Abstract
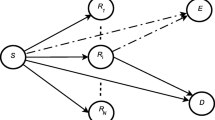
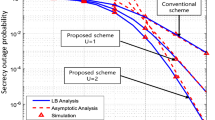
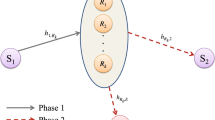
In this paper, a dual-hop amplify-and-forward relay system is considered with an eavesdropper where each link undergoes independent, non-identical, flat Rayleigh fading. The eavesdropper is capable of diversity combining the direct and relayed communication from the source using maximal ratio combining (MRC) and selection combining (SC). Closed-form upper and lower bounds on secrecy outage probability are derived. Closed-form approximate secrecy outage probability and ergodic secrecy rate is also obtained when source–relay link average signal-to-noise ratio (SNR) is high. Asymptotic analysis is presented when dual-hop links have equal or unequal average SNR. It is found that SC has both the secrecy outage and ergodic secrecy rate performances are better than MRC. To achieve the same secrecy outage performance of SC, MRC requires relatively higher SNR at lower rate. MRC also requires relatively higher SNR to achieve same secrecy rate performance of SC when eavesdropper link quality degrades. It is observed that lower bound for secrecy outage is tight and tends towards secrecy outage as SNR increases. It is interesting to find that either one of the dual-hop link can limit the performances even if the other link average SNR is infinitely high.






Similar content being viewed by others
References
Wyner, A. D. (1975). The wire-tap channel. Bell System Technical Journal, 54(8), 1355–1387. doi:10.1002/j.1538-7305.1975.tb02040.x.
Gopala, P. K., Lai, L., & Gamal, H. E. (2008). On the secrecy capacity of fading channels. IEEE Transactions of Information Theory, 54(10), 4687–4698.
Liang, Y., Poor, H., et al. (2009). Information theoretic security. Foundations and Trends in Communications and Information Theory, 5(4–5), 355–580.
Bloch, M., Barros, J., Rodrigues, M. R. D., & McLaughlin, S. (2008). Wireless information-theoretic security. IEEE Transactions of Information Theory, 54(6), 2515–2534.
Barros, J., Rodrigues, M. R. D. (2006). Secrecy Capacity of Wireless Channels. InProceedings of the IEEE international symposium on information theory (ISIT) (pp. 356–360).
Csiszar, I., & Korner, J. (1978). Broadcast channels with confidential messages. IEEE Transactions of Information Theory, 24(3), 339–348.
Luo, S., Li, J., & Petropulu, A. P. (2013). Uncoordinated cooperative jamming for secret communications. IEEE Transactions on Information Forensics and Security, 8(7), 1081–1090.
Gerbracht, S., Scheunert, C., & Jorswieck, E. (2012). Secrecy outage in MISO systems with partial channel information. IEEE Transactions on Information Forensics and Security, 7(2), 704–716.
Lai, L., & Gamal, H. E. (2008). The Relay–Eavesdropper channel: Cooperation for secrecy. IEEE Transactions of Information Theory, 54(9), 4005–4019.
Dong, L., Han, Z., Petropulu, A., & Poor, H. (2010). Improving wireless physical layer security via cooperating relays. IEEE Transactionns of Signal Processing, 58(3), 1875–1888.
Li, J., Petropulu, A., & Weber, S. (2011). On cooperative relaying schemes for wireless physical layer security. IEEE Transactionns of Signal Processing, 59(10), 4985–4997.
Krikidis, I. (2010). Opportunistic relay selection for cooperative networks with secrecy constraints. IET Communications, 4(15), 1787–1791.
Krikidis, I., Thompson, J., & McLaughlin, S. (2009). Relay selection for secure cooperative networks with jamming. IEEE Transactions of Wireless Communications, 8(10), 5003–5011.
Zou, Y., Wang, X., & Shen, W. (2013). Optimal relay selection for physical-layer security in cooperative wireless networks. IEEE Journal on Selected Areas in Communications, 31(10), 2099–2111.
Bao, V. N. Q., & Trung, N. L. (2012). Multihop decode-and-forward relay networks: Secrecy analysis and relay position optimization. REV Journal on Electronics and Communications, 2(1–2), 33–41.
Jindal, A., Kundu, C., & Bose, R. (2014). Secrecy outage of dual-hop amplify-and-forward system and its application to relay selection. InProceedings of the IEEE 79th vehicular technology conference (VTC Spring).
