818 (2016). https://doi.org/10.1007/s11276-015-1069-y
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-015-1069-y