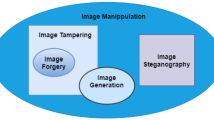
Abstract
With the extensive use of multimedia on internet and easy approachability of powerful image and video editing software, doctored visual contents have been extensively appearing in our electronic-mail in-boxes, Whatsapp, Facebook or any other social media. Recently, attempting blind tampering in visual contents have been progressively adopted. This paper presents a collaborative survey on detection of such attempts. Our aim is to establish an effective path, for researchers working in the field of image and video forensics, to unfold new aspects of forgery. This paper will avail the comprehensive study that will assist the researchers to go through the various challenges encountered in the previous work. The focus of this paper is to review the splicing and copy–move forgery detection methods in images as well as inter and intra-frame forgery challenges in videos, highlighting the commonly used datasets and hence assisting new researchers to work on with. The efficacy of the paper is that such collaborative survey under one umbrella is not available yet.











Similar content being viewed by others
References
Oommen, R. S., Jayamohan, M., & Sruthy, S. (2015). A survey of copy move forgery detection techniques for digital images. International Journal of Innovations in Engineering and Technology (IJIET),5(2), 419–426.
Singhal, N., & Gandhani, S. (2015). Analysis of copy–move forgery image forensics: A review. International journal of Signal Processing Image Processing and Pattern Recognition,8(7), 265–272.
Sharma, V., Jha, S., & Bharti, R. K. (2016). Image forgery and it’s detection technique: A review. International Research Journal of Engineering and Technology (IRJET),3(3), 756–762.
Wahab, A. W. A., et al. (2014). Passive video forgery detection techniques: A survey. In Proceedings of 10th international conference on information assurance and security (pp. 19–34).
Zhang, Z., et al. (2008). A survey on passive-blind image forgery by doctor method. Proceedings of International Conference on Machine Learning and Cybernetics,6, 3463–3467.
Jaseela, S., & Nishadha, S. G. (2016). Survey on copy move image forgery detection techniques. International Journal of Computer Science Trends and Technology (IJCST),4(1), 87–91.
Ansari, M. D., Ghrera, S. P., & Tyagi, V. (2014). Pixel-based image forgery detection: A review. IETE Journal of Education,55(1), 40–46.
Singh, R., & Thakkar, M. (2016). Copy move image forgery detection techniques: Survey. International Journal of Modern Trends in Engineering and Research,3(4), 654–657.
Singh, R. D., & Aggarwal, N. (2018). Video content authentication techniques: A comprehensive survey. Multimedia Systems,24(2), 211–240.
Hany, F. (2008). Digital image forensics. Scientific American,298(6), 66–71.
Redi, J. A., Taktak, W., & Dugelay, J. L. (2011). Digital image forensics: a booklet for beginners. Multimedia Tools Application,51(1), 133–162.
Parveen, A., Tayal, A. (2016) An algorithm to detect the forged part in an image. In Proceedings of 2nd international conference on communication and signal processing (pp. 1486–1490).
Fadl, S. M., Semary, N. O. A., & Hadhoud, M. M. (2014). Copy–rotate–move forgery detection based on spatial domain. In Proceedings of 9th international conference on computer engineering and systems (pp. 136–141).
Ren, X. (2009). An optimal image thresholding using genetic algorithm. International Forum on Computer Science-Technology and Applications,1, 169–172.
Hussain, M., Muhammad, G., Saleh, S. Q., Mirza, A. M., & Bebis, G. (2013). Copy–move image Forgery detection using multi-resolution weber descriptors. In Proceedings of 8th international conference on signal image technology and internet based systems (pp. 1570–1577).
Shahbahrami, A., Borodin, D., & Juurlink, B. (2008). Comparison between color and texture features for image retrieval. In Proceedings of conference (pp. 1–11).
Lin, S. D., & Wu, T. (2011). An integrated technique for splicing and copy–move forgery image detection. In Proceedings of 4th international conference on image and signal processing (pp. 1086–1090).
Yao, H., Qiao, T., Tang, Z., Zhao Y., & Mao, H. (2011). Detecting copy–move forgery using non-negative matrix factorization. In Proceedings of 2nd international conference on multimedia information networking and security (pp. 591–594).
