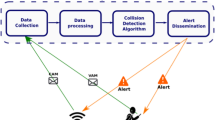
Abstract
Vehicular ad hoc networks (VANETs) have been a research focus in recent years. VANET’s main applications are enhancing road safety and reducing traffic accidents. Moreover, the VANET system can also reduce the time it takes for emergency vehicles to arrive at the accident location. The security of the transmission messages is of utmost importance, and to protect the transmission messages we propose a secure ambulance communication protocol for VANET to ensure that messages will not be revealed or stolen. The proposed scheme combines symmetric encryption, message authentication codes and digital signature mechanisms, and thereby achieves non-repudiation, availability, integrity, confidentiality, mutual authentication, session key security, known-key security and the ability to prevent known attacks. Finally, with NS2 simulation results that are based on realistic vehicle density statistics and the Taipei city road map, we argue that our secure ambulance communication protocol is effective in real VANET scenarios.












Similar content being viewed by others
References
Armknecht, F., Festag, A., Westhoff, D., & Zeng, K. (2007, March). Cross-layer privacy enhancement and non-repudiation in vehicular communication. In 4th Workshop on mobile ad-hoc networks (WMAN) 2007, Bern, Switzerland
Bouassida, M.-S., Chrisment, I., & Festor, O. (2008). Group key management in MANETs. International Journal of Network Security, 6(1), 67–69.
Browse nsnam Files on SourceForge.net, http://sourceforge.net/projects/nsnam/files/, access available on 3 April 2013.
Choi, J., & Jung, S. (2009). A security framework with strong non-repudiation and privacy in VANETs. In 6th IEEE consumer communications and networking conference (pp. 835–839), 10–13 Jan. 2009.
Das, K. (2008). An identity-based random key pre-distribution scheme for direct key establishment to prevent attacks in wireless sensor networks. International Journal of Network Security, 6(2), 134–144.
Duri, S., Gruteser, M., Liu, X., Moskowitz, P., Perez, R., Singh, M., & Tang, J.-M. Framework for security and privacy in automotive telematics. In Proceedings of the 2nd international workshop on mobile commerce (pp. 25–32).
Electronic Toll Collection, http://www.gsa.gov/portal/content/104326, access available on 3 April 2013.
ElZarki, M., Mehrotra, S., Tsudik, G., & Venkatasubramanian, N. (2002). Security issues in a future vehicular network. In European Wireless’02 conference.
Harney, H., & Muckenhirn, C. (1997). Group key management protocol (GKMP). (RFC 2094).
IEEE dedicated short range communication standard (DSRC), http://grouper.ieee.org/groups, access available on 3 April 2013.
Jiang, D., Birmingham, A. L., & Delgrossi, L. (2008). IEEE 802.11p: towards an international standard for wireless access in vehicular environments. In Proceedings of IEEE vehicular technology conference (pp. 2036–2040).
Jiang, N., & Wang, J. (2008). Anonymous authentication protocol for multi-services in wireless environments. The Journal of China Universities of Posts and Telecommunications, 15(4), 69–74.
Johnson, D.-B., Hu, Y., Maltz, D.-A. (2007). The dynamic source routing protocol (DSR) for mobile ad hoc networks for IPv4. IETF RFC 4728.
Jungels, D., Raya, M., Papadimitratos, P., Aad, I., & Hubaux, J.-P. Certificate revocation in vehicular ad hoc networks. Technical LCAReport-2006-006.
Karp, B., & Kung, H. (2000). GPSR: greedy perimeter stateless routing for wireless networks. In Proceedings of the 6th ACM annual international conference on Mobile computing and networking (MobiCom), Boston, Massachusetts, United States (pp. 243–254).
Ke Liu’s NS2 Code and Q &A, http://www.cs.binghamton.edu/~kliu/research/ns2code/index.html#gpsr, access available on 3 April 2013.
Kenney, J. B. (2011). Dedicated short-range communications (DSRC) standards in the United States. Proceedings of the IEEE, 99(7), 1162–1182.
Lee, J.-S., & Chang, C.-C. (2007). Secure communications for cluster-based ad hoc networks using node identities. Journal of Network and Computer Applications, 30(4), 1377–1396.
Li, C.-T., Hwang, M.-S., & Chu, Y.-P. (2008). A secure and efficient communication scheme with authenticated key establishment and privacy preserving for vehicular ad hoc networks. Computer Communications, 31(12), 2803–2814.
Li, W., Wen, Q., Su, Q., & Jin, Z. (2012). An efficient and secure mobile payment protocol for restricted connectivity scenarios in vehicular ad hoc network. Computer Communication, 35(2), 188–195.
Mershad, K., & Artail, H. (2013). A framework for secure and efficient data acquisition in vehicular ad hoc networks. IEEE Transactions on Vehicular Technology, 62(2), 536–551.
Perkins, C., & Royer, E. (1999). Ad-hoc on-demand distance vector routing. In Proceedings of the second IEEE workshop on mobile computing sytems and applications (pp. 90–100).
Perrig, A., Canetti, R., Tygar, J.-D., & Song, D. (2002). The TESLA broadcast authentication protocol. UC Berkeley and IBM Research, 5(2), 2–13.
Plößl, K., & Federrath, H. (2008). A privacy aware and efficient security infrastructure for vehicular ad hoc networks. Computer Standards & Interfaces, 30(6), 390–397.
Raghunathan, S., Mikler, A.-R., & Cozzolino, C. (2005). Secure agent computation: X.509 Proxy Certificates in a multi-lingual agent framework. Journal of Systems and Software, 75(1–2), 123–137.
Raya, M., & Hubaux, J.-P. (2005). Security aspects of inter-vehicle communications. In Proceedings of the 5th Swiss transport research conference, Monte Verità / Ascona (pp. 1–14), 9–11 March, 2005.
Raya, M., & Hubaux, J.-P. (2005). The security of vehicular ad hoc networks. In Proceedings of SASN’05 (pp. 11–21).
Schmitz, A., Wenig, M. (2006). The effect of the radio wave propagation model in mobile ad hoc networks. In The 9th ACM international symposium on modeling analysis and simulation of wireless and mobile systems, Spain (pp. 61–67).
Schneier, B. (1996). Applied cryptography protocols algorithms and source code in C (2nd ed.). New York: Wiley.
Stallings, W. (2005). Cryptography and network security (4th ed.). Englewood Cliffs: Prentice-Hall.
The American Society for Testing and Materials (ASTM), http://www.astm.org/, access available on 3 April 2013.
Traffic flow statistics, traffic engineering office Taipei City government, http://www.bote.taipei.gov.tw/ct.asp?xItem=660485&CtNode=20205&mp=117031, access available on 3 April 2013.
Wasef, A., & Shen, X. (2013). EMAP: expedite message authentication protocol for vehicular ad hoc networks. IEEE Transactions on Mobile Computing, 12(1), 78–89.
Yang, X., Liu, J., Zhao, F., & Vaidya, N. (2004). A vehicle-to-vehicle communication protocol for cooperative collision warning. In Annual international conference on mobile and ubiquitous systems: networking and services (MobiQuitous) (pp. 114–123).
Zhang, L., Wu, Q., Solanas, A., & Domingo-Ferrer, J. (2010). A scalable robust authentication protocol for secure vehicular communications. IEEE Transactions on Vehicular Technology, 59(4), 1606–1617.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Chen, CL., Chang, IC., Chang, CH. et al. A Secure Ambulance Communication Protocol for VANET. Wireless Pers Commun 73, 1187–1213 (2013). https://doi.org/10.1007/s11277-013-1273-y
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-013-1273-y