Abstract
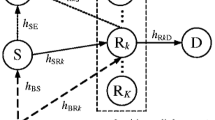
In this paper, an unlicensed relay is deployed to maintain wireless connection between an unlicensed source and an unlicensed destination in spectrum sharing paradigm when source-destination direct channel is unavailable. The relay is capable of energy scavenging (ES) from source signal and uses the scavenged energy to amplify-and-forward it to the destination. The relay’s information transmission is eavesdropped by a wire-tapper. For prompt system performance evaluation, the current paper suggests two closed-form formulas of eavesdropping outage probability at the wire-tapper and decoding outage probability at the destination under interference power limitation and peak transmit power limitation, from which eavesdropping-decoding compromise in the spectrum sharing paradigm with the ES-capable relay is recognized. Numerous results validate the analysis and expose that relay location, times of signal relaying and energy scavenging, received power distribution for signal processing and energy scavenging can be optimized to achieve the best eavesdropping-decoding compromise.






Similar content being viewed by others
Notes
It is recalled that the DOP and the EOP are correspondingly probabilities which channel capacities of the destination and the wire-tapper are less than a target capacity. According to information theory, they are respectively probabilities which the destination and the wire-tapper fail to restore the legitimate information. Consequently, they are pivotal metrics for measuring reliability and security. The smaller the DOP, the more accurate the information decoding at the destination. Meantime, the smaller the EOP, the more eavesdropped the source’s communication. Therefore, the correlation between the DOP and the EOP, which can be quantitatively measured as their ratio (or difference), is a good exposure for an eavesdropping-decoding compromise. In other words, this correlation is physically equivalent to the correlation between the signal and the noise in information transmission and hence, it implicitly reflects information securing capability.
A widely accepted assumption in previous researches on the spectrum sharing paradigm (e.g., [2, 23, 24] and references therein), is that interferences from licensed transmitters to unlicensed receivers are neglected. This assumption comes from the reasonings that licensed transmitters are distant from unlicensed receivers or such interferences are Gaussian-distributed. The current paper borrows this assumption and thus, no interferences from licensed transmitters to unlicensed receivers are considered.
A zero-mean \(\zeta \)-variance circular symmetric complex Gaussian random variable \(\varrho \) is mathematically denoted as \(\varrho \sim \mathcal {CN}(0,\zeta )\).
Simulated results are generated by the Monte-Carlo simulation/method which is well-known in research community on performance analysis, e.g., [30]. Due to the popularity of the Monte-Carlo simulation, a description of how it is conducted should be ignored for compactness and consistency. To obtain simulated results, \(10^7\) channel realizations have been used.
References
Zhou, F., Li, Z., Cheng, J., Li, Q., & Si, J. (2017). Robust AN-aided beamforming and power splitting design for secure MISO cognitive radio with SWIPT. IEEE Transactions on Communications, 16(4), 2450–2464.
Ho-Van, K. (2017). On the outage performance of reactive relay selection in cooperative cognitive networks over Nakagami-\(m\) fading channels. Wireless Personal Communications, 96(1), 1007–1027.
Ho-Van, K. (2017). On the performance of maximum ratio combining in cooperative cognitive networks with proactive relay selection under channel information errors. Telecommunication Systems, 65(3), 365–376.
Cao, Y., Zhao, N., Yu, F. R., Jin, M., Chen, Y., Tang, J., et al. (2018). Optimization or alignment: Secure primary transmission assisted by secondary networks. IEEE JSAC, 36(4), 905–917.
Zhao, N., Yu, F. R., Sun, H., & Li, M. (2016). Adaptive power allocation schemes for spectrum sharing in interference-alignment-based cognitive radio networks. IEEE Transactions on Vehicular Technology, 65(5), 3700–3714.
Zlatanov, N., Schober, R., & Hadzi-Velkov, Z. (2017). Asymptotically optimal power allocation for energy harvesting communication networks. IEEE Transactions on Vehicular Technology, 66(8), 7286–7301.
Nguyen, B. V., Jung, H., Har, D., & Kim, K. (2018). Performance analysis of a cognitive radio network with an energy harvesting secondary transmitter under Nakagami-\(m\) fading. IEEE Access, 6, 4135–4144.
Zhao, N., Cao, Y., Yu, F. R., Chen, Y., Jin, M., & Leung, V. C. M. (2018). Artificial noise assisted secure interference networks with wireless power transfer. IEEE Transactions on Vehicular Technology, 67(2), 1087–1098.
Chen, X., Guo, L., Li, X., Dong, C., Lin, J., & Mathiopoulos, P. T. (2018). Secrecy rate optimization for cooperative cognitive radio networks aided by a wireless energy harvesting jammer. IEEE Access, 6, 34127–34134.
Xu, M., Jing, T., Fan, X., Wen, Y., & Huo, Y. (2018). Secure transmission solutions in energy harvesting enabled cooperative cognitive radio networks. In Proceedings of IEEE WCNC, 15–18 April 2018, Barcelona, Spain (pp. 1–6).