Amerini, I., Ballan, L., Caldelli, R., Bimbo, A. D., & Serra, G. (2011). A SIFT-Based forensic method for copy–move attack detection and transformation recovery. IEEE Transactions on Information Forensics and Security,6(3), 1099–1110.
Lin, S. D., & Wu, T. (2011). An integrated technique for splicing and copy–move forgery image detection. In Proceedings of 4th international conference on image and signal processing (Vol. 2, pp. 1086–1091).
Agarwal, V., & Mane, V. (2016). Reflective SIFT for improving the detection of copy–move image forgery. In Proceedings of 2nd international conference on research in computational intelligence and communication networks (pp. 84–88).
Shahroudnejad, A., & Rahmati, M. (2016). Copy–move forgery detection in digital images using affine-SIFT. In Proceedings of 2nd international conference of signal processing and intelligent systems (pp. 1–5).
Ting, Z., & Rang-ding, W. (2009). Copy–move forgery detection based on SVD in digital image. In Proceedings of 2nd international conference on image and signal processing (pp. 1–5).
He, Z., Lu, W., Sun, W., & Huang, J. (2012). Digital image splicing detection based on markov features in DCT and DWT domain. Pattern Recognition,45(12), 4292–4299.
Sridevi, M., Mala, C., & Sandeep, S. (2012). Copy – move image forgery detection in a parallel environment. In Proceedings of CS & IT Computer science conference proceedings (CSCP) (pp. 19–29).
Kang, L., & Cheng, X. P. (2010). Copy–move forgery detection in digital image. In Proceedings of 3rd international congress on image and signal processing (CISP) (Vol. 5, pp. 2419–2421).
Li, H., Luo, W., Qiu, X., & Huang, J. (2017). Image forgery localization via integrating tampering possibility maps. IEEE Transactions on Information Forensics and Security,12, 1–13.
Al-Sanjary, O. I., & Sulong, G. (2015). Detection of video forgery: A review of literature. Journal of Theoretical and Applied Information Technology,74(2), 217–218.
Vidyadharan, D. S., & Thampi, S. M. (2015). Detecting spliced face in a group photo using PCA. In Proceedings of 7th international conference of soft computing and pattern recognition (pp. 175–180).
Tralic, D., Zupancic, I., Grgic, S., & Grgic, M. (2013). CoMoFoD—New database for copy–move forgery detection. In International symposium electronics in marine (pp. 49–54).
CASIA image tempering detection evaluation database (CAISA TIDE) V1.0 and V2.0. (2016). Retrieved March 30, 2016 from, http://forensics.idealtest.org/.
Wen, B., Zhu, Y., Subramanian, R., Ng, T., Shen, X., & Winkler, S. (2016). COVERAGE—A novel database for copy–move forgery detection. In Proceedings of IEEE international conference on image processing (pp. 161–165).
Surrey University library for forensic analysis (SULFA) of video content database. (2017). Retrieved May 5, 2017 from, http://sulfa.cs.surrey.ac.uk/forged_1.php.
REWIND copy–move forgery dataset for video-testing provided by SULFA. (2017). Retrieved July 10, 2017 from, https://sites.google.com/site/rewindpolimi/downloads/datasets/videocopy-move-forgeries-dataset.
Fridrich, A. J., Soukal, B. D., & Lukáš, A. J. (2003). Detection of copy–move forgery in digital images. In Digital forensic research workshop (DRWS) (pp. 19–23).
Bayram, S., Sencar, H. T., & Memon, N. (2009). An efficient and robust method for detecting copy–move forgery. In Proceedings of IEEE international conference on acoustics, speed and signal processing (ICASSP) (pp. 1053–1056).
Zhang, J., Feng, Z., & Su, Y. (2008). A New approach for detecting copy–move forgery in digital images. In Proceedings of IEEE international conference on communication systems (pp. 362–366).
Junhong, Z. (2010). Detection of copy–move forgery based on one improved LLE method. In Proceedings of 2nd international conference on advanced computer control (pp. 547–549).
Qureshi, M. A., & Deriche, M. (2014). A review on copy move image forgery detection techniques. In Proceedings of IEEE 11th international multi-conference on systems, signals and devices (pp. 1–5).
Ardizzone, E., Bruno, A., & Mazzola G. (2010). Detecting multiple copies in tampered images. In Proceedings of IEEE 17th international conference on image processing (pp. 2117-2120).
