Abstract
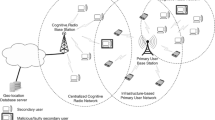
Cognitive radio (CR) is a flexible wireless network that can solve the scarcity and underutilization problem of the spectrum by permitting unlicensed users to access licensed bands. The dynamic nature of CR makes it more vulnerable in terms of security. This paper’s emphasis is on the primary user emulation attack, which poses a severe threat to the spectrum sensing operation of CR. In this attack, a malicious user imitates the signal characteristics of a licensed user (primary user) to disguise its true identity. Although many survey papers enhance our knowledge of cognitive radio security, this paper is an attempt to culminate new findings with the old ones to keep up the pace of the research community. Finally, the paper summarizes with some recommendations and future strategies pertinent to energy-efficient and flexible security methods for next-generation wireless systems.


Similar content being viewed by others
References
Marcus, M., Burtle, J., Franca, B., Lahjouji, A., & McNeil, N. (2002). Federal communications commission spectrum policy task force. Report of the unlicensed devices and experimental licenses working group.
Čabrić, D., Mishra, S. M., Willkomm, D., Brodersen, R., & Wolisz, A. (2005). A cognitive radio approach for usage of virtual unlicensed spectrum. In 14th IST mobile and wireless communications summit.
Fcc, E. (2003). Docket No 03-222 Notice of proposed rulemaking and order.
Haykin, S. (2005). Cognitive radio: Brain-empowered wireless communications. IEEE Journal on Selected Areas in Communications, 23(2), 201–220.
Thalia, N., Ingle, A., Raut, K., & Tilak, M. (2015). Cognitive radio network—A new paradigm in wireless communication. International Journal of Computer Applications, 975, 8887.
Akyildiz, I. F., Lee, W. Y., Vuran, M. C., & Mohanty, S. (2006). NeXt generation/dynamic spectrum access/cognitive radio wireless networks: A survey. Computer Networks, 50(13), 2127–2159.
Fragkiadakis, A. G., Tragos, E. Z., & Askoxylakis, I. G. (2012). A survey on security threats and detection techniques in cognitive radio networks. IEEE Communications Surveys and Tutorials, 15(1), 428–445.
Sharma, R. K., & Rawat, D. B. (2014). Advances on security threats and countermeasures for cognitive radio networks: A survey. IEEE Communications Surveys and Tutorials, 17(2), 1023–1043.
Mishra, N., Srivastava, S., & Sharan, S. N. (2019). Cognitive radio network security threats: A review. In 2019 2nd international conference on intelligent communication and computational techniques (ICCT) (pp. 333–338).
Manesh, M. R., & Kaabouch, N. (2018). Security threats and countermeasures of MAC layer in cognitive radio networks. Ad Hoc Networks, 70, 85–102.
Thalia, N., Ingle, A., Raut, K., & Tilak, M. (2016). A survey on security issues and primary user emulation attack detection techniques in cognitive radio network. International Journal of Computer Applications, 975, 8887.
Chen, R., & Park, J. M. (2006). Ensuring trustworthy spectrum sensing in cognitive radio networks. In 1st IEEE workshop on networking technologies for software defined radio networks (pp. 110–119).
Chen, R., Park, J. M., & Reed, J. H. (2008). Defense against primary user emulation attacks in cognitive radio networks. IEEE Journal on Selected Areas in Communications, 26(1), 25–37.
Rehman, S. U., Sowerby, K. W., & Coghill, C. (2014). Radio-frequency fingerprinting for mitigating primary user emulation attack in low-end cognitive radios. IET Communications, 8(8), 1274–1284.
Bouabdellah, M., Ghribi, E., & Kaabouch, N. (2019). RSS-based localization with maximum likelihood estimation for PUE attacker detection in cognitive radio networks. In IEEE international conference on electro information technology (EIT) (pp. 1–6).
Zhao, C., Xie, L., Jiang, X., Huang, L., & Yao, Y. (2010). A PHY-layer authentication approach for transmitter identification in cognitive radio networks. In International conference on communications and mobile computing (Vol. 2, pp. 154–158).
