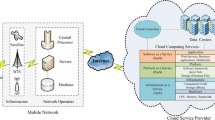
Abstract
Vehicular ad hoc network (VANET) is expected to improve our driving experience through enhanced safety, security, robustness, and infotainment. Nevertheless, despite considerable amount of research, VANET did not make it, at least not on a full scale, to the deployment stage because of many issues including security and privacy. However it is speculated that in the future high-end vehicles, on-board computation, communication, and storage resources will be under-utilized. Therefore, recently a new paradigm shift from conventional VANET to vehicular cloud computing was envisioned. This paradigm shift was realized through merging VANET with revolutionary cloud computing. Clearly cloud computing is one of today’s tempting technology areas due, at least partially, to its virtualization and cost-effectiveness. However, to date the potential architectural framework for VANET-based cloud computing has not been defined so far. To fill this gap, in this paper, first we put forth the taxonomy of VANET based cloud computing and then define a communication paradigm stack for VANET clouds. Additionally we divide VANET clouds into three architectural frameworks namely vehicular clouds (VC), vehicles using clouds (VuC), and hybrid vehicular clouds (HVC). Each proposed framework provides particular set of services depending upon the underlying communication paradigm. To understand our proposed framework well, we also propose a novel use-case service of the VANET-based cloud namely traffic information dissemination through clouds. In the proposed scheme, vehicles moving on the road are provided with fine-grained traffic information by the cloud as a result of their cooperation with the cloud infrastructure. Vehicles share their frequent mobility dynamics with the cloud and cloud in turn provides them with long range traffic information based on their current and near-future locations. Our simulation results show that the traffic information dissemination through cloud is feasible and the vehicles receive above 83 % of the traffic information from clouds through gateways in worst-case scenarios (i.e. extensive dense traffic) and above 90 % traffic information in average case scenarios. Finally we also outline the unique security and privacy issues and research challenges in VANET clouds.












Similar content being viewed by others
Notes
This argument is true only for insiders. In order to deal with the outsider attackers, the information must be made secure against different attacks launched by the outsiders such as content manipulation and profilation.
The terms ‘VANET-based clouds’ and ‘vehicular clouds’ are used interchangeably in this paper and both the terms refer to the merging of VANET and cloud computing.
The terms ‘movement vector’ and ‘mobility vector’ are used in this paper interchangeably and both are represented by MV.
References
Hartenstein, H., & Laberteaux, K. P. (2009). VANET: Vehicular applications and inter-networking. Chichester: Wiley. ISBN 978-0-470-74056-9.
Raya, M., & Hubaux, J.-P. (2007). Securing vehicular ad hoc networks. Journal of Computer Security, 15(1), 39–68.
Leinmuller, T., Schoch, E., & Maihofer, C. (2007). Security requirements and solution concepts in vehicular ad hoc networks. In Proceedings of the wireless on demand network systems and services (WONS ‘07), fourth annual conference on (pp. 84–91).
Dötzer, F. (2006). Privacy issues in vehicular ad hoc networks. In G. Danezis & D. Martin (Eds.) Privacy enhancing technologies, Lecture notes in computer science 3856 (pp. 197–209). Berlin: Springer.
Antolino Rivas, D., Barceló-Ordinas, J. M., Guerrero Zapata, M., & Morillo-Pozo, J. D. (2011). Security on VANETs: Privacy, misbehaving nodes, false information and secure data aggregation. Journal of Network and Computer Applications, 34(6), 1942–1955.
Papadimitratos, P., Buttyan, L., Holczer, T., Schoch, E., Freudiger, J., Raya, M., et al. (2008). Secure vehicular communication systems: Design and architecture. IEEE Communications Magazine, 46(11), 100–109.
Kargl, F., Papadimitratos, P., Buttyan, L., Muter, M., Schoch, E., Wiedersheim, B., et al. (2008). Secure vehicular communication systems: Implementation, performance, and research challenges. IEEE Communications Magazine, 46(11), 110–118.
National Transportation Statistics Book (2008). U.S. Department of Transportation, Research and Innovative Technology Administration. http://www.rita.dot.gov/bts/sites/rita.dot.gov.bts/files/publications/national_transportation_statistics/2008/index.html [Online]
Traffic Safety Facts. (2006). [Online], http://www.nhtsa.gov/
Lee, U., Cheung, R., & Gerla, M. (2009). Emerging vehicular applications. In S. Olariu & M. C. Weigle (Eds.) Vehicular networks: From theory to practice (pp. 1–30). BocaRaton, FL: Taylor and Francis.
