Abstract
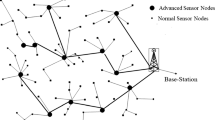
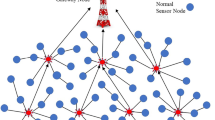
Most of recent researches carried out into wireless sensor networks are concerned with homogeneous networks in which all network nodes have the same features and key management mechanisms presented for them aim to enable as many nodes to establish shared cryptographic keys as possible. Hierarchical networks have shown a better performance because of using clustering features. This issue motivated us to present a method for key establishment in hierarchical wireless sensor networks based on symmetric cryptography. Since symmetric cryptosystems consume to have low energy, they are a good choice for sensor networks. Although symmetric cryptosystems consume to have high memory, this shortcoming can be diminished by appropriate techniques. The simulation results have shown that our proposed method can significantly reduce the memory consumption resulted from saving keys alongside reducing the energy consumption resulted from communications in all network nodes than related works while it presents a favorable level of security.







Similar content being viewed by others
References
Duarte-Melo, E. J., & Liu, M. (2003). Data-gathering wireless sensor networks: Organization and capacity. Computer Networks,43(4), 519–537. https://doi.org/10.1016/S1389-1286(03)00357-8.
Xu, K., Hong, X., & Gerla, M. (2002). An ad hoc network with mobile backbones. In 2002 IEEE international conference on communications. Conference Proceedings. ICC 2002 (Cat. No. 02CH37333) (Vol. 5, pp. 3138–3143). IEEE. https://doi.org/10.1109/ICC.2002.997415.
Daemen, J., & Rijmen, V. (2002). The Design of Rijndael, AES—The Advanced Encryption Standard (p. 238). Springer.
Rifa-Pous, H., & Herrera-Joancomartí, J. (2011). Computational and energy costs of cryptographic algorithms on handheld devices. Future internet,3(1), 31–48. https://doi.org/10.3390/fi3010031.
Mungara, R., VenkateswaraRao, K., & Pallamreddy, V. A. Routing-driven elliptic curve cryptography based key management scheme for heterogeneous sensor networks.
Yarvis, M., Kushalnagar, N., Singh, H., Rangarajan, A., Liu, Y., & Singh, S. (2005). Exploiting heterogeneity in sensor networks. In IEEE infocom (Vol. 2, p. 878). Institute of Electrical Engineers Inc (IEEE).
Girod, L., Stathopoulos, T., Ramanathan, N., Elson, J., Estrin, D., Osterweil, E., et al. (2004). A system for simulation, emulation, and deployment of heterogeneous sensor networks. In Proceedings of the 2nd international conference on Embedded networked sensor systems (pp. 201–213). ACM. https://doi.org/10.1145/1031495.1031519.
Lai, B., Kim, S., & Verbauwhede, I. (2002). Scalable session key construction protocol for wireless sensor networks. In Proceedings of the IEEE Workshop on Large Scale Real Time and Embedded Systems (LARTES), Washington, DC, USA, December 2002, p. 7.
Nemec, L., Matyas, V., Ostadal, R., Svenda, P., & Palant, P. L. (2019). Evaluating dynamic approaches to key (Re-) Establishment in wireless sensor networks. Sensors,19(4), 914.
Chan, H., Perrig, A., & Song, D. (2003). Random key predistribution schemes for sensor networks. In Proceedings of the 2003 Symposium on Security and Privacy, Berkeley, CA, USA, 11–14 May 2003, pp. 197–213.
Álvarez Bermejo, J. A., Lodroman, A., & López-Ramos, J. A. (2016). Distributed key agreement for group communications based on elliptic curves. An application to sensor networks. Mathematical Methods in the Applied Sciences,39, 4797–4809.
Parrilla, L., Castillo, E., López-Ramos, J. A., Álvarez Bermejo, J. A., García, A., & Morales, D. P. (2018). Unified compact ECC-AES co-processor with group-key support for IoT devices in wireless sensor networks. Sensors,18, 251.
