Abstract
In this paper, we consider two-way relaying networks (TWRNs) in which information of two users randomly exchange via buffer-aided relay. We assume that all nodes work on half-duplex decode-and-forward for relaying of data packets. The relay is equipped with two finite-size buffers and both the users know the exact number of data packets. The data packets are scheduling with different channel access probabilities to avoid collision at relay. The protocols are developed on the basis of selective transmission scheme with states of Markov chain at relay for buffer state information (BSI) and Hybrid buffer state information/channel state information (BSI/CSI). On the basis of these protocols, we investigate closed-from expressions of maximum achievable sum throughput and end-to-end throughput for TWRNs. The numerical results are obtained with the help of CVX software package. Our proposed scheme significantly outperforms the existing two-way buffer-aided relaying scheme in literature.






Similar content being viewed by others
References
Cover, T. M., & Thomas, J. A. (2006). Element of information theory (2nd ed., pp. 509–611). London: Wiley. (Chapter 5).
Bhushan, N., Li, J., Malladi, D., Gilmore, R., Brenner, D., Damnjanovic, A., et al. (2014). Network densification: the dominant theme for wireless evolution into 5G. IEEE Communications Magazine, 52(2), 82–89.
Wu, Y., Chou, P. A., & Kung, S. Y. (2005). Information exchange in wireless network coding and physical-layer broadcast. In Proceedings of the 39th annual conference on science systems (pp. 1–6).
Popovski, P., & Yomo, H. (2007). Wireless network coding by amplify-and-forward for bi-directional traffic flows. IEEE Communications Letters, 11(1), 16–18.
Rankov, B., & Wittneben, A. (2007). Spectral efficient protocols for half-duplex fading relay channel. IEEE Journal on Selected Areas in Communications, 25(2), 379–389.
Li, Q., Ting, S. H., Pandharipande, A., & Han, Y. (2008). Outage analysis for adaptive two-way relaying. In IEEE 19th international symposium on personal, indoor and mobile radio communications (pp. 1–5).
Ding, Z., Krikidis, I., Thompson, J., & Leung, K. K. (2011). Physical layer network coding and precoding for the two-way relay channel in cellular systems. IEEE Transactions on Signal Processing, 59(2), 696–712.
Liang, X., Jin, S., Gao, X., & Wong, K.-K. (2013). Outage performance for decode-and-forward two-way relay network with multiple interferers and noisy relay. IEEE Transactions on Wireless Communications, 61(2), 521–531.
Hyadi, A., Benjillali, M., & Alouini, M. S. (2015). Outage performance of decode-and-forward in two-way relaying with outdated CSI. The IEEE Transactions on Vehicular Technology, 64(12), 5940–5947.
Liu, H., Popovski, P., Carvalho, E. D., & Zhao, Y. (2013). Sum-rate optimization in a two-way relay network with buffering. IEEE Communications Letters, 17(1), 95–98.
Shim, Y., & Park, H. (2014). A closed-form expression of optimal time for two-way relay using DF MABC protocol. IEEE Communications Letters, 18(5), 721–724.
Cho, D. S., Shim, Y., & Park, H. (2014). Optimal time allocation for two-way relay channel using physical-layer network coding. IET Communications, 8(14), 2469–2475.
Yang, Y., Bai, L., Chen, C., Jin, Y., & Choi, J. (2015). Fairness-aware power allocation in two-way decode-and-forward relay systems. Electronics Letters, 51(1), 52–54.
Jamali, V., Zlatanov, N., & Schober, R. (2015). Bidirectional buffer-aided relay networks with fixed rate transmission-Part I: Delay-unconstrained case. IEEE Transactions on Wireless Communications, 14(3), 1323–1338.
Jamali, V., Zlatanov, N., & Schober, R. (2015). Bidirectional buffer-aided relay networks with fixed rate transmission-Part II: Delay-constrained case. IEEE Transactions on Wireless Communications, 14(3), 1339–1355.
Shi, S., Li, S., & Tian, J. (2016). Markov modeling for two-way relay with finite buffer. IEEE Communications Letters, 20(4), 768–771.
Shi, S., Ni, W., & Liu, R. P. (2017). Performance analysis of XOR two-way relay with finite buffers and instant scheduling. IET Communications, 11(4), 507–513.
Liu, R., Popovski, P., & Wang, G. (2017). Decoupled uplink and downlink in a wireless system with buffer-aided relaying. IEEE Transactions on Wireless Communications, 65(4), 1507–1517.
Kumar, R., & Hossain, A. (2017). Optimisation of throughput of two-way buffer-aided relaying networks with wireless assisted links. IET Communications, 11(10), 1626–1632.