Liu, L., Ni, R., Zhao, Y., & Li, S. (2014). Improved SIFT-based copy–move detection using BFSN clustering and CFA features. In Proceedings of 10th international conference on intelligent information hiding and multimedia signal processing (pp. 626–629).
Vidhi, R., & Khushbu, S. (2014). An integrated technique DCT & SIFT for detection of image forgery. International Journal for Technological Research in Engineering,1(10), 1190–1195.
Debbarma, S., Singh, A. B., & Singh, K. M. (2014). Key points based copy–move forgery detection of digital images. In Proceedings of international conference on informatics electronics & vision (pp. 1–5).
Li, J., Li, X., Yang, B., & Sun, X. (2015). Segmentation-based image copy–move forgery detection scheme. IEEE Transactions on Information Forensics and Security,10(3), 507–518.
Manu, V. T., & Mehtre, B. M. (2015). Detection of copy–move forgery in images using segmentation and SURF. Advances in Signal Processing and Intelligence in Recognition Systems,425, 645–654.
Shandilya, M., & Naskar, R. (2015). Detection of geometric transformations in copy move forgery of digital images. In Proceedings of annual IEEE India conference (INDICON) (pp. 1–6).
Ustubioglu, B., Muzaffer, G., Ulutas, G., Nabiyev, V., & Ulutas, M. (2015). A novel keypoint based forgery detection method based on local phase quantization and SIFT. In Proceedings of 2nd International conference on electrical and electronics engineering (pp. 185–189).
Sharma, P., Singla, S., & Kaur, S. (2016). Detecting copy–move forgery in digital image using SIFT. International Journal of Latest Trends in Engineering and Technology,7(3), 199–204.
Bhullar, L. K., Budhirajam, S., & Dhindsa, A. (2014). DWT and SIFT based passive copy–move forgery detection. International Journal of Computer Applications,95(23), 14–18.
Datta, U., & Sharma, C. (2013). Analysis of copy–move image forgery detection. International Journal of Advanced Research in Computer Science and Electronics Engineering,2(8), 607–609.
Ustubioglu, B., Ayas, S., Doğan, H., & Ulutaş, G. (2015). Image forgery detection based on colour SIFT. In Proceedings of 23th international conference on signal processing and communications applications (pp. 1741–1744).
Dixit, A., Dixit, R., & Gupta, R. K. (2016). Detection of copy–move forgery exploiting LBP features with discrete wavelet transform. International Journal of Computer Applications,153(3), 0975–0987.
Nguyen, H. C., & Beisser, S. K. (2012). Detection of copy–move forgery in digital images using radon transformation and Phase Correlation. In Proceedings of 8th international conference on intelligent information hiding and multimedia signal processing (pp. 134–137).
İmamoğlu, M. B., Ulutaş, G., & Ulutaş, M. (2013). Detection of copy–move forgery using krawtchouk moment. In Proceedings of 8th international conference on electrical and electronics engineering (pp. 311–314).
Zhong, L., & Xu, W. (2013). A robust image copy–move forgery detection based on mixed moments. In Proceedings of 4th international conference on software engineering and service science (pp. 381–384).
Chen, Y., & Hsu, C. T. (2013). What has been tampered? From a sparse manipulation perspective. In IEEE 15th international workshop on multimedia signal processing (pp. 123–128).
Chakraborty, S. (2013). Copy move image forgery detection using mutual information. In Proceedings of 4th international conference on computing communications and networking technologies (pp. 1–4).
Ardizzone, E., Bruno, A., & Mazzola, G. (2015). Copy–move forgery detection by matching triangles of key points. IEEE Transactions on Information Forensics and Security,10(10), 2084–2094.
Ustubıoglu, B., Nabıyev, V., Ulutas, G., & Ulutas, M. (2015). Image forgery detection using colour moments. In Proceedings of 38th international conference on telecommunications and signal processing (pp. 540–544).
Saini, G. K., & Mahajan, M. (2016). Improvement in copy–move forgery detection using hybrid approach. International Journal of Modern Education and Computer Science,12, 56–63.
Kumar, S., Desai, J. V., & Mukherjee, S. (2015). A fast keypoint based hybrid method for copy move forgery detection. International Journal of Computing and Digital Systems,4(2), 91–98.