Rahman, S. M. M., & El-Khatib, K. (2010). Private Key agreement and secure communication for heterogeneous sensor networks. Journal of Parallel and Distributed Computing,70(8), 858–870. https://doi.org/10.1016/j.jpdc.2010.03.009.
Azarderskhsh, R., & Reyhani-Masoleh, A. (2011). Secure clustering and symmetric key establishment in heterogeneous wireless sensor networks. EURASIP Journal on Wireless Communications and Networking,2011(1), 893592. https://doi.org/10.1155/2011/893592.
Boujelben, M., Youssef, H., Mzid, R., & Abid, M. (2011). IKM—An identity based key management scheme for heterogeneous sensor networks. JCM,6(2), 185–197.
Traynor, P., Kumar, R., Choi, H., Cao, G., Zhu, S., & La Porta, T. (2007). Efficient hybrid security mechanisms for heterogeneous sensor networks. IEEE Transactions on Mobile Computing,6(6), 663–677. https://doi.org/10.1109/TMC.2007.1020.
Koblitz, N. (1987). Elliptic curve cryptosystems. Mathematics of Computation,48(177), 203–209. https://doi.org/10.1090/S0025-5718-1987-0866109-5.
Kaur, A. (2013). Energy analysis of wireless sensor networks using rsa and ecc encryption method. International Journal of Scientific & Engineering Research,4(5), 2212.
Landstra, T., Zawodniok, M., & Jagannathan, S. (2007). Energy-efficient hybrid key management protocol for wireless sensor networks. In 32nd IEEE conference on local computer networks (LCN 2007) (pp. 1009–1016). IEEE. https://doi.org/10.1109/LCN.2007.135.
Zhang, X., He, J., & Wei, Q. (2011). EDDK: Energy-efficient distributed deterministic key management for wireless sensor networks. EURASIP Journal on Wireless Communications and Networking,2011(1), 765143. https://doi.org/10.1155/2011/765143.
Sahingoz, O. K. (2013). Large scale wireless sensor networks with multi-level dynamic key management scheme. Journal of Systems Architecture,59(9), 801–807. https://doi.org/10.1016/j.sysarc.2013.05.022.
Perrig, A., Szewczyk, R., Tygar, J. D., Wen, V., & Culler, D. E. (2002). SPINS: Security protocols for sensor networks. Wireless Networks,8(5), 521–534. https://doi.org/10.1023/A:1016598314198.
Rasheed, A., & Mahapatra, R. (2010). Key predistribution schemes for establishing pairwise keys with a mobile sink in sensor networks. IEEE Transactions on Parallel and Distributed Systems,22(1), 176–184. https://doi.org/10.1109/TPDS.2010.57.
Zhang, J., & Varadharajan, V. (2010). Wireless sensor network key management survey and taxonomy. Journal of Network and Computer Applications,33(2), 63–75. https://doi.org/10.1016/j.jnca.2009.10.001.
Fanian, A., Berenjkoub, M., Saidi, H., & Gulliver, T. A. (2010). A new key establishment protocol for limited resource wireless sensor networks. In 2010 8th annual communication networks and services research conference (pp. 138–145). IEEE. https://doi.org/10.1109/CNSR.2010.43.
Shi, Q., Zhang, N., Merabti, M., & Kifayat, K. (2013). Resource-efficient authentic key establishment in heterogeneous wireless sensor networks. Journal of Parallel and Distributed Computing,73(2), 235–249. https://doi.org/10.1016/j.jpdc.2012.10.004.
Joan, D., & Vincent, R. (2002). The design of Rijndael: AES-the advanced encryption standard. In Information Security and Cryptography. Springer.
Singh, R., Misra, R., & Kumar, V. (2013). Analysis the impact of symmetric cryptographic algorithms on power consumption for various data types. International Journal on Recent and Innovation Trends in Computing and Communication,1(4), 321–326.
