Abstract
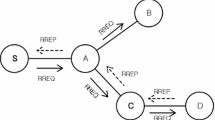
Delay tolerant networks (DTNs) are characterized by delay and intermittent connectivity. Satisfactory network functioning in a DTN relies heavily on co-ordination among participating nodes. However, in practice, such co-ordination cannot be taken for granted due to possible misbehaviour by relay nodes. Routing in a DTN is, therefore, vulnerable to various attacks, which adversely affect network performance. Several strategies have been proposed in the literature to alleviate such vulnerabilities—they vary widely in terms of throughput, detection time, overhead etc. One key challenge is to arrive at a tradeoff between detection time and overhead. We observe that the existing table-based reactive strategies to combat Denial-of-service (DoS) attacks in DTN suffer from two major drawbacks: high overhead and slow detection. In this paper, we propose three secure, light-weight and time-efficient routing algorithms for detecting DoS attacks (Blackhole and Grey-hole attacks) in the Spray & Focus routing protocol. The proposed algorithms are based on use of a small fraction of privileged (trusted) nodes. The first strategy, called TN, outperforms the existing table-based strategy with 20–30 % lesser detection time, 20–25 % higher malicious node detection and negligible overhead. The other two strategies, CTN_MI and CTN_RF explore the novel idea that trusted nodes are able to utilize each others’ information/experience using their long range connectivity as and when available. Simulations performed using an enhanced ONE simulator reveals that investing in enabling connectivity among trusted nodes (as in CTN_RF) can have significant performance benefits.












Similar content being viewed by others
References
Bettstetter, C., Resta, G., & Santi, P. (2003). The node distribution of the random waypoint mobility model for wireless ad hoc networks. Mobile Computing, IEEE Transactions on, 2(3), 257–269.
Burgess, J., Gallagher, B., Jensen, D., & Levine, B. N. (2006). Maxprop: Routing for vehicle-based disruption-tolerant networks. INFOCOM, 6, 1–11.
Chuah, M., Yang, P., & Han, J. (2007). A ferry-based intrusion detection scheme for sparsely connected ad hoc networks. In Mobile and Ubiquitous Systems: Networking & Services, 2007. MobiQuitous 2007. Fourth Annual International Conference on (pp. 1–8). IEEE.
Dvir, A., & Vasilakos, A. V. (2010). Backpressure-based routing protocol for DTNs. In Proceedings of the ACM SIGCOMM 2010 Conference, SIGCOMM ’10 (pp. 405–406). New York, NY: ACM. doi:10.1145/1851182.1851233.
E-one for security. http://www.nitdgp.ac.in/MCN-RG/eONE/security/security.html.
Fall, K. (2003). A delay-tolerant network architecture for challenged internets. In Proceedings of the 2003 Conference on Applications, Technologies, Architectures, and Protocols for Computer Communications (pp. 27–34). ACM.
Guo, Y., Schildt, S., & Wolf, L. (2013). Detecting blackhole and greyhole attacks in vehicular delay tolerant networks. In Communication Systems and Networks (COMSNETS), 2013 Fifth International Conference on (pp. 1–7). IEEE.
Jing, Q., Vasilakos, A. V., Wan, J., Lu, J., & Qiu, D. (2014). Security of the internet of things: Perspectives and challenges. Wireless Networks, 20(8), 2481–2501. doi:10.1007/s11276-014-0761-7.
Keränen, A., Ott, J., & Kärkkäinen, T. (2009). The one simulator for dtn protocol evaluation. In Proceedings of the 2nd International Conference on Simulation Tools and Techniques (p. 55). Institute for Computer Sciences, Social-Informatics and Telecommunications Engineering (ICST).
Li, F., Wu, J., & Srinivasan, A. (2009). Thwarting blackhole attacks in disruption-tolerant networks using encounter tickets. In INFOCOM 2009, IEEE (pp. 2428–2436). IEEE.
Li, Q., Zhu, S., & Cao, G. (2010). Routing in socially selfish delay tolerant networks. In INFOCOM, 2010 Proceedings IEEE (pp. 1–9). IEEE.
Lindgren, A., Doria, A., & Schelén, O. (2003). Probabilistic routing in intermittently connected networks. ACM SIGMOBILE Mobile Computing and Communications Review, 7(3), 19–20.
Liu, B., Bi, J., & Vasilakos, A. V. (2014). Toward incentivizing anti-spoofing deployment. Information Forensics and Security, IEEE Transactions on, 9(3), 436–450.
