Abstract
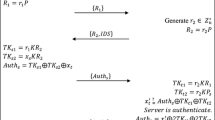
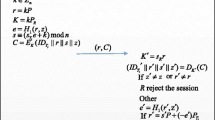
The existing RFID (Radio Frequency Identification) security protocol lacks the key establishment mechanism, assuming only that both parties of the authentication protocol have shared their respective session keys. However, key establishment is an integral part of the RFID security system. This article first introduces the elliptic curve related mathematical theory foundation. Then we establish the key negotiation mechanism, and analyze the correctness and rationality of the negotiation mechanism. Finally, we design the authentication protocol based on elliptic curve in mobile RFID system, analyze the protocol authentication process, and compare the security and performance with other protocols, which shows that the authentication protocol has more efficient performance and the ability to resist all kinds of attacks.


Similar content being viewed by others
References
Zhao, Z. (2014). A secure RFID authentication protocol for healthcare environments using elliptic curve cryptosystem. Journal of Medical Systems, 38(5), 1–7.
Kumar, N., Kaur, K., Misra, S. C., & Iqbal, R. (2016). An intelligent RFID-enabled authentication scheme for healthcare applications in vehicular mobile cloud. Peer-to-Peer Networking and Applications, 9(5), 824–840.
Niu, B., Zhu, X., & Li, H. (2013). An ultralightweight and privacy-preserving authentication protocol for mobile RFID systems. In Wireless communications and NETWORKING conference. IEEE, pp. 1864–1869.
Kumar, A., & Om, H. (2016). Lightweight, ECC Based RFID authentication scheme for WLAN. International Journal of Business Data Communications and Networking, 12(2), 89–103.
Cong, G., Zhang, Z. J., Zhu, L. H., et al. (2014). A novel secure group RFID authentication protocol. The Journal of China Universities of Posts and Telecommunications, 21(1), 94–103.
Jin, C., Xu, C., Zhang, X., et al. (2016). A secure ECC-based RFID mutual authentication protocol to enhance patient medication safety. Journal of Medical Systems, 40(1), 1–6.
Liao, Y. P., & Hsiao, C. M. (2014). A secure ECC-based RFID authentication scheme integrated with ID-verifier transfer protocol. Ad Hoc Networks, 18(7), 133–146.
Chou, J. S. (2014). An efficient mutual authentication RFID scheme based on elliptic curve cryptography. The Journal of Supercomputing, 70(1), 75–94.
Chou, J. S., Chen, Y., Wu, C. L., et al. (2011). An efficient RFID mutual authentication scheme based on ECC. IACR Cryptology Eprint Archive, 2011, 418.
Chien, H. Y. (2017). Elliptic curve cryptography-based RFID authentication resisting active tracking. Wireless Personal Communications, 94(4), 2925–2936.
Chen, Y. L., & Chou, J. S. (2015). ECC-based untraceable authentication for large-scale active-tag RFID systems. Electronic Commerce Research, 15(1), 97–120.
Tuyls, P., & Batina, L. (2006). RFID-tags for anti-counterfeiting. Lecture Notes in Computer Science, 3860, 115–131.
Yong, K. L., Batina, L., & Verbauwhede, I. (2008). EC-RAC (ECDLP Based Randomized Access Control): Provably secure RFID authentication protocol. In IEEE international conference on RFID. IEEE, pp. 97–104.
Batina, L., Guajardo, J., Kerins, T., et al. (2007). Public-key cryptography for RFID-Tags. In IEEE international conference on pervasive computing and communications workshops, 2007. Percom workshops. IEEE, pp. 217–222.
Zhou, J., Zhou, Y., Xiao, F., et al. (2012). Mutual authentication protocol for mobile RFID systems. Journal of Computational Information Systems, 8(8), 3261–3268.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Liu, G., Zhang, H., Kong, F. et al. A Novel Authentication Management RFID Protocol Based on Elliptic Curve Cryptography. Wireless Pers Commun 101, 1445–1455 (2018). https://doi.org/10.1007/s11277-018-5771-9
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-018-5771-9