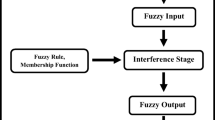
Abstract
In order to analyze the methods of music content research, this paper systematically introduces the fuzzy classification, then constructs the basic framework of music content authentication based on fuzzy classification, in which the content of music with Chroma features were extracted. At the same time, the robust Hash is calculated to verify the accuracy of algorithm to distinguish ability to maintain content operation and malicious tampering and tamper localization. The authentication algorithm of the music signal is divided into a series of unequal note segments, so that each certification unit contains the complete semantic information, and effectively solve the problem of lost synchronization in time domain algorithms exist, for each note fragment extraction contains rich information of the characteristics of middle melody. On this basis, the robust values were calculated, and the metrics were defined based on the statistical and time distribution characteristics that differ from the original music values. In this experiment, the fuzzy logic method was used to classify and made the authentication decision.








Similar content being viewed by others
Change history
13 December 2022
This article has been retracted. Please see the Retraction Notice for more detail: https://doi.org/10.1007/s11277-022-10135-z
References
Preissler, P., Kordovan, S., Ullrich, A., et al. (2016). Favored subjects and psychosocial needs in music therapy in terminally ill cancer patients: A content analysis. BMC Palliative Care, 15(1), 48.
Brooks, W. L. (2015). Music in infant-directed digital video discs: A content analysis. Music Education Research, 17(2), 141–161.
Baveye, Y., Dellandrea, E., Chamaret, C., et al. (2015). Liris-accede: A video database for affective content analysis. IEEE Transactions on Affective Computing, 6(1), 43–55.
Tsiris, G., Spiro, N., Pavlicevic, M., et al. (2014). What does the past tell us? A content analysis of the first quarter-century of the British Journal of Music Therapy. British Journal of Music Therapy, 28(1), 4–24.
Melin, P., Olivas, F., Castillo, O., et al. (2013). Optimal design of fuzzy classification systems using PSO with dynamic parameter adaptation through fuzzy logic. Expert Systems with Applications, 40(8), 3196–3206.
Lin, Y. H., & Tsai, M. S. (2014). Non-intrusive load monitoring by novel neuro-fuzzy classification considering uncertainties. IEEE Transactions on Smart Grid, 5(5), 2376–2384.
Karagiannis, A., Cauli, B., Battaglia, D., et al. (2013). Beyond the frontiers of neuronal types: fuzzy classification of interneurons. BMC neuroscience, 14(1), 56.
Luo, F., Dong, Z., Chen, G., et al. (2015). Advanced pattern discovery-based fuzzy classification method for power system dynamic security assessment. IEEE Transactions on Industrial Informatics, 11(2), 416–426.
Jiménez, F., Sánchez, G., Juárez, J. M., et al. (2014). Multi-objective evolutionary algorithms for fuzzy classification in survival prediction. Artificial Intelligence in Medicine, 60(3), 197–219.
Mastropietro, D. J., & Omidian, H. (2015). Abuse-deterrent formulations: Part 1-development of a formulation-based classification system. Expert opinion on drug metabolism & toxicology, 11(2), 193–204.
Sowmya, K. N., & Chennamma, H. R. (2015). A survey on video forgery detection. International Journal of Computer Engineering and Applications, 9(2), 17–27.
Rigoni, R., Freitas, P. G., Farias, M. C., et al. (2016). Detecting tampering in audio-visual content using QIM watermarking. Information Sciences, 328(9), 127–143.
Xiao, S., & Xu, Z. (2017). Reliable and energy efficient communication algorithm in hierarchical wireless sensor networks. Wireless Personal Communications, 95(3), 1891–1909.
Acknowledgements
This work was supported by general project of research on philosophy and social science of colleges and universities in Jiangsu (2016SJD760060) .
Author information
Authors and Affiliations
Corresponding author
About this article
Cite this article
Li, Z., Gao, X. RETRACTED ARTICLE: Research on the Method of Music Content Analysis Based on Fuzzy Classification. Wireless Pers Commun 102, 1949–1962 (2018). https://doi.org/10.1007/s11277-018-5248-x
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-018-5248-x