Xu, Q., Mak, T., Ko, J., & Sengupta, R. (2004). Vehicle-to-vehicle safety messaging in DSRC. In Proceedings of the 1st ACM international workshop on vehicular ad hoc networks, ACM, Philadelphia, PA, USA (pp. 19–28).
Abuelela, M., & Olariu, S. (2010). Taking VANET to the clouds. In Proceedings of the 8th international conference on advances in mobile computing and multimedia (MoMM’10) (pp. 6–13).
Armbrust, M., Fox, A., Griffith, R., Joseph, A. D., Katz, R., Konwinski, A., et al. (2010). A view of cloud computing. Communications of the ACM, 53(4), 50–58.
Olariu, S., Eltoweissy, M., & Younis, M. (2011). Towards autonomous vehicular clouds. ICST Transactions on Mobile Communications and Applications, 11(7–9), 1–11.
Hussain, R., Son, J., Eun, H., Kim, S., & Oh, H. (2012). Rethinking vehicular communications: Merging VANET with cloud computing. In Proceedings of the IEEE 4th international conference on cloud computing technology and science (CloudCom) (pp. 606–609).
Hartenstein, H., & Laberteaux, K. P. (2008). A tutorial survey on vehicular ad hoc networks. Communications Magazine, IEEE, 46(6), 164–171.
Papadimitratos, P., Buttyan, L., Holczer, T., Schoch, E., Freudiger, J., Raya, M., et al. (2008). Secure vehicular communication systems: Design and architecture. Communications Magazine, IEEE, 46(11), 100–109.
Hussain, R., Kim, S., & Oh, H. (2009). Towards privacy aware pseudonymless strategy for avoiding profile generation. In H. Youm & M. Yung (Eds.), VANET. Information security applications, Lecture notes in computer science 5932 (pp. 268–280). Berlin: Springer.
Jinyuan, S., Chi, Z., Yanchao, Z., & Yuguang, F. (2010). An identity-based security system for user privacy in vehicular ad hoc networks. Parallel and Distributed Systems, IEEE Transactions on, 21(9), 1227–1239.
Li, C.-T., Hwang, M.-S., & Chu, Y.-P. (2007). A secure and efficient communication scheme with authenticated key establishment and privacy preserving for vehicular ad hoc networks. Computer Communications, 31(12), 2803–2814.
Wlodarczyk, T. W., & Chunming, R. (2011). An initial survey on integration and application of cloud computing to high performance computing. In Proceedings of the cloud computing technology and science (CloudCom), IEEE third international conference on (pp. 612–617).
Zhou, M., Zhang, R., Xie, W., Qian, W., & Zhou, A. (2010). Security and privacy in cloud computing: A survey. In Proceedings of semantics knowledge and grid (SKG), sixth international conference on (pp. 105–112).
Zeng, K., & Cavoukian, A. (2010). Modeling cloud computing architecture without compromising privacy: A privacy by design approach. Ontario: NEC Company Ltd, and Information and Privacy Commissioner.
Bessani, A., Correia, M., Quaresma, B., Andr, F., & Sousa, P. (2011). DepSky: Dependable and secure storage in a cloud-of-clouds. In Proceedings of the sixth conference on computer systems (EuroSys’11), ACM (pp. 31–46).
Cachin, C., Keidar, I., & Shraer, A. (2009). Trusting the cloud. SIGACT News, 40(2), 81–86.
Bernstein, D., Vidovic, N., & Modi, S. (2010). A cloud PAAS for high scale, function, and velocity mobile applications—With reference application as the fully connected car. In Proceedings of the systems and networks communications (ICSNC), fifth international conference on (pp. 117–123).
Yan, G., Rawat, D. B., & Bista, B. B. (2012). Towards secure vehicular clouds. In Proceedings of the complex, intelligent and software intensive systems (CISIS), sixth international conference on (pp. 370–375).
Yan, G., Wen, D., Olariu, S., & Weigle, M. C. (2013). Security challenges in vehicular cloud computing. Intelligent Transportation Systems, IEEE Transactions on, 14(1), 284–294.
