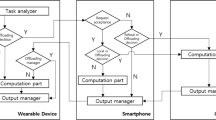
Abstract
Computation offloading effectively expands the usability of mobile terminals beyond their physical limits, and also greatly extends their battery charging intervals. Offloading or cyber foraging is a technique by which large and complex computational jobs are relocated from lightweight portable devices (such as smartphones) called offloadee to powerful servers (such as nearby laptops/desktops or cloud server over the Internet) called surrogates, and getting the output back at the offloadee. Many research works have been done so far on the architecture of offloading systems, but only few works can be found on fault detection and tolerance. So this paper concentrates on categorizing different failures that may affect the benefit of offloading computation and proposes a fault-tolerance approach to alleviate those faults. The checkpoint based fault-tolerance approach proposed in this paper is able to handle crash, omission and transient failures altogether. Fault prevention is obtained by utilizing historical data for choosing worthy surrogate from known neighborhood. This fault tolerance model is evaluated by applying a real application named \(\pi\)calculator and Scimark benchmark suite. The system is implemented and the proposed approach is found to be effective with respect to energy consumption and resource utilization even in case of crash and omission failure.












Similar content being viewed by others
References
Ou, S., Wu, Y., Yang, K., & Zhou, B. (2008). Performance analysis of fault-tolerant offloading systems for pervasive services in mobile wireless environments. In IEEE international conference on communications, 2008. ICC’08 (pp. 1856–1860).
Satyanarayanan, M. (2001). Pervasive computing: Vision and challenges. IEEE Personal Communications, 8(4), 10–17.
Cuervo, E., Balasubramanian, A., Cho, D. K., Wolman, A., Saroiu, S., Chandra, R., & Bahl, P. (2010). MAUI: Making smartphones last longer with code offload. In Proceedings of the 8th international conference on mobile systems, applications, and services (pp. 49–62). ACM.
Bhagat, N., & Bhushan, S. (2016). Energy efficient offloading for mobile cloud computing: A review. International Journal of Advanced Engineering Research and Applications., 2(2), 65–71.
Powell, M. L., & Miller, B. P. (1983). Process migration in demos/mp. Proceedings of the Ninth ACM Symposium on Operating Systems Principles SOSP ’83, 17(5), 110–119.
Kumar, K., Liu, J., Lu, Y. H., & Bhargava, B. (2013). A survey of computation offloading for mobile systems. Mobile Networks and Applications, 18(1), 129–140.
Kemp, R., Palmer, N., Kielmann, T., & Bal, H. (2012). Cuckoo: A computation offloading framework for smartphones. In M. Gris & G. Yang (Eds.), Mobile computing, applications, and services. MobiCASE 2010. Lecture Notes of the Institute for Computer Sciences, Social Informatics and Telecommunications Engineering (Vol. 76). Springer.
Park, S., Chen, Q., Han, H., & Yeom, H. Y. (2014). Design and evaluation of mobile offloading system for web-centric devices. Journal of Network and Computer Applications, 40, 105–115.
Yang, K., Ou, S., & Chen, H. H. (2008). On effective offloading services for resource-constrained mobile devices running heavier mobile internet applications. IEEE Communications Magazine, 46(1), 56–63.
Chen, X., Chen, S., Zeng, X., Zheng, X., Zhang, Y., & Rong, C. (2017). Framework for context-aware computation offloading in mobile cloud computing. Journal of Cloud Computing: Advances, Systems and Applications. Hindawi, 6(1), 71:1–71:17.
Kwon, D., Yang, S., Paek, Y., & Ko, K. (2017). Optimization techniques to enable execution offloading for 3D video games. Journal of Multimedia Tools and Applications, 76(9), 11347–11360.
Haghighi, V., & Moayedian, N. S. (2018). An offloading strategy in mobile cloud computing considering energy and delay constraints. Publihed in IEEE Access, 6, 11849–11861.
Jin, X., Liu, Y., Fan, W., Wu, F., & Tang, B. (2017). Multisite computation offloading in dynamic mobile cloud environments. Journal of Science China Information Sciences, 60, 89301.
Chen, G., Kang, B. T., Kandemir, M., Vijaykrishnan, N., Irwin, M. J., & Chandramouli, R. (2004). Studying energy tradeoffs in offloading computation/compilation in java-enabled mobile devices. IEEE Transactions on Parallel and Distributed Systems, 15(9), 795–809.
Li, Z., Wang, C., & Xu, R. (2001). Computation offloading to save energy on handheld devices: A partition scheme. In Proceedings of the 2001 international conference on compilers, architecture, and synthesis for embedded systems (pp. 238–246). ACM.