León, O., Hernández-Serrano, J., & Soriano, M. (2012). Cooperative detection of primary user emulation attacks in CRNs. Computer Networks, 56(14), 3374–3384.
Wei, J., & Zhang, X. (2010). Two-tier optimal-cooperation based secure distributed spectrum sensing for wireless cognitive radio networks. In INFOCOM IEEE conference on computer communications workshops, San Diego, CA (pp. 1–6).
Adebo, S. A., Onwuka, E. N., Usman, A. U., & Onumanyi, A. J. (2019). A hybrid localization scheme for detection of primary user emulator in cognitive radio networks. International Journal of Computing and Digital Systems, 8(03), 217–227.
Fassi Fihri, W., El Ghazi, H., Abou El Majd, B., & El Bouanani, F. (2019). A decision-making approach for detecting the primary user emulation attack in cognitive radio networks. International Journal of Communication Systems, 32(15), e4026.
Arun, S., & Umamaheswari, G. (2020). An adaptive learning-based attack detection technique for mitigating primary user emulation in cognitive radio networks. Circuits, Systems, and Signal Processing, 39(2), 1071–1088.
El Mrabet, Z., Arjoune, Y., El Ghazi, H., Abou Al Majd, B., & Kaabouch, N. (2018). Primary user emulation attacks: A detection technique based on Kalman filter. Journal of Sensor and Actuator Networks, 7(3), 26.
Selvapriya, T., Sharmila, S. S. S., Sindhuja, M., Sinthuja, V., & Jayasri, C. (2017). A database assisted detection against primary user emulation in cognitive radio network. International Journal of Innovative Research in Electrical, Electronics, Instrumentation and Control Engineering, 5(3), 1–6.
Liu, Z., Zhang, G., Meng, W., Ma, X., & Li, G. (2020). Multiple-phase energy detection and effective capacity based resource allocation against primary user emulation attacks in cognitive radio networks. KSII Transactions on Internet and Information Systems. https://doi.org/10.3837/tiis.2020.03.022.
Muñoz, E. C., Rodriguez-Colina, E., Pedraza, L. F., & Paez, I. P. (2020). Detection of dynamic location primary user emulation on mobile cognitive radio networks using USRP. EURASIP Journal on Wireless Communications and Networking, 2020(1), 1–19.
Anand, S., Jin, Z., & Subbalakshmi, K. P. (2008). An analytical model for primary user emulation attacks in cognitive radio networks. In 3rd IEEE symposium on new frontiers in dynamic spectrum access networks (pp. 1–6).
Jin, Z., Anand, S., & Subbalakshmi, K. P. (2009). Detecting primary user emulation attacks in dynamic spectrum access networks. In IEEE international conference on communications (pp. 1–5).
Jin, Z., Anand, S., & Subbalakshmi, K. P. (2009). Mitigating primary user emulation attacks in dynamic spectrum access networks using hypothesis testing. ACM SIGMOBILE Mobile Computing and Communications Review, 13(2), 74–85.
Chen, Z., Cooklev, T., Chen, C., & Pomalaza-Ráez, C. (2009). Modeling primary user emulation attacks and defenses in cognitive radio networks. In IEEE 28th international performance computing and communications conference (pp. 208–215).
Liu, Y., Ning, P., & Dai, H. (2010). Authenticating primary users’ signals in cognitive radio networks via integrated cryptographic and wireless link signatures. In IEEE symposium on security and privacy (pp. 286–301).
Jayapalan, A., Savarinathan, P., Praveenkumar, P., & Karuppasamy, T. (2019). Detecting and mitigating selfish primary users in cognitive radio. Wireless Personal Communications, 109(2), 1021–1031.
Mathur, C. N., & Subbalakshmi, K. P. (2007). Digital signatures for centralized DSA networks. In 4th IEEE consumer communications and networking conference (pp. 1037–1041).
Ghanem, W. R., Shokair, M., & Desouky, M. I. (2016). Defense against selfish PUEA in cognitive radio networks based on hash message authentication code. International Journal of Electronics and Information Engineering, 4(1), 12–21.
Alahmadi, A., Abdelhakim, M., Ren, J., & Li, T. (2014). Defense against primary user emulation attacks in cognitive radio networks using advanced encryption standard. IEEE Transactions on Information Forensics and Security, 9(5), 772–781.