Qian, S. (2012). A novel key pre-distribution for wireless sensor networks. Physics Procedia,25, 2183–2189. https://doi.org/10.1016/j.phpro.2012.03.368.
Bechkit, W., Challal, Y., & Bouabdallah, A. (2013). A new class of Hash-Chain based key pre-distribution schemes for WSN. Computer Communications,36(3), 243–255. https://doi.org/10.1016/j.comcom.2012.09.015.
Liu, D., Ning, P., & Li, R. (2005). Establishing pairwise keys in distributed sensor networks. ACM Transactions on Information and System Security (TISSEC),8(1), 41–77. https://doi.org/10.1145/1053283.1053287.
Fanian, A., Berenjkoub, M., Saidi, H., & Gulliver, T. A. (2010). A hybrid key establishment protocol for large scale wireless sensor networks. In 2010 IEEE Wireless Communication and Networking Conference (pp. 1–6). IEEE. https://doi.org/10.1109/WCNC.2010.5506121.
Du, W., Deng, J., Han, Y. S., Varshney, P. K., Katz, J., & Khalili, A. (2005). A pairwise key predistribution scheme for wireless sensor networks. ACM Transactions on Information and System Security (TISSEC),8(2), 228–258. https://doi.org/10.1145/1065545.1065548.
Zhang, Y., Xu, L., Xiang, Y., & Huang, X. (2013). A matrix-based pairwise key establishment scheme for wireless mesh networks using pre deployment knowledge. IEEE Transactions on Emerging Topics in Computing,1(2), 331–340. https://doi.org/10.1109/TETC.2013.2287196.
Sarmad, U. K., Lavagno, L., & Pastrone, C. (2010). A key management scheme supporting node mobility in heterogeneous sensor networks. In 2010 6th International Conference on Emerging Technologies (ICET) (pp. 364–369). IEEE. https://doi.org/10.1109/ICET.2010.5638458.
Moharrum, M., Eltoweissy, M., & Mukkamala, R. (2006). Dynamic combinatorial key management scheme for sensor networks. Wireless Communications and Mobile Computing,6(7), 1017–1035. https://doi.org/10.1002/wcm.435.
Lai, B., Kim, S., & Verbauwhede, I. (2002). Scalable session key construction protocol for wireless sensor networks. In IEEE Workshop on Large Scale RealTime and Embedded Systems (LARTES) (Vol. 7).
Zhu, S., Setia, S., & Jajodia, S. (2006). LEAP+: Efficient security mechanisms for large-scale distributed sensor networks. ACM Transactions on Sensor Networks (TOSN),2(4), 500–528. https://doi.org/10.1145/1218556.1218559.
Zeng, Y., Zhao, B., Su, J., Yan, X., & Shao, Z. (2007). A loop-based key management scheme for wireless sensor networks. In International conference on embedded and ubiquitous computing (pp. 103–114). Berlin, Heidelberg: Springer. https://doi.org/10.1007/978-3-540-77090-9_10.
Dutertre, B., Cheung, S., & Levy, J. (2004). Lightweight key management in wireless sensor networks by leveraging initial trust (pp. 1–18). Technical Report SRI-SDL-04-02, SRI International.
Chan, H., Gligor, V. D., Perrig, A., & Muralidharan, G. (2005). On the distribution and revocation of cryptographic keys in sensor networks. IEEE Transactions on Dependable and Secure Computing,3, 233–247. https://doi.org/10.1109/TDSC.2005.37.
Mungara, R., VenkateswaraRao, K., & Pallamreddy, V. A. (2009). Routing-driven elliptic curve cryptography based key management scheme for heterogeneous sensor networks. IEEE Transactions on Wireless Communications,8(3), 371–383.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Mirvaziri, H., Hosseini, R. A Novel Method for Key Establishment Based on Symmetric Cryptography in Hierarchical Wireless Sensor Networks. Wireless Pers Commun 112, 2373–2391 (2020). https://doi.org/10.1007/s11277-020-07155-y
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-020-07155-y