Abstract
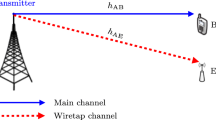
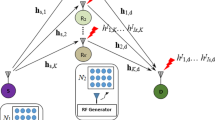
Physical layer security in relay based cooperative networks is a promising approach to maintain confidentiality of information. In this paper, secrecy performance of a dual hop network, with multiple energy harvesting decode and forward (DF) relays, has been analyzed where an eavesdropper also receives the information from the transmission of a selected relay. A selected DF relay harvests energy based on power splitting (PS) scheme in the first time slot. In the second time slot, the selected DF relay transmits the information as well as jamming signals, only when it has harvested sufficient power as decided by a threshold, based on the outage constraint of the network. The secrecy outage probability (SOP) under some assumed conditions, termed as a conditional SOP (CSOP), has been evaluated in closed form. Performance regarding the CSOP increases with increase in transmits power of the source, threshold outage rate, number of relay and energy conversion efficiency, whereas it decreases with an increase in threshold secrecy rate. We indicate the optimal value of PS factor for harvesting energy and the optimal value of a fraction of harvested energy devoted to information signal transmission at which the CSOP is minimum. The SOP without any condition has also been evaluated with and without jamming. The results shows that the CSOP yields better results than the SOP. It is observed that the CSOP with jamming is better than the SOP with jamming by 49.12% for 1 bits/s/Hz threshold secrecy rate and by 81.94% for a threshold secrecy rate of 0.5 bits/s/Hz, respectively at 10 dBW of the source transmits power. A MATLAB based simulation is used to verify our analytical works of the CSOP and the SOP with jamming.










Similar content being viewed by others
References
Wyner, A. D. (1975). The wire-tap channel. Bell System Technical Journal, 54(8), 1355–1387.
Leung-Yan-Cheong, S. K., & Hellman, M. E. (1978). The Gaussian wire-tap channel. IEEE Transactions on Information Theory, 24(4), 451–456.
Bloch, M., Member, S., Barros, J., Rodrigues, M. R. D., & Mclaughlin, S. W. (2008). Wireless information-theoretic. Security, 54(6), 2515–2534.
Zhou, X., McKay, M. R., Maham, B., & Hjorungnes, A. (2011). Rethinking the secrecy outage formulation: A secure transmission design perspective. IEEE Communications Letters, 15(3), 302–304.
Sudevalayam, S., & Kulkarni, P. (2011). Energy harvesting sensor nodes: Survey and implications. IEEE Communications Surveys and Tutorials, 13(3), 443–461.
Gong, J., Chen, X., Xia, M., Member, J. G., Member, X. C., & Member, M. X. (2018). Transmission optimization for hybrid half/full-duplex relay with energy harvesting. IEEE Transactions on Wireless Communications, 17(5), 3046–3058.
Lu, X., Wang, P., Niyato, D., Kim, D. I., Han, Z., & Engineering, C. (2015). Wireless networks with RF energy harvesting: A contemporary survey. IEEE Communications Surveys and Tutorials, 17(2), 757–789.
Ku, M., Li, W., Chen, Y., Member, S., & Liu, K. J. R. (2016). Advances in energy harvesting communication: Past, present, and future challenges. IEEE Communications Surveys and Tutorials, 18(2), 1384–1412.
Luo, Y., Zhang, J., & Letaief, K. B. (2013). Optimal scheduling and power allocation for two-hop energy harvesting communication systems. IEEE Transactions on Wireless Communications, 12(9), 4729–4741.
Zhang, R., & Ho, C. K. (2013). MIMO broadcasting for simultaneous wireless information and power transfer. IEEE Transactions on Wireless Communications, 12(5), 1989–2001.
Son, P. N., & Kong, H. Y. (2015). Cooperative communication with energy-harvesting relays under physical layer security. IET Communications, 9(17), 2131–2139.
Kalamkar, S. S., & Banerjee, A. (2017). Secure communication via a wireless energy harvesting untrusted relay. IEEE Transactions on Vehicular Technology, 66(3), 2199–2213.
Gupta, V., Kalamkar, S. S., & Banerjee, A. (2017). On secure communication using RF energy harvesting two-way untrusted relay. arXiv:1708.07989v1.
Dong, L., Yousefi, H., & Jafarkhani, H. (2011). Cooperative jamming and Power allocation for wireless relay network in presence of eavesdropper. In 2011 IEEE international conference on communications (ICC), Kyoto, 1–5.
Sun, L., Zhang, T., Li, Y., & Niu, H. (2012). Performance study of two-hop amplify-and-forward systems with untrustworthy relay nodes. IEEE Transactions on Vehicular Technology, 61(8), 3801–3807.
Liu, Y., Li, J., & Petropulu, A. P. (2013). Destination assisted cooperative jamming for wireless physical-layer security. IEEE Transactions on Information Forensics and Security, 8(4), 682–694.
Cao, K., Cai, Y., Wu, Y., & Yang, W. (2017). Cooperative jamming for secure communication with finite alphabet inputs. IEEE Communications Letters, 21(9), 2025–2028.
Zhang, G., Xu, J., Wu, Q., Cui, M., Li, X., & Lin, F. (2018). Wireless powered cooperative jamming for secure OFDM system. IEEE Transactions on Vehicular Technology, 67(2), 1331–1346.