Yuan, Z., Niyato, D., Li, H., Song, J. B., & Han, Z. (2012). Defeating primary user emulation attacks using belief propagation in cognitive radio networks. IEEE Journal on Selected Areas in Communications, 30(10), 1850–1860.
Maric, S., Reisenfeld, S., & Goratti, L. (2016). A single iteration belief propagation algorithm to minimize the effects of primary user emulation attacks. In International symposium on intelligent signal processing and communication systems (ISPACS) (pp. 1–6). IEEE.
Chen, S., Zeng, K., & Mohapatra, P. (2011). Hearing is believing: detecting wireless microphone emulation attacks in white space. IEEE Transactions on Mobile Computing, 12(3), 401–411.
Bishnu, A., & Bhatia, V. (2019). Cognitive radio networks: IEEE 802.22 standards. In Sensing techniques for next generation cognitive radio networks (pp. 27–50). IGI Global.
Stevenson, C. R., Chouinard, G., Lei, Z., Hu, W., Shellhammer, S. J., & Caldwell, W. (2009). IEEE 802.22: The first cognitive radio wireless regional area network standard. IEEE Communications Magazine, 47(1), 130–138.
Wang, B., Wu, Y., & Liu, K. R. (2010). Game theory for cognitive radio networks: An overview. Computer Networks, 54(14), 2537–2561.
Maharjan, S., Zhang, Y., & Gjessing, S. (2011). Economic approaches for cognitive radio networks: A survey. Wireless Personal Communications, 57(1), 33–51.
Rawat, D. B., Bajracharya, C., & Yan, G. (2011). Game theory for resource allocation in wireless networks. In Emerging technologies in wireless ad hoc networks: Applications and future development (pp. 335–352). IGI Global.
Manshaei, M. H., Zhu, Q., Alpcan, T., Bacşar, T., & Hubaux, J. P. (2013). Game theory meets network security and privacy. ACM Computing Surveys (CSUR), 45(3), 1–39.
Tan, Y., Sengupta, S., & Subbalakshmi, K. P. (2012). Primary user emulation attack in dynamic spectrum access networks: A game-theoretic approach. IET Communications, 6(8), 964–973.
Nguyen-Thanh, N., Ciblat, P., Pham, A. T., & Nguyen, V. T. (2015). Surveillance strategies against primary user emulation attack in cognitive radio networks. IEEE Transactions on Wireless Communications, 14(9), 4981–4993.
Ta, D. T., Nguyen-Thanh, N., Maille, P., Ciblat, P., & Nguyen, V. T. (2016). Mitigating primary emulation attacks in multi-channel cognitive radio networks: A surveillance game. In 2016 IEEE global communications conference (GLOBECOM) (pp. 1–6). IEEE.
Ta, D. T., Nguyen-Thanh, N., Maillé, P., & Nguyen, V. T. (2018). Strategic surveillance against primary user emulation attacks in cognitive radio networks. IEEE Transactions on Cognitive Communications and Networking, 4(3), 582–596.
Mahmoudi, M., Faez, K., & Ghasemi, A. (2019). Uncoordinated frequency hopping scheme for defense against primary user emulation attack in cognitive radio networks. Computer Networks, 163, 106884.
Yazdi, S. A. V., & Ghazvini, M. (2019). Countermeasure with primary user emulation attack in cognitive radio networks. Wireless Personal Communications, 108(4), 2261–2277.
Clancy, C., Hecker, J., Stuntebeck, E., & O’Shea, T. (2007). Applications of machine learning to cognitive radio networks. IEEE Wireless Communications, 14(4), 47–52.
Bkassiny, M., Li, Y., & Jayaweera, S. K. (2012). A survey on machine-learning techniques in cognitive radios. IEEE Communications Surveys and Tutorials, 15(3), 1136–1159.
Wang, J., Jiang, C., Zhang, H., Ren, Y., Chen, K. C., & Hanzo, L. (2020). Thirty years of machine learning: The road to pareto-optimal wireless networks. IEEE Communications Surveys and Tutorials.
