Abstract
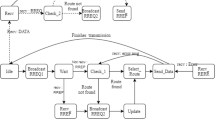
Constructing an efficient and secured Wireless Mesh Network is a challenging issue due to its physical channel vulnerability and dynamic change of topology. In this network, attacks on network layer have vital significance since they may lead to disabling of larger scale network services. Secured Routing Protocol plays a major role in providing seamless network services. A Modified DSR protocol is proposed in this paper to overcome the blackhole attacks by detecting malicious nodes in the network. The proposed work computes the trust level of the path in the network layer by calculating the capability of the links. The link forwarding capability of the links is calculated at the link layer and node forwarding capability is calculated at network layer based on the behavior of the nodes. The nodes operate in the promiscuous mode to detect the misbehaving nodes. The performance of the modified DSR protocol is compared with DSR protocol and the simulation results show that the throughput and packet delivery ratio for the proposed work is better than DSR even in the presence of malicious nodes with minimal network overhead.











Similar content being viewed by others
References
Akyildiz, I. F., Wang, X., & Wang, W. (2005). Wireless mesh network: A survey. Computer Networks and ISDN Systems, 47(4), 445–487.
Campista, M. E. M., & Passos, D. G. (2008). Routing metrics and protocols for wireless mesh networks. IEEE Network Magazine, 22, 6–12.
Ad hoc on-demand distance vector (AODV) routing. www.ietf.org/rfc/rfc3561.txt.
Draves, R., Padhye, J., & Zill, B. (2004). The architecture of the link quality source routing protocol, technical report MSR-TR-2004-57, Microsoft Research.
Draves, R., Padhye, J., & Zill, B. (2004). Routing in multi-radio, multi-hop wireless mesh networks. In ACM international conference on mobile computing and networking (MobiCom) (p. 114128).
Optimized Link State Routing Protocol (RFC 3626)-IETF. www.ietf.org/rfc/rfc3626.txt.
Perkins, C. E., & Bhagwa, P. (1994). Highly dynamic destination-sequenced distance-vector routing (DSDV) for mobile computers. In SIGCOMM ’94 proceedings of the conference on communications architectures, protocols and applications (pp. 234–244).
The dynamic source routing protocol (DSR) for mobile ad hoc networks for IPv4. www.ietf.org/rfc/rfc4728.txt.
Akyildiz, I. F., & Xudong, W. (2008). Cross-layer design in wireless mesh networks. IEEE Transactions on Vehicular Technology, 57(2), 1061–1076.
Chien, C., Srivastava, M., Jain, R., Lettieri, P., Aggarwal, V., & Sternowski, R. (1999). Adaptive radio for multimedia wireless links. IEEE Journal on Selected Areas in Communications, 17(5), 793–813.
Ebert, J., & Wolisz, A. (2001). Combined tuning of RF power and medium access control for WLANs. Mobile Networks and Applications, 6(5), 417–426.
Lettieri, P., & Srivastava, M. (1998). Adaptive frame length control for improving wireless link throughput, range, and energy efficiency. In IEEE INFOCOM (Vol. 2, pp. 564–571).
Sen, J. (2013). Wireless networks and security—Issues, challenges and research trends. Berlin: Springer.
Hu, Y. C., Johnson, D. B. & Perrig, A. (2002). SEAD: Secure efficient distance vector routing for mobile wireless ad hoc networks. In Proceedings of the 4th IEEE workshop on mobile computing systems and applications (WMCSA02) (p. 313). Callicoon, NY.
Zapata, M. G., & Asokan, N. (2002). Securing ad hoc routing protocols. Proceedings of the 1st ACM workshop on wireless security (WiSe02) (pp. 1–10). Atlanta. GA.
Hu, Y. C., Perrig, A., & Johnson, D. (2002). Ariadne: A secure on-demand routing protocol for adhoc networks. In Proceedings of ACM annual international conference on mobile computing (MobiCom02) (pp. 21–38). Atlanta, GA.
Sanzgiri, K., Dahill, B., Levine, B. N., Shields, C., & Belding-Royer, E. M. (2002). A secure routing protocol for ad hoc networks. In Proceedings of the 10th IEEE international conference on network protocols (ICNP02) (pp. 78–87) Paris.
Papadimitratos, P., & Haas, Z. J. (2002). Secure routing for mobile ad hoc networks. In Proceedings of the SCS communication networks and distributed systems modeling and simulation conference (CNDS02) (pp. 27–31). San Antonio, TX.
Papadimitratos, P., & Hass, Z. J. (2003). Secure link state routing for mobile ad hoc networks. In Proceedings of the symposium on applications and the internet workshops (SAINT03) (pp. 379–383). Washington, DC.
Li, C., Wang, Z., & Yang, C. (2011). Secure routing for wireless mesh networks. International Journal of Network Security, 13(2), 109–120.
Just, M., Kranakis, E., & Wan, T. (2003). Resisting malicious packet dropping in wireless ad hoc networks, second international conference proceedings (pp. 8–10) Montreal.
Perlman, R. (1998). Network layer protocols with byzantine robustness. Ph.D. thesis, Massachusetts Institute of Technology.
Deng, H., Li, W., & Agrawal, D. P. (2002). Routing security in wireless ad hoc networks. IEEE Communications Magazine, 40(10), 70–75.
Singh, P. K., & Sharma, G. (2012). An efficient prevention of black hole problem in AODV routing protocol in MANET. In IEEE 11th international conference on trust, security and privacy in computing and communications.
Thachil, F., & Shet. K. C. (2012). A trust based approach for AODV protocol to mitigate black hole attack in MANET. In International conference on computing sciences, Phagwara.
Saetang, W., & Charoenpanyasak, S. (2012). CAODV free black hole attack in ad hoc networks. In International conference on computer networks and communication system, IPCSIT. Singapore: IACSIT Press.
Patcha, A., & Mishra, A. (2003). Collaborative security architecture for black hole attack prevention in mobile ad hoc networks. In Radio and wireless conference (pp. 75–78).
Xiaopeng, G., & Wei, C. (2007). A novel gray hole attack detection scheme for mobile ad-hoc networks. In IFIP international conference on network and parallel computing workshops (pp. 209–214).
Cai, J., Yi, P., Chen, J., Wang, Z., & Liu, N. (2010). An adaptive approach to detecting black and gray hole attacks in ad hoc network. In 24th IEEE international conference on advanced information networking and applications, Perth, Australia.
Misra, R., & Mandal, C. R. (2005). Performance comparison of AODV/DSR on-demand routing protocols for ad hoc networks in constrained situation. In IEEE international conference on personal wireless communications (ICPWC) (pp. 86–89). doi:10.1109/ICPWC.2005.1431307.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Thillaikarasi, R., Bhanu, S.M.S. An Efficient DSR Protocol to Detect Blackhole Attacks in WMN Using Cross Layer Approach. Wireless Pers Commun 95, 3477–3492 (2017). https://doi.org/10.1007/s11277-017-4008-7
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-017-4008-7