Baykal, E., Ustubioglu, B., & Ulutas, G. (2016). Image forgery detection based on SIFT and k-means ++. In Proceedings of 39th international conference on telecommunications and signal processing (TSP) (pp. 474–477).
Mohebbian, E., & Hariri, M. (2015). Increase the efficiency of DCT method for detection of copy–move forgery in complex and smooth images. In Proceedings of 2nd international conference on knowledge-based engineering and innovation (KBEI) (pp. 436–440).
Zhao, J., & Guo, J. (2013). Passive forensics for copy–move image forgery using a method based on DCT and SVD. Forensic Science International,233(1), 158–166.
Chetty, G., Biswas, M., & Singh, R. (2010). Digital video tamper detection based on multimodal fusion of residue features. In Proceedings of 4th international conference on network and system security (pp. 606–612).
Hu, J., Zhang, H., Gao, Q., & Huang, H. (2011). An improved lexicographical sort algorithm of copy–move forgery detection. In proceedings of second international conference on networking and distributed computing (pp. 23–27).
Tu, H. K., et al. (2017). Develop an algorithm for image forensics using feature comparison and sharpness estimation. In Proceedings of international conference on recent advances in signal processing, telecommunications & computing (SigTelCom) (pp. 82–88).
Qureshi, M. A., & Deriche, M. (2015). A bibliography of pixel-based blind image forgery detection techniques. Signal Processing: Image Communication,39(Part A), 46–74.
Ng, T., Chang, S., & Sun, Q. (2004). Blind detection of photomontage using higher order statistics. IEEE International Symposium on Circuits and Systems,5, 688–691.
Popescu, A. C., & Farid, H. (2005). Exposing digital forgeries by detecting traces of resampling. IEEE Transactions on Signal Processing,53(2), 758–767.
Hsu, Y. F., & Chang, S. F. (2010). Camera response functions for image forensics: An automatic algorithm for splicing detection. IEEE Transactions on Information Forensics and Security,5(4), 816–825.
Zheng, Q., Sun W., & Lu, W. (2010). Digital spliced image forensics based on edge blur measurement. In Proceedings of IEEE international conference on information theory and information security (pp. 399–402).
Ping, Z., & Xiang, Z. (2010). Image splicing detection based on image quality and analysis of variance. In Proceedings of 2nd international conference on education technology and computer (ICETC) (Vol. 4, pp. 242–246).
Lin, G. S., Chang, M. K., & Chen, Y. L. (2011). A passive-blind forgery detection scheme based on content-adaptive quantization table estimation. IEEE Transactions on Circuits and Systems for Video Technology,21(4), 421–433.
He, Z., Sun, W., Lu, W., & Lu, H. (2011). Digital image splicing detection based on approximate run length. Pattern Recognition Letters,32(12), 1591–1597.
Venkateswarlu, Y., Sujatha, B., & Kumar, V. V. (2012). Extraction of texture information from fuzzy run length matrix. International Journal of Computer Applications,55(1), 0975–8887.
Shi, Z., Shen, X., Chen, H., Li, X. (2015). Blind detection of image splicing based on fuzzy run-length. In Proceedings of IEEE international conference on computer and information technology (pp. 915–920).
Liu, H., Yang, Y., & Shang, M. (2012). Blind detection of image splicing based on run length matrix combined properties. In Proceedings of 10th world congress on intelligent control and automation (pp. 4545–4550).
Dong, J., et al. (2008). Run-length and edge statistics-based approach for image splicing detection. In Proceedings of international workshop in digital watermarking (pp. 76–87).
Mushtaq, S., & Mir, A. H. (2014). Novel method for image splicing detection. In Proceedings of international conference on advances in computing, communications and informatics (pp. 2398–2404).
Wu, X., & Fang, Z. (2011). Image splicing detection using illuminant color inconsistency. In Proceedings of 3rd international conference on multimedia information networking and security (pp. 600–603).
Binnar, P., & Mane, V. (2015). Robust technique of localizing blurred image splicing based on exposing blur type inconsistency. In Proceedings of international conference on applied and theoretical computing and communication technology (pp. 398–401).
