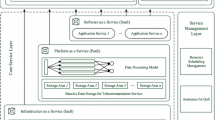
Abstract
Computing environment has changed a lot by development of network and wide spread of the mobile terminal. Among them, adoption of cloud computing causes a large change socially. The social consensus by introduction of smartwork based on this cloud computing environment is increasing. Especially, smartwork which can work freely anytime and anywhere has been noted as a new business model while broadband communication infrastructure becomes popular. However, smartwork based on cloud computing environment has a variety of security vulnerabilities. The risk of information leakage is increasing according to increasing of vulnerability of virtualization technology which cloud computing has, and security threats of mobile terminal used to smartwork. In this paper, we look security element by smartwork design for the activation of the smartwork based on cloud computing and organize to respond to the attack. The corresponding method presented in this paper will be applied to safe security model.




Similar content being viewed by others
References
Diogo, A. B., & Fernandes, L. (2014). Security issues in cloud environments: A survey. International Journal of Information Security, 13(2), 113–170.
Rong, C., Nguyen, S., & Jaatun, M. (2013). Beyond lightning: A survey on security challenges in cloud computing. Computers & Electrical Engineering, 39(1), 47–54.
Li, J., Li, B., Wo, T., Hu, C., Huai, J., Liu, L., & Lam, K. P. (2012). CyberGuarder: A virtualization security assurance architecture for green cloud computing. Future Generation Computer Systems, 28(2), 379–390.
Chen, C.-L., Tsaur, W.-J., Chen, Y.-Y., & Chang, Y.-C. (2014). A secure mobile DRM system based on cloud architecture. Computer Science and Information Systems, 11(3), 925–941.
Guha, V., & Shrivastava, M. (2013). Review of information authentication in mobile cloud over SaaS & PaaS layers. International Journal of Advanced Computer Research (IJACR), 3(1), 9.
Peng, K. (2013). A secure network for mobile wireless service. Journal of Information Processing Systems, 9(2), 247–258.
Lee, T., Kim, H., Rhee, K.-H., & Uk, S. (2013). Design and implementation of E-discovery as a service based on cloud computing. Computer Science and Information Systems, 10(2), 703–724.
Joo, S. G., Son, Y. G., & Jeon, S. G. (2012). Policy implications for the smart work diffusion: Focusing on the perceptual differences on organizational effectiveness between smart workers and office workers. Journal of Digital Policy & Management, 10, 11–22.
Kim, Y., & Chang, H. (2013). A study on small and medium enterprise information foundation for wireless sensor networks work environment implementation. Sensor Letters, 11(9), 1799–1803.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Yang, HS., Yoo, SJ. A Study on Smartwork Security Technology Based on Cloud Computing Environment. Wireless Pers Commun 94, 445–454 (2017). https://doi.org/10.1007/s11277-015-3091-x
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-015-3091-x