Abstract
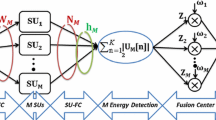
In Cognitive Radio Network, access to the vacant spectrum holes in the licensed Primary User (PU) channel is allowed to the Secondary Users. In order to use the PU spectral holes accurately and on time, spectrum sensing is extremely important to avoid interference with the PU transmission. In Cooperative Spectrum Sensing (CSS) individual users report the Fusion Center (FC) about sensing data for a global decision which leads to better sensing results as compared to non-cooperative sensing. The objective of this paper is to make the CSS performance precise and accurate in the presence of Malicious Users (MUs) reporting false sensing information to the FC. The proposed scheme reduces falsifying effects of the YES, NO and OPPOSITE categories of MUs in CSS using Differential Evolution (DE) algorithm. A dynamic threshold value is determined using optimum coefficient vector by the DE at the FC. This leads to minimum error probability in detecting PU channel when the YES, NO and OPPOSITE categories of MUs reports FC in CSS. The weighting coefficient vector is further employed at the FC to assign weights to the received sensing information of cooperative users. Therefore, cooperative users with minutely erroneous reports receive high weight as compared to MUs. The simulations performed for varying number of MUs, total cooperative users, Signal to Noise Ratios and sensing samples show minimum error in detecting PU activity for the proposed DE technique in comparison with the Kullback–Leibler divergence, particle swarm optimization, Genetic Algorithm and Maximum Gain Combination schemes.

















Similar content being viewed by others
References
Haykin, S. (2005). Cognitive radio: Brain-empowered wireless communications. IEEE Journal on Selected Areas in Communications, 23(2), 201–220.
Ghasemi, A., & Sousa, E. S. (2008). Spectrum sensing in cognitive radio networks: Requirements, challenges and design trade-offs. Communications Magazine, IEEE, 46(4), 32–39.
Giupponi, L., Galindo-Serrano, A., Blasco, P., & Dohler, M. (2010). Docitive networks: An emerging paradigm for dynamic spectrum management [dynamic spectrum management]. IEEE Wireless Commun., 17(4), 47–54.
Cabric, D., Mishra, S. M., & Brodersen, R. W. (2004). Implementation issues in spectrum sensing for cognitive radios. In Conference record of the thirty-eighth asilomar conference on signals, systems and computers, 2004 (Vol. 1, pp. 772–776).
Tandra, R., & Sahai, A. (2005). Fundamental limits on detection in low SNR under noise uncertainty. In 2005 international conference on wireless networks, communications and mobile computing (Vol. 1, pp. 464–469).
Hiep, K. V.-V. (2012). A robust cooperative spectrum sensing based on Kullback-Leibler divergence. IEICE Transactions on Communications, E95–B(4), 1286–1290.
Sharifi, A. A., & Niya, J. M. (2016). Securing collaborative spectrum sensing against malicious attackers in cognitive radio networks. Wireless Personal Communications, 90(1), 75–91.
Mehboob, U., Qadir, J., Ali, S., & Vasilakos, A. (2016). Genetic algorithms in wireless networking: Techniques, applications, and issues. Berlin: Springer.
Bhattacharjee, S. (2015). Optimization of probability of false alarm and probability of detection in cognitive radio networks using GA. In Proceedings of ReTIS’15—2nd IEEE international conference on recent trends in information systems, Kolkata, India. https://doi.org/10.1109/retis.2015.7232852.
Akbari, M., & Ghanbarisabagh, M. (2014). A novel evolutionary-based cooperative spectrum sensing mechanism for cognitive radio networks. Wireless Personal Communications, 79(2), 1017–1030. https://doi.org/10.1007/s11277-014-1915-8.
Fathy, M., Tammam, A., & Saafan, A. (2019). Influence of relaying malicious node within cooperative sensing in cognitive radio network. Wireless Network, 5, 2449–2458.
Sharifi, A. A., Sharifi, M., & MuseviNiya, M. J. (2016). Collaborative spectrum sensing under primary user emulation attack in cognitive radio networks. IETE Journal of Research, 62(2), 205–211.
Abrardo, A., Barni, M. Kallas, K., & Tondi, B. (2018). Decision fusion with unbalanced priors under synchronized byzantine attacks : A message-passing approach. In 2018 Asia-Pacific signal and information processing association annual summit and conference (APSIPA ASC) (pp. 1160–1167).
Gupta, N., Dhurandher, S. K., Member, S., & Sehgal, A. (2019). A contract theory approach-based scheme to encourage secondary users for cooperative sensing in cognitive radio networks. IEEE Systems Journal 1–11.
Cao, X., Lai, L., & Member, S. (2019). Distributed gradient descent algorithm robust to an arbitrary number of byzantine attackers. IEEE Transactions on Signal Processing, 67(22), 5850–5864.
Zhang, L., Ding, G., & Member, S. (2019). Detecting abnormal power emission for orderly spectrum usage B. generalized likelihood ratio detector with unknown. IEEE Transactions on Vehicular Technology, 68(2), 1989–1992.
Lee, S., Zhang, Y., Yoon, S., & Song, I. (2019). Order statistics and recursive updating with aging factor for cooperative cognitive radio networks under SSDF attacks. ICT Express, 2019, 1–4.
Sun, Z., Xu, Z., Hammad, M. Z., Ning, X., Wang, Q., & Guo, L. (2019). Defending against massive SSDF attacks from a novel perspective of honest secondary users. IEEE Communications Letters, 23(10), 1696–1699.