Jindal, A., Kundu, C., & Bose, R. (2014). Secrecy outage of dual-hop af relay system with relay selection without eavesdropper’s CSI. IEEE Communications Letters, 18(10), 1759–1762.
Hwang, K.-S., & Ju, M. (2014). Secrecy outage probability of amplify-and-forward transmission with multi-antenna relay in presence of eavesdropper. In Proceedings of the IEEE international conference on communications (ICC) (pp. 5408–5412).
Gabry, F., Salimi, S., Thobaben, R., & Skoglund, M. (2013). High SNR performance of amplify-and-forward relaying in Rayleigh fading wiretap channels. InProceedings of the Iran workshop on communication and information theory (IWCIT) (pp. 1–5).
Zou, Y., Zhu, J., Zheng, B., & Yao, Y.-D. (2010). An adaptive cooperation diversity scheme with best-relay selection in cognitive radio networks. IEEE Transactions of Signal Processing, 58(10), 5438–5445.
Proakis, J. (2001). Digital communications. New York: McGraw-Hill.
Hasna, M. O., & Alouini, M.-S. (2003). Outage probability of multihop transmission over Nakagami fading channels. IEEE Communications Letters, 7(5), 216–218.
Hasna, M. O., & Alouini, M.-S. (2004). Harmonic mean and end-to-end performance of transmission systems with relays. EEE Transactions on Communications, 52(1), 130–135.
Karagiannidis, G., Tsiftsis, T., Mallik, R., Sagias, N., & Kotsopoulos, S. (2005). Closed-form bounds for multihop relayed communications in Nakagami-m fading. In Proceedings of the IEEE international conference on communications (ICC) (Vol. 4, pp. 2362–2366).
Karagiannidis, G., Tsiftsis, T., & Mallik, R. (2006). Bounds for multihop relayed communications in Nakagami-m fading. IEEE Transactions on Communications, 54(1), 18–22.
Laneman, J., & Wornell, G. (2000). Energy-efficient antenna sharing and relaying for wireless networks. Proceedings of the IEEE Wireless Communications and Networking Confernce (WCNC)., 1, 7–12.
Farhadi, G., & Beaulieu, N. (2009). On the ergodic capacity of multi-hop wireless relaying systems. IEEE Transactions on Wireless Communications, 8(5), 2286–2291.
Simon, M. K., & Alouini, M.-S. (2000). Digital communication over fading channels. New York: Wiley.
Papoulis, A., & Pillai, S. U. (2002). Probability, random variables and stochastic processes. New York: McGraw-Hill Book Company.
Akkouchi, M. (2008). On the convolution of exponential distributions. The Journal of Chungcheong Mathematical Society, 21(4), 501–510.
Prudnikov, A. P., Brychkov, Y., & Marichev, O. (1986). Integrals and series, volume 1: Elementary functions. New York: Gordon & Breach Science Publishers.
Prudnikov, A. P., Brychkov, Y., & Marichev, O. (1986). Integrals and series, volume 2: Special functions. New York: Gordon & Breach Science Publishers.
Author information
Authors and Affiliations
Corresponding author
Appendices
Appendix 1: Proof of Proposition 1
Proof
CDF and the PDF of the random variable T can be found in [16, 17]. For the convenience of the reader we deduce the the CDF of the RV T conditioned on \(X, F_{T|X}(t|x)\), here again. From the definition of CDF we get
We can write (57) from the fact that
As X and Y are independent, by simply using CDF of RV Y i.e. CDF of exponential distribution in (57) we get the CDF of the a RV T as
By differentiating (59) with respect to t we get the PDF as
From the definition, MGF expressed in (9) can be found by simply evaluating the following integrals
Appendix 2: Proof of Corollary 1
Proof
Directly following the proof of proposition 1, the CDF is obtained in [16, 17] as
The corresponding PDF is derived in [16, 17] by differentiating (62) as
Using standard derivation of MGF as in (61), we can find MGF of RV T in (10).
Rights and permissions
About this article
Cite this article
Kundu, C., Jindal, A. & Bose, R. Secrecy Outage of Dual-Hop Amplify-and-Forward Relay System with Diversity Combining at the Eavesdropper. Wireless Pers Commun 97, 539–563 (2017). https://doi.org/10.1007/s11277-017-4518-3
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-017-4518-3