Su, R., Wang, Y., & Sun, R. (2018). Destination-assisted jamming for physical-layer security in SWIPT cognitive radio systems. In Proceedings of IEEE WCNC, 15–18 April 2018, Barcelona, Spain (pp. 1–6).
Qiao, J., Zhang, H., Zhao, F., & Yuan, D. (2018). Secure transmission and self-energy recycling with partial eavesdropper CSI. IEEE JSAC, 36(7), 1531–1543.
Quang, P. M., Duy, T. T., & Bao, V. N. Q. (2016). Performance evaluation of underlay cognitive radio networks over Nakagami-\(m\) fading channels with energy harvesting. In Proceedings of International Conference on Advanced Technologies for Communications, HaNoi, Vietnam, 10–12 October 2016 (pp. 108–113).
Zhang, J., Pan, G., & Wang, H. M. (2016). On physical-layer security in underlay cognitive radio networks with full-duplex wireless-powered secondary system. IEEE Access, 4, 3887–3893.
Ho-Van, K., & Do-Dac, T. (2018). Performance analysis of jamming technique in energy harvesting cognitive radio networks. Telecommunication Systems. https://doi.org/10.1007/s11235-018-0477-6.
Mou, W., Yang, W., Xu, X., Li, X., & Cai, Y. (2016). Secure transmission in spectrum-sharing cognitive networks with wireless power transfer. In Proceedings of international conference on wireless communications & signal processing, JiangSu, China, 13–15 October 2016 (pp. 1–5).
Lei, H., Xu, M., Zhang, H., Pan, G., Ansari, I. S.,&Qaraqe, K. A. (2016). Secrecy outage performance for underlay MIMO CRNs with energy harvesting and transmit antenna selection. In Proceedings of IEEE global communications conference, Washington DC, USA, 4–8 December, 2016 (pp. 1–6).
Singh, A., Bhatnagar, M. R., & Mallik, R. K. (2016). Secrecy outage of a simultaneous wireless information and power transfer cognitive radio system. IEEE Communications Letters, 5(3), 288–291.
Liu, Y., Wang, L., Zaidi, S. A. R., Elkashlan, M., & Duong, T. Q. (2016). Secure D2D communication in large-scale cognitive cellular networks: A wireless power transfer model. IEEE Transactions on Communications, 64(1), 329–342.
Maji, P., Roy, S. D., & Kundu, S. (2018). Physical layer security in cognitive radio network with energy harvesting relay and jamming in the presence of direct link. IET Communications, 12(11), 1389–1395.
Raghuwanshi, S., Maji, P., Roy, S. D.,&Kundu, S. (2016). Secrecy performance of a dual hop cognitive relay network with an energy harvesting relay. In Proceedings of international conference on advances in computing, communications and informatics, Jaipur, India, 21–24 September, 2016 (pp. 1622–1627).
Benedict, F. P., Maji, P., Roy, S. D., & Kundu, S. (2017). Secrecy analysis of a cognitive radio network with an energy harvesting AF relay. In Proceedings of IEEE WiSPNET, 22–24 March 2017, Chennai, India (pp. 1358–1363).
Zhang, X., Xing, J., Yan, Z., Gao, Y., & Wang, W. (2013). Outage performance study of cognitive relay networks with imperfect channel knowledge. IEEE Communications Letters, 17(1), 27–30.
Seyfi, M., Muhaidat, S., & Liang, J. (2013). Relay selection in cognitive radio networks with interference constraints. IET Communications, 7(10), 922–930.
Zhou, X., Zhang, R., & Ho, C. K. (2013). Wireless information and power transfer: Architecture design and rate-energy trade-off. IEEE Transactions on Communications, 61(11), 4754–4767.
Nasir, A. A., Zhou, X., Durrani, S., & Kennedy, R. A. (2013). Relaying protocols for wireless energy harvesting and information processing. IEEE Transactions on Wireless Communications, 12(7), 3622–3636.
Biglieri, E., Proakis, J., & Shamai, S. (1998). Fading channels: Information-theoretic and communications aspects. IEEE Transactions on Information Theory, 44(6), 2619–2692.
Ho-Van, K. (2016). Exact outage probability analysis of proactive relay selection in cognitive radio networks with MRC receivers. Journal of Communications and Networks, 18(3), 288–298.
Gradshteyn, I. S., & Ryzhik, I. M. (2000). Table of integrals, series and products (6th ed.). San Diego, CA: Academic.
Thomopoulos, N. T. (2013). Essentials of Monte Carlo simulation: Statistical methods for build- ing simulation models. New York, Heidelberg, Dordrecht, London: Springer.
Torabi, M., Ajib, W., & Haccoun, D. (2009). Performance analysis of amplify-and- forward cooperative networks with relay selection over Rayleigh fading channels. In Proceedings of IEEE vehicular technology conference, Barcelona, Spain, 26–29 April 2009 (pp. 1–5).
Acknowledgements
This research is funded by Vietnam National Foundation for Science and Technology Development (NAFOSTED) under grant number 102.04-2017.01.