Goyal, M., & Saini,P. (2016). A fault-tolerant energy-efficient computational offloading approach with minimal energy and response time in mobile cloud computing. In: Proceedings of 4th international conference on parallel, distributed and grid computing.
Xia, F., Ding, F., Li, J., Kong, X., Yang, L. T., & Ma, J. (2014). Phone2Cloud: Exploiting computation offloading for energy saving on smartphones in mobile cloud computing. Journal of Information Systems Frontiers, 16(1), 95–111.
Jun, Y., Lee, J., & Seo, E. (2017). Evaluation of remote-I/O support for a DSM-based computation offloading scheme. Journal of Computer Science and Technology, 32(5), 957–973.
Wang, Q., & Wolter, K. (2014). Detection and analysis of performance deterioration in mobile offloading system. In 2014 IEEE international symposium on software reliability engineering workshops (ISSREW) (pp. 420–425). IEEE.
Meng, T., Wang, Q., & Wolter, K. (2015). Model-based quantitative security analysis of mobile offloading systems under timing attacks. In M. Gribaudo, D. Manini & A. Remke (Eds.), Analytical and stochastic modelling techniques and applications. ASMTA 2015. Lecture Notes in Computer Science (Vol. 9081, pp. 143–157). Springer.
Mondal, S., Chowdhury, C., Roy, S., Deb, S. K., & Neogy, S. (2016). Crash failure immune offloading framework. In IEEE international conference proceedings of advanced networks and telecommunications systems (ANTS) (pp. 1–6).
Brumley, D., & Boneh, D. (2005). Remote timing attacks are practical. Computer Networks, 48(5), 701–716.
Abd, S. K., Al Haddad, S. K. R., Abdullah, A. B. H. J., & Yussof, S. (2017). Energy-aware fault tolerant task offloading of mobile cloud computing. In Proceedings of 5th IEEE international conference on mobile cloud computing, services, and engineering (pp. 161–164).
Kwon, Y., & Tilevich, E. (2012). Energy efficient and fault tolerant distributed mobile execution. In Proceedings of 32nd IEEE international conference on distributed computing systems (pp. 586–595).
Gordon, M. S., Jamshidi, D. A., Mahlke, S., Mao, Z. M., & Chen, X. (2012). Comet: Code offload by migrating execution transparently. In 10th USENIX symposium on operating systems design and implementation (OSDI 12) (pp. 93–106).
Huang, Y., Kintala, C., Kolettis, N., & Fulton, N. D. (1995). Software rejuvenation: Analysis, module and applications. In Twenty-fifth international symposium on fault-tolerant computing, 1995. FTCS-25. digest of papers (pp. 381–390).
Cotroneo, D., Natella, R., Pietrantuono, R., & Russo, S. (2011). Software aging and rejuvenation: Where we are and where we are going. In 2011 IEEE third international workshop on software aging and rejuvenation (WoSAR) (pp. 1–6).
Van Moorsel, A., & Wolter, K. (2006). Analysis of restart mechanisms in software systems. IEEE Transactions on Software Engineering, 32(8), 547–558.
Ou, S., Yang, K., & Hu, L. (2007). Cross: A combined routing and surrogate selection algorithm forpervasive service offloading in mobile ad hoc environments. In Global telecommunications conference, 2007. GLOBECOM’07 (pp. 720–725). IEEE.
Rebeiro, C., Mukhopadhyay, D., & Bhattacharya, S. (2015). An introduction to timing attacks. In Timing channels in cryptography (pp. 1–11). Springer.
Liu, J., & Lu, Y. H. (2010). Energy savings in privacy-preserving computation offloading with protection by homomorphic encryption. In Proceedings of the 2010 international conference on power aware computing and systems, HotPower (Vol. 10, pp. 1–7).
Liu, J., Kumar, K., & Lu, Y. H. (2010). Tradeoff between energy savings and privacy protection in computation offloading. In Proceedings of the 16th ACM/IEEE international symposium on low power electronics and design (pp. 213–218). ACM.
Sheahan, R., Lipsky, L., Fiorini, P. M., & Asmussen, S. (2006). On the completion time distribution for tasks that must restart from the beginning if a failure occurs. ACM SIGMETRICS Performance Evaluation Review, 34(3), 24–26.
http://ziyang.eecs.umich.edu/projects/powertutor/. Accessed 5 Oct 2018.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Chowdhury, C., Roy, S., Ray, A. et al. A Fault-Tolerant Approach to Alleviate Failures in Offloading Systems. Wireless Pers Commun 110, 1033–1055 (2020). https://doi.org/10.1007/s11277-019-06772-6
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-019-06772-6