Sztrik, J. (2012). Queuing theory (pp. 15–16). Debrecen: University of Debreen: Faculty of Informatics. (Chapter 1).
Gross, D., Shortle, J. F., Thompson, J. M., & Harris, C. M. (2008). Fundamentals of queueing theory (4th ed., pp. 49–115). London: Wiley. (Chapter 2).
Boyd, S., & Vandenberghe, L. (2004). Convex optimization (pp. 127–189). Cambridge: Cambridge University Press.
Grant, M., & Boyd, S. (2014). CVX: MATLAB software for disciplined convex programming, version 2.1. http://cvxr.com/cvx. Accessed March 2014.
Papoulis, A., & Pillai, S. U. (2002). Probability, random variables, and stochastic processes (4th ed., pp. 169–242). New York: McGraw Hill Education. (Chapter 6).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendices
Appendix 1
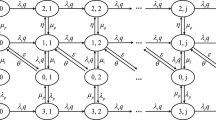
In this appendix, we compute the outage probability discussed in Sect. 3.1. The probability of events \(Pr\left( {{\mathcal{S}}_{1} } \right)\) to \(Pr\left( {{\mathcal{S}}_{6} } \right)\) can be expressed as,
For Rayleigh fading, probability density functions (pdfs) of instantaneous SNRs \(\gamma_{1} \left( i \right)\) and \(\gamma_{2} \left( i \right)\) are defined [14] as \(f_{{\gamma_{1} }} \left( {\gamma_{1} } \right) = \frac{1}{{\Omega _{1} \gamma }}exp\left( { - \gamma_{1} /\left( {\Omega _{1} \gamma } \right)} \right)\) and \(f_{{\gamma_{2} }} \left( {\gamma_{2} } \right) = \frac{1}{{\Omega _{2} \gamma }}exp\left( { - \gamma_{2} /\left( {\Omega _{2} \gamma } \right)} \right)\). We draw the lines using (28) as shown in Fig. 7. The joint pdf is defined in [24] as \(f_{{\gamma_{1} \gamma_{2} }} \left( {\gamma_{1} , \gamma_{2} } \right) = f_{{\gamma_{1} }} \left( {\gamma_{1} } \right) f_{{\gamma_{2} }} \left( {\gamma_{2} } \right)\) for non-outage regions \(\left\{ {Z_{{\gamma_{1} }} , Z_{{\gamma_{2} }} } \right\}\). The outage probability of \(u_{1} - r\) link is defined as,
We assume that \(u_{1} - r\) channel is reciprocal to \(r - u_{1}\) channel i.e., \({\mathcal{P}}_{1r} = {\mathcal{P}}_{r1}\). Similarly, we obtain outage probability of \(u_{2} - r\) link, \({\mathcal{P}}_{2r}\) discussed in (2). Again, we assume that \(u_{2} - r\) channel is reciprocal to \(r - u_{2}\) channel i.e., \({\mathcal{P}}_{2r} = {\mathcal{P}}_{r2}\).
For multi-access channel, probability of successful transmission of both users is shown in Fig. 7 by non-outage region \(\Delta _{1}\).Thus, outage probability of multiple access channel, \({\mathcal{P}}_{MA} = 1 - Pr\left( {\left( {\gamma_{1} + \gamma_{2} } \right) \ge \gamma_{0}^{sum} } \right)\) in TWRNs is defined as,
By substituting value of joint pdfs \(f_{{\gamma_{1} \gamma_{2} }} \left( {\gamma_{1} , \gamma_{2} } \right)\) in (30), we obtain (3). The outage probability of broadcast channel in TWRNs is defined as,
Considering (31) and substituting the value of joint pdfs \(f_{{\gamma_{1} \gamma_{2} }} \left( {\gamma_{1} , \gamma_{2} } \right)\), we obtain (4). We investigate non-outage events \({\mathcal{S}}_{12}\) and \({\mathcal{S}}_{21}\) which are responsible for successfully deliver of data packers from user 1-to-user 2 and from user 2-to-user 1 respectively and these are expressed as,
Considering (32a), outage probability of TWRNs from user 1-to-user 2 is formulated as,
In (33), the integration expression indicates that the summation of integration is computed over the lower limits and upper limits of sets, \(\left\{ { \Delta_{1,lo} , \Delta_{1,up} } \right\}\), \(\left\{ {\Delta_{2,lo} , \Delta_{2,up} } \right\}\), \(\left\{ { \Delta_{3,lo} , \Delta_{3,up} } \right\}\) and \(\left\{ { \Delta _{4,lo} ,\Delta _{4,up} } \right\}\) of regions \(\Delta _{1}\), \(\Delta _{2}\), \(\Delta _{3}\), and \(\Delta _{4}\). By evaluating (33), we obtain (5). From Fig. 7, it is clear that the non-outage region of event \({\mathcal{S}}_{21}\) is identical to non-outage region of event \({\mathcal{S}}_{21}\). Thus, outage probability from user 1-to-user 2 is equal to outage probability from user 2-to-user 1 i.e., \({\mathcal{P}}_{12}^{out} = {\mathcal{P}}_{21}^{out}\).