Author information
Authors and Affiliations
Corresponding author
Appendices
Appendix 1: Proof of Lemma 3
Rewriting \({{{\mathcal {J}}}_3}\left( {a,b,c,g} \right) \) as \(\int \limits _a^\infty {{e^{ - \frac{b}{z}}}\frac{{{e^{ - cz}}}}{{{{\left( {z + g} \right) }^2}}}dz}\) and then applying the series expansion for \({{e^{ - \frac{b}{z}}}}\), one can simplify \({{{\mathcal {J}}}_3}\left( {a,b,c,g} \right) \) as
Applying the partial fraction decomposition to \(\frac{1}{{{z^v}{{\left( {z + g} \right) }^2}}}\), one can simplify (37) as
By denoting \({{\mathcal {G}}}\left( {a,c,g} \right) = \int \limits _a^\infty {\frac{{{e^{ - cz}}}}{{{{\left( {z + g} \right) }^2}}}dz}\) and using the definitions of \({{\mathcal {L}}}\left( {a,c,g} \right) = \int \limits _a^\infty {\frac{{{e^{ - cz}}}}{{z + g}}dz}\) and \({{\mathcal {U}}}\left( {u,p,n} \right) = \int \limits _u^\infty {\frac{{{e^{ - pz}}}}{{{z^{n + 1}}}}dz}\), it is observed that (38) accurately matches (28). As such, in order to finish the proof of Lemma 3, one must prove that \({{\mathcal {G}}}\left( {a,c,g} \right) \) can be represented as (29). Performing the integral by parts and then using the definition of \({{\mathcal {L}}}\left( {a,c,g} \right) = \int \limits _a^\infty {\frac{{{e^{ - cz}}}}{{z + g}}dz}\), it is straightforward to reduce \({{\mathcal {G}}}\left( {a,c,g} \right) \) to
which accurately matches (29), finishing the proof.
Appendix 2: Proof of Theorem 1
Rewrite (23) as
According to [31], the SNR at D, \({\Phi _d} = \frac{{{\gamma _{sr}}{\gamma _{rd}}}}{{{\gamma _{sr}} + {\gamma _{rd}} + 1}}\), in (11), can be tightly approximated as
Using (41), one can tightly approximate the DOP in (40) as
Because \(\gamma _{sr}\) and \({{\tilde{P}}}_r\) contain \({P_s}{\left| {{h_{sr}}} \right| ^2}\), they are correlated. Therefore, the \({{{\overline{\text {DOP}} }}}\) can be computed through two steps: i) Step 1 computes the conditional \({{{\overline{\text {DOP}} }}}\) given \({P_s}{\left| {{h_{sr}}} \right| ^2}\); ii) Step 2 averages the conditional \({{{\overline{\text {DOP}} }}}\) over \({P_s}{\left| {{h_{sr}}} \right| ^2}\). In other words, the \({{{\overline{\text {DOP}} }}}\) must be computed as
Inserting \({{\tilde{P}}_r} = \min \left( {\frac{{{I_m}}}{{{{\left| {{h_{rl}}} \right| }^2}}},{P_r}} \right) \) in (22) into the above, one can rewrite the \({{{\overline{\text {DOP}} }}}\) as
By denoting
one can reduce (44) to
By plugging (46) into (42), it is seen that (42) accurately matches (30). As such, the proof of Theorem 1 is finished if (45) is proved to match (31). Toward this end, one substitutes (3) and (12) into (45):
By denoting \(Y = {P_s}{\left| {{h_{sr}}} \right| ^2}\) and letting M as (35), one simplifies (47) as
The PDF of Y can be derived through its CDF as \({f_Y}\left( y \right) = \frac{{d{F_Y}\left( y \right) }}{{dy}}\). Therefore, the CDF of Y must be derived first. Using the definition of the CDF, one obtains
Plugging (19) and (20) into (49), \({F_Y}\left( y \right) \) is further simplified as
where V, T, and U are defined in (32), (33), and (34), respectively.
Taking the derivative of (50), one obtains the PDF of Y as
Plugging (51) into (48) and after performing the variable change \({z = y + \sigma _r^2}\), (48) is simplified as
By rewriting (52) in terms of \({{{\mathcal {J}}}_1}\left( {a,b,c} \right) = \int \limits _a^\infty {{e^{ - \frac{b}{z} - cz}}dz}\), \({{{\mathcal {J}}}_2}\left( {a,b,c,g} \right) = \int \limits _a^\infty {\frac{{{e^{ - \frac{b}{z} - cz}}}}{{z + g}}dz}\), and \({{{\mathcal {J}}}_3}\left( {a,b,c,g} \right) = \int \limits _a^\infty {\frac{{{e^{ - \frac{b}{z} - cz}}}}{{{{\left( {z + g} \right) }^2}}}dz}\), it is seen that (52) accurately matches (31), finishing the proof.
Rights and permissions
About this article
Cite this article
Ho-Van, K., Do-Dac, T. Eavesdropping-decoding compromise in spectrum sharing paradigm with ES-capable AF relay. Wireless Netw 26, 1937–1948 (2020). https://doi.org/10.1007/s11276-018-1878-x
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-018-1878-x