Mamaghani, M. T., Kuhestani, A., & Wong, K.-K. (2018). Energy harvesting based secure two-way communication using an untrusted relay, 1–14. arXiv:1708.06437v2 [cs. CR].
Salem, A., Hamdi, K. A., & Rabie, K. M. (2016). Physical layer security with RF energy harvesting in AF multi-antenna relaying networks. IEEE Transactions on Communications, 64(7), 3025–3038.
Raghuwanshi, S., & Maji, P. (2016). Secrecy performance of a dual hop cognitive relay network with an energy harvesting relay. In 2016 International conference on advances in computing, communications and informatics (ICACCI), Jaipur, India (pp. 1622–1627).
Hoang, T. M., Duong, T. Q., Vo, N. S., & Kundu, C. (2017). Physical layer security in cooperative energy harvesting networks with a friendly jammer. IEEE Wireless Communications Letters, 6(2), 174–177.
Ouyang, N., Jiang, X., & Bai, E. (2017). Destination assisted jamming and beamforming for improving the security of AF relay systems. IEEE Access, 5, 4125–4131.
Vo, V. N., Nguyen, T. G., So-In, C., Baig, Z. A., & Sanguanpong, S. (2018). Secrecy outage performance analysis for energy harvesting sensor networks with a jammer using relay selection strategy. IEEE Access, 6, 23406–23419.
Zhang, J., Pan, G., & Xie, Y. (2018). Secrecy analysis of wireless-powered multi-antenna relaying system with nonlinear energy harvesters and imperfect CSI. IEEE Transactions on Green Communications and Networking, 2(2), 460–470.
Zhao, L., & Zheng, K. (2016). Cooperative energy broadcasting system with massive MIMO. IEEE Communications Letters, 20(6), 1247–1250.
Chen, L., Yu, F. R., Ji, H., Rong, B., Li, X., & Leung, V. C. M. (2016). Green full-duplex self-backhaul and energy harvesting small cell networks with massive MIMO. IEEE Journal on Selected Areas in Communications, 34(12), 3709–3724.
Amjad, M., Akhtar, F., Rehmani, M. H., Reisslein, M., & Umer, T. (2017). Full-duplex communication in cognitive radio networks: A survey. IEEE Communications Surveys and Tutorials, 19(4), 2158–2191.
Zheng, B., Wen, M., Wang, C. X., et al. (2018). Secure NOMA based two-way relay networks using artificial noise and full duplex. IEEE Journal on Selected Areas in Communications, XX(XX), 1–14.
Tran, H., Zepernick, H. J., & Phan, H. (2013). Cognitive proactive and reactive df relaying schemes under joint outage and peak transmit power constraints. IEEE Communications Letters, 17(8), 1548–1551.
Gradshteyn, I. S., & Ryzhik, I. M. (2007). Table of integrals, series, and products (7th ed.). New York: Academic Press.
Ho-Van, K., & Do-Dac, T. (2018). Performance analysis of jamming technique in energy harvesting cognitive radio networks. Telecommunication Systems. https://doi.org/10.1007/s11235-018-0477-6.
Acknowledgements
This research is supported by the Department of Electronics and Information Technology, Ministry of Communications and IT, Government of India under the Visvesvaraya Ph.D. Scheme administered by Media Lab Asia with Grant Number PhD-MLA/4(29)/2015–16.
Author information
Authors and Affiliations
Corresponding author
Appendix
Appendix
The \(I^{'}\) from Eq. (24) is given as:
For simplicity in expressing the expression, we assume the some constant as: \(A_1=2^{2R_{TH}^{SEC}} \left( 1+\gamma _{\mathcal {E}_i}\right) -1\), \(A_2=\varOmega _{\mathcal {RD}}\), \(A_3=\frac{{\left( {1 - \beta } \right) }}{{\alpha \eta \beta }}\) and \(A_4=\frac{{A_1{N_0}}}{{\alpha \eta \beta {P_{\mathcal{S}}}{\varOmega _{{\mathcal{S}}{\mathcal{R}}}}}}\). The Eq. (31) can be re-expressed under assumed constant as:
Split the Eq. (32) in two parts to make suitable for the solution and expressed as:
With the help of [31], eq. 3.324.1], the \(I_1^{'}\) can be expressed as:
where \(K_1 (.)\) is the modified Bessel function of first order second kind.
Now, \(I_2^{'}\) from the Eq. (33) can be expressed as:
The \(I_2^{'}\) can be re-expressed with the help of [32], eq. 46] as:
where Ei(.) is the exponential integral function, \(\sum \limits _{Initial\,Value}^{{Final\,Value}} (.)\) indicates the sum of the series. With the help of [31], eq. 3.351.4], we can express the \(I_2^{''}\) in closed form as:
As per Eq. (33), \(I^{'}\) can be expressed in closed form with the help of equation from (34) to (37) as:
This is the closed form expression of \(I^{'}\) which is used in Eq. (25).
Rights and permissions
About this article
Cite this article
Sharma, S., Dhar Roy, S. & Kundu, S. Secure communication with energy harvesting multiple half-duplex DF relays assisted with jamming. Wireless Netw 26, 1151–1164 (2020). https://doi.org/10.1007/s11276-018-1859-0
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-018-1859-0