Liu, J., Li, Y., Wang, H., Jin, D., Su, L., Zeng, L., et al. (2016). Leveraging software-defined networking for security policy enforcement. Information Sciences, 327, 288–299. doi:10.1016/j.ins.2015.08.019.
Lu, R., Lin, X., Zhu, H., Shen, X. S., & Preiss, B. (2010). Pi: A practical incentive protocol for delay tolerant networks. Wireless Communications, IEEE Transactions on, 9(4), 1483–1493.
Ning, T., Yang, Z., Xie, X., & Wu, H. (2011). Incentive-aware data dissemination in delay-tolerant mobile networks. In Sensor, Mesh and Ad Hoc Communications and Networks (SECON), 2011 8th Annual IEEE Communications Society Conference on (pp. 539–547). IEEE.
Ren, Y., Chuah, M. C., Yang, J., & Chen, Y. (2010). Muton: Detecting malicious nodes in disruption-tolerant networks. In Wireless Communications and Networking Conference (WCNC), 2010 IEEE (pp. 1–6). IEEE.
Ren, Y., Chuah, M. C., Yang, J., & Chen, Y. (2010). Detecting wormhole attacks in delay-tolerant networks [security and privacy in emerging wireless networks]. Wireless Communications, IEEE, 17(5), 36–42.
Saha, S., Nandi, S., Paul, P. S., Shah, V. K., Roy, A., & Das, S. K. (2015). Designing delay constrained hybrid ad hoc network infrastructure for post-disaster communication. Ad Hoc Networks, 25 (Part B), 406–429. doi:10.1016/j.adhoc.2014.08.009. http://www.sciencedirect.com/science/article/pii/S1570870514001802. New Research Challenges in Mobile, Opportunistic and Delay-Tolerant NetworksEnergy-Aware Data Centers: Architecture, Infrastructure, and Communication.
Saha, S., Verma, R., Sengupta, S., Mishra, V., & Nandi, S. (2012). SRSnF: a strategy for secured routing in spray and focus routing protocol for DTN. In Advances in Computing and Information Technology (pp. 159–169). Springer.
Shu, Z., Wan, J., Li, D., Lin, J., Vasilakos, A. V., & Imran, M. (2016). Security in software-defined networking: Threats and countermeasures. Mobile Networks and Applications. doi:10.1007/s11036-016-0676-x.
Spyropoulos, T., Psounis, K., & Raghavendra, C. S. (2007). Spray and focus: Efficient mobility-assisted routing for heterogeneous and correlated mobility. In Pervasive Computing and Communications Workshops, 2007. PerCom Workshops’ 07. Fifth Annual IEEE International Conference on, pp. 79–85. IEEE.
Spyropoulos, T., Rais, R. N. B., Turletti, T., Obraczka, K., & Vasilakos, A. (2010). Routing for disruption tolerant networks: Taxonomy and design. Wireless Networks, 16(8), 2349–2370. doi:10.1007/s11276-010-0276-9.
The one simulator. http://www.netlab.tkk.fi/tutkimus/dtn/theone/.
Vasilakos, A. V., Zhang, Y., & Spyropoulos, T. (2011). Delay tolerant networks: Protocols and applications (1st ed.). Boca Raton, FL: CRC Press Inc.
Yang, H., Zhang, Y., Zhou, Y., Fu, X., Liu, H., & Vasilakos, A. V. (2014). Provably secure three-party authenticated key agreement protocol using smart cards. Computer Networks, 58, 29–38.
Yao, G., Bi, J., & Vasilakos, A. V. (2015). Passive IP traceback: Disclosing the locations of IP spoofers from path backscatter. Information Forensics and Security, IEEE Transactions on, 10(3), 471–484.
Zeng, Y., Xiang, K., Li, D., & Vasilakos, A. V. (2013). Directional routing and scheduling for green vehicular delay tolerant networks. Wireless Networks, 19(2), 161–173. doi:10.1007/s11276-012-0457-9.
Zhou, J., Dong, X., Cao, Z., & Vasilakos, A. V. (2015). Secure and privacy preserving protocol for cloud-based vehicular DTNs. IEEE Transactions on Information Forensics and Security, 10(6), 1299–1314.
Zhu, H., Lin, X., Lu, R., Fan, Y., & Shen, X. (2009). Smart: A secure multilayer credit-based incentive scheme for delay-tolerant networks. Vehicular Technology, IEEE Transactions on, 58(8), 4628–4639.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Saha, S., Nandi, S., Verma, R. et al. Design of efficient lightweight strategies to combat DoS attack in delay tolerant network routing. Wireless Netw 24, 173–194 (2018). https://doi.org/10.1007/s11276-016-1320-1
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-016-1320-1