Bahrami, K., Kot, A. C., Li, L., & Li, H. (2015). Blurred image splicing localization by exposing blur type inconsistency. IEEE Transactions on Information Forensics and Security,10(5), 999–1009.
Das, A., Medhi, A., Karsh, R. K., & Laskar, R. H. (2016). Image splicing detection using Gaussian or defocus blur. In Proceedings of international conference on communication and signal processing (pp. 1237–1241).
Agarwal, S., & Chand, S. (2016). Texture operator based image splicing detection hybrid technique. In Proceedings of 2nd international conference on computational intelligence & communication technology (pp. 116–120).
Shen, X., Shi, Z., & Chen, H. (2017). Splicing image forgery detection using textural features based on the gray level co-occurrence matrices. IET Image Processing,11(1), 44–53.
Carvalho, T., et al. (2015). Illuminant-based transformed spaces for image forensics. IEEE Transactions on Information Forensics and Security,11(4), 1–14.
Fan, Y., Carré, P., & Maloigne, C. F. (2015). Image splicing detection with local illumination estimation. In Proceedings of IEEE international conference on image processing (ICIP) (pp. 2940–2944).
Rao, Y., & Ni, J. (2016). A deep learning approach to detection of splicing and copy–move forgeries in images. In Proceedings of IEEE international workshop on information forensics and security (pp. 1–6).
Cozzolino, D., & Verdoliva, L. (2016). Single-image splicing localization through autoencoder-based anomaly detection. In Proceedings of IEEE international workshop on information forensics and security (pp. 1–6).
Hsu, Y. F., & Chang, S. F. (2007). Image splicing detection using camera response function consistency and automatic segmentation. In Proceedings of IEEE international conference on multimedia and expo (pp. 28–31).
Wang, E., Dong, J., & Tan, T. (2009). Effective image splicing detection based on image chroma. In Proceedings of 16th IEEE international conference on image processing (ICIP) (pp. 1257–1260).
Alahmadi, A. A., et al. (2013). Splicing image forgery detection based on DCT and local binary pattern. In Proceedings of IEEE global conference on signal and information processing (pp. 253–256).
El-Alfy, E. M., & Qureshi, M. A. (2015). Combining spatial and DCT based markov features for enhanced blind detection of image splicing. Pattern Analysis and Applications,18(3), 713–723.
Muhammad, G., Al-Hammadi, M. H., Hussain, M., & Bebis, G. (2014). Image forgery detection using steerable pyramid transform and local binary pattern. Machine Vision and Applications,25(4), 985–994.
Mushtaq, S., & Mir, A. H. (2014). Forgery detection using statistical features. In Proceedings of international conference on innovative applications of computational intelligence on power, energy and controls with their impact on humanity (pp. 92–97).
Agarwal, S., & Chand, S. (2016). Image forgery detection using markov features in undecimated wavelet transform. In Proceedings of 9th international conference on contemporary computing (pp. 1–6).
Sharma, S., & Dhavale, S. V. (2016). A review of passive forensic techniques for detection of copy–move attacks on digital videos. In Proceedings of 3rd international conference on advanced computing and communication systems (ICACCS) (Vol. 1, pp. 1–6)
Shih, T. K., Tang, N. C., Tsai, J. C., & Hwang, J. N. (2011). Video motion interpolation for special effect applications. IEEE Transactions on Systems, Man, and Cybernetics, Part C (Applications and Reviews),41(5), 720–732.
Chen, R., Dong, Q., Ren, H., & Fu, J. (2012). Video forgery detection based on non-subsampled contour let transformation and gradient information. Information Technology Journal,11, 1456–1462.
Wang, W., & Farid, H. (2007). Exposing digital forgeries in video by detecting duplication. In Proceedings of 9th workshop on multimedia and security (pp. 35–42).
Goodwin, J., & Chetty, G. (2011). Blind video tamper detection based on fusion of source features. In Proceedings of international conference on digital image computing techniques and applications (pp. 608–613).
Khammar, M. R. (2012). Evaluation of different block matching algorithms to motion estimation. International Journal of VLSI and Embedded Systems (IJVES),3(3), 148–153.
Wang, W., & Farid, H. (2006). Exposing digital forgeries in video by detecting double MPEG compression. In Proceedings of 8th workshop on multimedia and security (pp. 37–47).