Grissa, M., Member, S., & Yavuz, A. A. (2017). Preserving the location privacy of secondary users in cooperative spectrum sensing. IEEE Transactions on Information Forensics and Security, 12(2), 418–431.
Grissa, M., Yavuz, A., & Hamdaoui, B. (2016). An efficient technique for protecting location privacy of cooperative spectrum sensing users. In 2016 IEEE conference on computer communications workshops (INFOCOM WKSHPS) (pp. 915–920).
Du, H., Fu, S., & Chu, H. (2015). A credibility-based defense SSDF attacks scheme for the expulsion of malicious users in cognitive radio. International Journal of hybrid information Technology, 8(9), 269–280.
Sharifi, A. A. (2019). An effective and optimal fusion rule in the presence of probabilistic spectrum sensing data falsification attack. Journal of Communication Engineering, 8(1), 78–92.
Chen, H., Zhou, M., Xie, L., & Li, J. (2017). Cooperative spectrum sensing with M-ary quantized data in cognitive radio networks under SSDF attacks. IEEE Transactions on Wireless Communications, 16(8), 5244–5257.
Feng, J., Zhang, M., Xiao, Y., & Yue, H. (2018). Securing cooperative spectrum sensing against collusive SSDF attack using XOR distance analysis in cognitive radio networks. Sensors (Switzerland), 18(2), 1–14.
Feng, J., Li, S., Lv, S., Wang, H., & Fu, A. (2018). Securing cooperative spectrum sensing against collusive false feedback attack in cognitive radio networks. IEEE Transactions on Vehicular Technology, 67(9), 8276–8287.
Fu, Y., & He, Z. (2019). Bayesian-inference-based sliding window trust model against probabilistic SSDF attack. IEEE Systems Journal, 12, 1–12.
Shrivastava, S., John, S., Rajesh, A., & Bora, P. K. (2018). Preventing collusion attacks in cooperative spectrum sensing. In International conference on signal processing and communications (SPCOM) (pp. 90–94).
Zhao, F., Li, S., & Feng, J. (2019). Securing cooperative spectrum sensing against DC-SSDF attack using trust fluctuation clustering analysis in cognitive radio networks. Wireless Communications and Mobile Computing, 2019, 1–11.
Wan, R., Ding, L., Xiong, N., & Zhou, X. (2019). Mitigation strategy against spectrum- sensing data falsification attack in cognitive radio sensor networks. International Journal of Distributed Sensor Networks, 15(9), 1–12.
Luo, Z., Zhao, S., Lu, Z., Xu, J., & Sagduyu, Y. E. (2019). When attackers meet AI : Learning-empowered attacks in cooperative spectrum sensing. 1–15.
Gul, N., Qureshi, I. M., Omar, A., Elahi, A., & Khan, M. S. (2017). History based forward and feedback mechanism in cooperative spectrum sensing including malicious users in cognitive radio network. PLoS ONE, 12(8), e0183387.
Gul, N., Qureshi, I. M., Akbar, S., Kamran, M., & Rasool, I. (2018). One-to-many relationship based kullbackLeibler divergence against malicious users in cooperative spectrum sensing. Wireless Communications and Mobile Computing, 2018, 1–14.
Gul, N., Qureshi, I. M., Elahi, A., & Rasool, I. (2018). Defense against malicious users in cooperative spectrum sensing using genetic algorithm. International Journal of Antennas and Propagation, 2018, 1–11.
Gul, N., Naveed, A., Elahi, A., Khattak, T., & Qureshi, I. (2017). A combination of double sided neighbor distance and genetic algorithm in cooperative spectrum sensing against malicious users. In Proceedings of 2017 14th international bhurban conference on applied sciences & technology (IBCAST) (pp. 746–753).
Gul, N., Mansoor, I., Aqdas, Q., Atif, N., & Imtiaz, E. (2019). Secured soft combination schemes against malicious—users in cooperative spectrum sensing. Wireless Personal Communications, 0123456789, 1–20.
Akbari, M., Manesh, M. R., Saleh, A. A., & Ismail, M. (2012). Improved soft fusion based cooperative spectrum sensing using particle swarm optimization. IEICE Electronics Express, 9(6), 436–442.
Quan, Z., Cui, S., & Sayed, A. H. (2008). Optimal linear cooperation for spectrum sensing in cognitive radio network. IEEE Journal of Selected Topics in Signal Processing, 2, 28–40m.
Zainab, A., & Sinha, P. (2016). A survey of cognitive radio reconfigurable antenna design and proposed design using genetic algorithm. In IEEE students’ conference on electrical, electronics and computer science, Bhopal, India (p. 1–6). https://doi.org/10.1109/sceecs.2016.7509263.
Karaboga, D., & Okdem, S. (2004). A simple and global optimization algorithm for engineering problems: differential evolution algorithm. Turkish Journal of Electrical Engineering & Computer Sciences, 12(1), 53–60.
Veterstrom, J., & Thomsen, R. (2004). A comparative study of differential evolution, particle swarm optimization, and evolutionary algorithms on problems. In IEEE congress on evolutionary computation (pp. 980–987).
Storn, R., & Price, K. V. (1995). Differential evolution: A simple and efficient adaptive scheme for global optimization over continuous spaces. ICSI, USA, Tech. Rep. TR-95-012, 1995 [Online]. Available: http://icsi.berkeley.edu/∼storn/litera.html.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Gul, N., Qureshi, I.M., Khan, M.S. et al. Differential Evolution Based Reliable Cooperative Spectrum Sensing in the Presence of Malicious Users. Wireless Pers Commun 114, 123–147 (2020). https://doi.org/10.1007/s11277-020-07354-7
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-020-07354-7