Hossain, M. A., Noor, R. M., Yau, K. L. A., Azzuhri, S. R., Z’aba, M. R., & Ahmedy, I. (2020). Comprehensive survey of machine learning approaches in cognitive radio-based vehicular ad hoc networks. IEEE Access.
Bhatti, D. M. S., Ahmed, S., Chan, A. S., & Saleem, K. (2020). Clustering formation in cognitive radio networks using machine learning. AEU-International Journal of Electronics and Communications, 114, 152994.
Li, Y., & Peng, Q. (2016). Achieving secure spectrum sensing in presence of malicious attacks utilizing unsupervised machine learning. In MILCOM IEEE military communications conference (pp. 174–179).
Blesa, J., Romero, E., Rozas, A., & Araujo, A. (2013). PUE attack detection in CWSNs using anomaly detection techniques. EURASIP Journal on Wireless Communications and Networking, 2013(1), 215.
Dong, Q., Chen, Y., Li, X., & Zeng, K. (2018). Explore recurrent neural network for PUE attack detection in practical CRN models. In IEEE international smart cities conference (ISC2) (pp. 1–9).
López, D., Rivas, E., & Gualdron, O. (2019). Primary user characterization for cognitive radio wireless networks using a neural system based on deep learning. Artificial Intelligence Review, 1–27.
Albehadili, A., Ali, A., Jahan, F., Javaid, A. Y., Oluochy, J., & Devabhaktuniz, V. (2019). Machine learning-based primary user emulation attack detection in cognitive radio networks using pattern described link-signature (PDLS). In Wireless telecommunications symposium (WTS) (pp. 1–7).
Elghamrawy, S. M. (2018). Security in cognitive radio network: Defense against primary user emulation attacks using genetic artificial bee colony (GABC) algorithm. Future Generation Computer Systems. https://doi.org/10.1016/j.future.2018.08.022.
Kumar, A., Kumar, D., & Jarial, S. (2018). A novel hybrid K-means and artificial bee colony algorithm approach for data clustering. Decision Science Letters, 7(1), 65–76.
Mirza, M. A., Ahmad, M., Habib, M. A., Mahmood, N., Faisal, C. N., & Ahmad, U. (2018). CDCSS: Cluster-based distributed cooperative spectrum sensing model against primary user emulation (PUE) cyber-attacks. The Journal of Supercomputing, 74(10), 5082–5098.
Han, X., Xue, L., Shao, F., & Xu, Y. (2020). A power spectrum maps estimation algorithm based on generative adversarial networks for underlay cognitive radio networks. Sensors, 20(1), 311.
Shi, Y., Sagduyu, Y. E., Erpek, T., Davaslioglu, K., Lu, Z., & Li, J. H. (2018). Adversarial deep learning for cognitive radio security: Jamming attack and defense strategies. In 2018 IEEE international conference on communications workshops (ICC Workshops) (pp. 1–6). IEEE.
Roy, D., Mukherjee, T., Chatterjee, M., & Pasiliao, E. (2019). Defense against PUE attacks in DSA networks using GAN based learning. In IEEE global communications conference (GLOBECOM) (pp. 1–6).
Roy, D., Mukherjee, T., Chatterjee, M., & Pasiliao, E. (2019). Detection of rogue RF transmitters using generative adversarial nets. In IEEE wireless communications and networking conference (WCNC) (pp. 1–7).
Toma, A., Krayani, A., Farrukh, M., Qi, H., Marcenaro, L., Gao, Y., et al. (2020). AI-based abnormality detection at the phy-layer of cognitive radio by learning generative models. IEEE Transactions on Cognitive Communications and Networking, 6(1), 21–34.
Liao, X., Si, J., Shi, J., Li, Z., & Ding, H. (2020). Generative adversarial network assisted power allocation for cooperative cognitive covert communication system. IEEE Communications Letters. https://doi.org/10.1109/LCOMM.2020.2988384.
Srinivasan, S., Shivakumar, K. B., & Mohammad, M. (2019). Semi-supervised machine learning for primary user emulation attack detection and prevention through core-based analytics for cognitive radio networks. International Journal of Distributed Sensor Networks, 15(9), 1550147719860365.