Conotter, V., O’Brien, J. F., & Farid, H. (2012). Exposing digital forgeries in ballistic motion. IEEE Transactions on Information Forensics and Security,7(1), 283–296.
Stamm, M. C., Lin, W. S., & Liu, K. J. (2012). Temporal forensics and anti-forensics for motion compensated video. IEEE Transactions on Information Forensics and Security,7(4), 1315–1327.
Lin, G., Chang, J., & Chuang, C. (2011). Detecting frame duplication based on spatial and temporal analyses. In Proceedings of 6th international conference on computer science & education (ICCSE) (pp. 1396–1399).
Wang, W., & Farid, H. (2007). Exposing digital forgeries in video by detecting duplication. In Proceedings of 9th workshop of multimedia and security (pp. 35–42).
Mathai, M., Rajan, D., & Emmanuel, S. (2016). Video forgery detection and localization using normalized cross-correlation of moment features. In IEEE southwest symposium on image analysis and interpretation (SSIAI) (pp. 149-152).
Shianglin, G., & Chang, J. F. (2012). Detection of frame duplication forgery in videos based on spatial and temporal analysis. International Journal of Pattern Recognition and Artificial Intelligence,26(7), 1–18.
Mathai. M., Rajan, D., & Emmanuel, S. (2016). Video forgery detection and localization using normalized cross-correlation of moment features. In Proceedings of IEEE southwest symposium on image analysis and interpretation (SSIAI) (pp. 149–152).
Tralic, D., Grgic, S., & Zovko-Cihlar, B. (2014). Video frame copy–move forgery detection based on cellular automata and local binary patterns. In 10th International symposium on telecommunications (BIHTEL) (pp. 1–4).
Amiano, L., Cozzolino, D., Poggi, G., & Verdoliva, L. (2015). Video forgery detection and localization based on 3D patchmatch. In Proceedings of IEEE international conference on multimedia & expo workshops (ICMEW) (pp. 1–6).
Bidokhti, A., & Ghaemmaghami, S. (2015). Detection of regional copy–move forgery in MPEG videos using optical flow. In Proceedings of the international symposium on artificial intelligence and signal processing (AISP) (pp. 13–17).
Bian, S., Luo, W., & Huang, J. (2014). Detecting video frame-rate up-conversion based on periodic properties of inter-frame similarity. Multimedia Tools and Applications,72(1), 437–451.
Zheng, L., Sun, T., & Shi, Y. Q. (2015). Inter-frame video forgery detection based on block-wise brightness variance descriptor. In Digital-forensics and watermarking (pp. 18–30).
Wang, W., & Farid, H. (2009). Exposing digital forgeries in video by detecting double quantization. In Proceedings of 11th ACM workshop on multimedia and security (pp. 39–48).
GRIP—Image processing research group video Dataset. (2018). Retrieved January 10, 2018 from, http://www.grip.unina.it/web-download.html.
Sundaram, M. A., & Nandini, C. (2015). CBFD: Coherence based forgery detection technique in image forensics analysis. In Proceedings of international conference on emerging research in electronics, computer science and technology (ICERECT) (pp. 192–197).
Zhong, J., et al. (2017). A new block-based method for copy move forgery detection under image geometric transforms. Multimedia Tools and Applications,76(13), 4887–14903.
Hsu, C. C., et al. (2008). Video forgery detection using correlation of noise residue. In Proceedings of IEEE 10th workshop on multimedia signal processing (pp. 170–174).
Dong, Q., Yan, G., & Zhu, N. (2011). A MCEA based passive forensics scheme for detecting frame-based video tampering. IEEE Transactions on Circuits and Systems for Video Technology,21(4), 421–434.
Ravi, H., Subramanyam, A. V., Gupta, G., & Kumar, A. B. (2014). Compression noise based video forgery detection. In Proceedings of IEEE international conference on image processing (pp. 5352–5356).
Tan, S., Chen, S., & Li, B. (2015). GOP based automatic detection of object-based forgery in advanced video. In Proceedings of Asia-pacific signal and information processing association annual summit and conference (pp. 719–722).
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Kaur, H., Jindal, N. Image and Video Forensics: A Critical Survey. Wireless Pers Commun 112, 1281–1302 (2020). https://doi.org/10.1007/s11277-020-07102-x
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-020-07102-x