Yu, R., Zhang, Y., Gjessing, S., Xia, W., & Yang, K. (2013). Toward cloud-based vehicular networks with efficient resource management. IEEE Network, 27(5), 48–55.
Whaiduzzaman, M., Sookhak, M., Gani, A., & Buyya, R. (2014). A survey on vehicular cloud computing. Jouranl of Network and Computer Applications, 40, 325–344.
Wolterink, W. K., Heijenk, G., & Karagiannis, G. (2011). Dissemination protocols to support cooperative adaptive cruise control (CACC) merging. In Proceedings of the ITS telecommunications (ITST), 11th international conference on (pp. 15–20).
Watson, J. D., Pellerito, M., Gladden, C., & Huirong, F. Simulation and analysis of extended brake lights for inter-vehicle communication networks. In Proceedings of the distributed computing systems workshops, ICDCSW ‘07, 27th international conference on (p. 87).
Chow, R., Golle, P., Jakobsson, M., Shi, E., Staddon, J., Masuoka, R., & Molina, J. (2009). Controlling data in the cloud: Outsourcing computation without outsourcing control. In Proceedings of the 2009 ACM workshop on cloud computing security, CCSW’09 (pp. 85–90).
Pearson, S., & Benameur, A. (2010). Privacy, security and trust issues arising from cloud computing. In Proceedings of the cloud computing technology and science (CloudCom), IEEE second international conference on (pp. 693–702).
Ngo, C., Membrey, P., Demchenko, Y., & de Laat, C. (2011). Security framework for virtualised infrastructure services provisioned on-demand. In Proceedings of the cloud computing technology and science (CloudCom), IEEE third international conference on (pp. 698–704).
Arif, S., Olariu, S., Wang, J., Yan, G., Yang, W., & Khalil, I. (2012). Datacenter at the airport: Reasoning about time-dependent parking lot occupancy. IEEE Transactions on Parallel and Distributed Systems, 23(11), 2067–2080.
Hussain, R., Abbas, F., Son, J., Kim, S., & Oh, H. (2014). Using public buses as mobile gateways in vehicular clouds. In Proceedings of the IEEE international conference on consumer electronics (ICCE) (pp. 175–176).
Hussain, R., Abbas, F., Son, J., & Oh, H. (2013). TIaaS: Secure cloud-assisted traffic information dissemination in vehicular ad hoc networks. In Proceedings of the 13th IEEE/ACM international symposium on cluster, cloud, and grid computing (CCGrid) (pp. 178–179).
http://articles.sae.org/11340/. Accessed on February 5, 2014.
Hussain, R., Abbas, F., Son, J., Kim, D., Kim, S., & Oh, H. (2013). Vehicle witnesses as a service: Leveraging vehicles as witnesses on the road in VANET clouds. In Proceedings of the cloud computing technology and science, IEEE international conference on, (CloudCom’13) (pp. 439–444).
Qin, Y., Huang, D., & Zhang, X. (2012). VehiCloud: Cloud computing facilitating routing in vehicular networks. In Proceedings of the security and privacy in computing and communications (TrustCom), IEEE 11th international conference on (pp. 1438–1445).
Acknowledgments
This work was supported in part by the MSIP (Ministry of Science, ICT and Future Planning), Korea, under the ITRC (Information Technology Research Center) support program (NIPA-2014-H0301-14-1015) supervised by the NIPA (National IT Industry Promotion Agency). This work was also supported in part by the MSIP (Ministry of Science, ICT and Future Planning), Korea, under the ITRC (Information Technology Research Center) support program (NIPA-2014-H0301-14-1044) supervised by the NIPA(National IT Industry Promotion Agency). This work was also supported in part by the NRF (National Research Foundation of Korea) grant funded by the Korea government MEST (Ministry of Education, Science and Technology) (No. NRF-2012R1A1A2009152). This work was also supported in part by the NRF (National Research Foundation of Korea) grant funded by the Korea government MEST (Ministry of Education, Science and Technology) (No. NRF-2012R1A2A2A01046986).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Hussain, R., Rezaeifar, Z. & Oh, H. A Paradigm Shift from Vehicular Ad Hoc Networks to VANET-Based Clouds. Wireless Pers Commun 83, 1131–1158 (2015). https://doi.org/10.1007/s11277-015-2442-y
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-015-2442-y