Srinivasan, S., & Shivakumar, K. B. (2018). AI based algorithm and framework for efficient PUE attack detection using dual classification method in CRN. International Journal of Applied Engineering Research, 13(4), 52–56.
Ling, M. H., & Yau, K. L. A. (2019). Can Reinforcement learning address security issues? An investigation into a clustering scheme in distributed cognitive radio networks. In 2019 International conference on information networking (ICOIN) (pp. 296–300).
Raj, R. N., Nayak, A., & Kumar, M. S. (2020). A survey and performance evaluation of reinforcement learning based spectrum aware routing in cognitive radio ad hoc networks. International Journal of Wireless Information Networks, 27(1), 144–163.
Ling, M. H., Yau, K. L. A., Qadir, J., Poh, G. S., & Ni, Q. (2015). Application of reinforcement learning for security enhancement in cognitive radio networks. Applied Soft Computing, 37, 809–829.
Manohar, A. L., Yau, K. L. A., Ling, M. H., & Khan, S. (2018). A security-enhanced cluster size adjustment scheme for cognitive radio networks. IEEE Access, 7, 117–130.
Saleem, Y., Yau, K. L. A., Mohamad, H., Ramli, N., Rehmani, M. H., & Ni, Q. (2017). Clustering and reinforcement-learning-based routing for cognitive radio networks. IEEE Wireless Communications, 24(4), 146–151.
Ling, M. H., Yau, K. L. A., Qadir, J., & Ni, Q. (2018). A reinforcement learning-based trust model for cluster size adjustment scheme in distributed cognitive radio networks. IEEE Transactions on Cognitive Communications and Networking, 5(1), 28–43.
Syed, A. R., Yau, K. L. A., Qadir, J., Mohamad, H., Ramli, N., & Keoh, S. L. (2016). Route selection for multi-hop cognitive radio networks using reinforcement learning: An experimental study. IEEE Access, 4, 6304–6324.
Musavi, M., Yau, K. L. A., Syed, A. R., Mohamad, H., & Ramli, N. (2018). Route selection over clustered cognitive radio networks: An experimental evaluation. Computer Communications, 129, 138–151.
Ren, Y., Dmochowski, P., & Komisarczuk, P. (2010). Analysis and implementation of reinforcement learning on a GNU radio cognitive radio platform. In Proceedings of the fifth international conference on cognitive radio oriented wireless networks and communications (pp. 1–6).
Joshi, A. P., Han, M., & Wang, Y. (2018). A survey on security and privacy issues of blockchain technology. Mathematical Foundations of Computing, 1(2), 121–147.
Sajid, A., Khalid, B., Ali, M., Mumtaz, S., Masud, U., & Qamar, F. (2020). Securing cognitive radio networks using blockchains. Future Generation Computer Systems. https://doi.org/10.1016/j.future.2020.03.020.
Kotobi, K., & Bilen, S. G. (2018). Secure blockchains for dynamic spectrum access: A decentralized database in moving cognitive radio networks enhances security and user access. IEEE Vehicular Technology Magazine, 13(1), 32–39.
Weiss, M. B., Werbach, K., Sicker, D. C., & Bastidas, C. E. C. (2019). On the application of blockchains to spectrum management. IEEE Transactions on Cognitive Communications and Networking, 5(2), 193–205.
Patnaik, M., Prabhu, G., Rebeiro, C., Matyas, V., & Veezhinathan, K. (2020). ProBLeSS: A proactive blockchain based spectrum sharing protocol against SSDF attacks in cognitive radio IoBT networks. IEEE Networking Letters. https://doi.org/10.1109/LNET.2020.2976977.
Le, T. N., Chin, W. L., & Kao, W. C. (2015). Cross-layer design for primary user emulation attacks detection in mobile cognitive radio networks. IEEE Communications Letters, 19(5), 799–802.
Hamamreh, J. M., & Arslan, H. (2018). Joint PHY/MAC layer security design using ARQ with MRC and null-space independent PAPR-aware artificial noise in SISO systems. IEEE Transactions on Wireless Communications, 17(9), 6190–6204.