Appendix 2
Using (6a) and (8a) we can write,
where \({{\mathcal{X}}}_{{n}} = \prod \nolimits_{{{i} = {{1}}}}^{{n}} \frac{{{\alpha}_{{i}} }}{{\overline{{{\alpha}_{{i}} }} }}\) and it can be rearranged as \({{\mathcal{X}}}_{{n}} = \frac{{{\alpha}_{{n}} }}{{\overline{{{\alpha}_{{n}} }} }}{{\mathcal{X}}}_{{{n} - {\mathbf{1}}}}\).Thus, \(\alpha_{{n}}\) can be written in term of \({{\mathcal{X}}}_{{n}}\) as \({\alpha}_{{n}} = \frac{{{{\mathcal{X}}}_{{n}} }}{{{{\mathcal{X}}}_{{n}} + {{\mathcal{X}}}_{{{n} - {{1}}}} }}\). Substituting \({\alpha}_{{n}}\) in (34), we obtain steady-state probability as,
Since, we have \(\mathop \sum \nolimits_{{{n} = {{0}}}}^{{N}} {{\mathcal{V}}}_{{n}} = {{1}}\). Considering (35), we can write initial steady-state term as,
Substituting (34) and (36) in (11), we obtain (13a). Similarly, we can write (13b) for relaying of buffer \(B_{2}\) at relay. We consider \({\mathcal{X}}_{0} = 1\) then denominator of (13a) can be expressed as,
Substituting (37) in (13a), we can write
If birth–death MC is at \(N\) state, the buffer \(B_{1}\) at relay drops data packets i.e., overflow condition. In this scenario, \(u_{1}\) transmits with probability, \(\alpha_{N} = 0\). Thus, \({\mathcal{X}}_{N} = 0\) and then (38) can be written as,
Substituting the value of \(K\) in (39), we obtain (15a). Similarly, we can obtain \({\mathcal{R}}_{21}^{B}\) for TWRNs that has been expressed in (15b).
Appendix 3
With consideration of (22) and (23), we can express the sum throughput of TWRNs as,
From (40), we observe that the sum throughput should be maximized by maximizing the term \(\left( {\Lambda _{12} +\Lambda _{21} } \right)\). In our problem, the set of variable \(\left\{ \phi \right\}_{n = 1}^{N}\) is used to express the term \(\Lambda _{12}\) while the set of variables \(\left\{ \psi \right\}_{m = 1}^{M}\) is used to express the term \(\Lambda _{21}\). Both terms \(\Lambda _{12}\) and \(\Lambda _{21}\) are independent from each other. Thus, sum throughput is maximized individually with maximization of \(\Lambda _{12}\) and \(\Lambda _{21}\). For maximization of \(\Lambda _{12}\), we consider global balance condition and is expressed as,
Substituting (8a), (17a) and (21a) in (41), we yield an expression as,
We rearrange the terms in (42) and it can be written as,
The coefficients \(e\) and \(f\) are conferred in (25). By setting \(\xi_{0} = 1\) and \(\phi_{0} = 1\) and summing both sides of (43) from \(n = 1\) to (N − 1), we get
Considering (43), we can write \(\left\{ {\xi_{n} } \right\}_{n = 1}^{N}\) as,
Substituting (44) in (22) of \(\varLambda_{12}\), we obtain objective function in linear-fractional program (26) which is shown in vector form. The constraints are obtained from basic assumption, range of transmit channel access probability, and overflow condition of \(B_{1}\) by considering vector form of (45). We follow similar mathematical operation discussed in (26) to obtain the expression of (27). Combining (26) and (27), we obtain sum throughput in form of linear-fractional program discussed in (24).
Rights and permissions
About this article
Cite this article
Kumar, R., Hossain, A. Performance of Random Access Markov Modelling for Two-Way Buffer-Aided Relaying Networks with Wireless Assisted Links. Wireless Pers Commun 108, 1995–2015 (2019). https://doi.org/10.1007/s11277-019-06505-9
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-019-06505-9