Chen, P., Ouyang, J., Zhu, W. P., Lin, M., El Shafie, A., & Al-Dhahir, N. (2020). Artificial-noise-aided energy-efficient secure beamforming for multi-eavesdroppers in cognitive radio networks. IEEE Systems Journal. https://doi.org/10.1109/JSAC.2018.2824622.
Yu, Y. C., Hu, L., Li, H. T., Zhang, Y. M., Wu, F. M., & Chu, J. F. (2014). The security of physical layer in cognitive radio networks. Journal of Communications, 9(12), 28–33.
Sharma, S., Roy, S. D., & Kundu, S. (2020). Physical layer security in cognitive cooperative radio network with energy harvesting DF relay assisted with cooperative jamming. In Proceedings of the 2nd international conference on communication, devices and computing (pp. 119–129). Springer, Singapore.
Salahdine, F., & Kaabouch, N. (2020). Security threats, detection, and countermeasures for physical layer in cognitive radio networks: A survey. Physical Communication, 101001.
Pahuja, S., & Jindal, P. (2019). Cooperative communication in physical layer security: Technologies and challenges. Wireless Personal Communications, 108(2), 811–837.
Chandran, T. A., Pal, R., Prakash, A., & Tripathi, R. (2020). Proactive spectrum handoff-based MAC protocol for cognitive radio ad hoc network. In Advances in VLSI, communication, and signal processing (pp. 91–101). Springer, Singapore.
Patnaik, M., Kamakoti, V., Matyáš, V., & Řchák, V. (2019). PROLEMus: A proactive learning-based MAC protocol against PUEA and SSDF attacks in energy constrained cognitive radio networks. IEEE Transactions on Cognitive Communications and Networking, 5(2), 400–412.
Narayanan, N. S., Patnaik, M., & Kamakoti, V. (2016). ProMAC: A proactive model predictive control based MAC protocol for cognitive radio vehicular networks. Computer Communications, 93, 27–38.
Kwon, S., Kim, B., & Roh, B. H. (2014). Preemptive opportunistic MAC protocol in distributed cognitive radio networks. IEEE Communications Letters, 18(7), 1155–1158.
Halima, N. B., & Boujemâa, H. (2020). Energy harvesting for cooperative cognitive radio networks. Wireless Personal Communications. https://doi.org/10.1007/s11277-020-07058-y.
Ku, M. L., Li, W., Chen, Y., & Liu, K. R. (2015). Advances in energy harvesting communications: Past, present, and future challenges. IEEE Communications Surveys and Tutorials, 18(2), 1384–1412.
Liu, Y., Mousavifar, S. A., Deng, Y., Leung, C., & Elkashlan, M. (2015). Wireless energy harvesting in a cognitive relay network. IEEE Transactions on Wireless Communications, 15(4), 2498–2508.
Ni, L., Da, X., Hu, H., Huang, Y., Xu, R., & Zhang, M. (2018). Outage constrained robust transmit design for secure cognitive radio with practical energy harvesting. IEEE Access, 6, 71444–71454.
He, H., & Jiang, H. (2019). Deep learning based energy efficiency optimization for distributed cooperative spectrum sensing. IEEE Wireless Communications, 26(3), 32–39.
Kwasinski, A., Wang, W., & Mohammadi, F. S. (2020). Reinforcement learning for resource allocation in cognitive radio networks. Machine Learning for Future Wireless Communications. https://doi.org/10.1002/9781119562306.ch2.
Dai, Y., Xu, D., Maharjan, S., Chen, Z., He, Q., & Zhang, Y. (2019). Blockchain and deep reinforcement learning empowered intelligent 5G beyond. IEEE Network, 33(3), 10–17.
Luong, N. C., Anh, T. T., Binh, H. T. T., Niyato, D., Kim, D. I., & Liang, Y. C. (2019). Joint transaction transmission and channel selection in cognitive radio based blockchain networks: A deep reinforcement learning approach. In ICASSP 2019-2019 IEEE international conference on acoustics, speech and signal processing (ICASSP) (pp. 8409–8413). IEEE.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Mishra, N., Srivastava, S. & Sharan, S.N. Countermeasures for Primary User Emulation Attack: A Comprehensive Review. Wireless Pers Commun 115, 827–858 (2020). https://doi.org/10.1007/s11277-020-07600-y
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-020-07600-y