Abstract
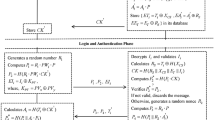
Smart cities or Smart societies require Internet of Things (IoT), for connecting numerous devices to enormous asset pools in cloud computing. This coordination of embedded tools plus cloud servers conveys the extensive applicability of IoT in Smart Cities. However, authentication and data protection, play a major job in secure coordination of these two technologies. Considering this, in 2017, Chang et al.s system introduced famous verification system dependent on an elliptic curve cryptography (ECC) for IoT plus cloud servers for Smart Cities and guaranteed that it fulfills need of security protocols and is safe to different sorts of assaults. Nevertheless, in this paper, we demonstrate that Chang et.al. system is defenseless to a privileged insider intrusion, server impersonation intrusion, known session-specific information intrusion and offline password guessing intrusion. In addition, it does not accomplish device anonymity and mutual authentication. Considering this weakness of existing system, we propose an authentication system dependent on ECC for IoT and cloud servers in Smart Cities. The suggested system accomplishes mutual authentication and supports fundamental safety necessities. The informal security examination, performance analysis and contrast of the suggested system with existing systems prove that the suggested method is powerful, effective and stout as a counter to manifold security threats faced by Smart Cities. The formal confirmation of the suggested procedure is performed by AVISPA tools, which affirms its safety strength within the sight of a conceivable invader.









Similar content being viewed by others
References
Liu, J., Ren, A., Zhang, L., Sun, R., Du, X. & Guizani, M. (2019). A Novel Secure Authentication Scheme for Heterogeneous Internet of Things, in: ICC 2019-2019 IEEE International Conference on Communications (ICC), Organization, IEEE, pp. 1–6.
Amin, R., Kumar, N., Biswas, G., Iqbal, R., & Chang, V. (2018). A light weight authentication protocol for IoT-enabled devices in distributed Cloud Computing environment. Elsevier, 78, 1005–1019.
Roy, S., Chatterjee, S., Das, A. K., Chattopadhyay, S., Kumari, S., & Jo, M. (2017). Chaotic map-based anonymous user authentication scheme with user biometrics and fuzzy extractor for crowdsourcing Internet of Things. IEEE Internet of Things Journal, 5(4), 2884–2895.
Yang, Y., Wu, L., Yin, G., Li, L., & Zhao, H. (2017). A survey on security and privacy issues in internet-of-things. IEEE Internet of Things Journal, 4(5), 1250–1258.
Mahmood, Z., Ning, H., Ullah, A., & Yao, X. (2017). Secure authentication and prescription safety protocol for telecare health services using ubiquitous IoT. Applied Sciences, 7(10), 1069.
Yao, X., Chen, Z., & Tian, Y. (2015). A lightweight attribute-based encryption scheme for the Internet of Things. Future Generation Computer Systems, 49, 104–112.
Moosavi, S. R., Nigussie, E., Virtanen, S. & Isoaho, J. (2014). An Elliptic Curve-based Mutual Authentication Scheme for RFID Implant Systems., in: ANT/SEIT, 1, pp. 98–206.
Debiao, H., Jianhua, C., & Jin, H. (2012). An ID-based client authentication with key agreement protocol for mobile client-server environment on ECC with provable security. Information Fusion, 13(3), 223–230.
Liao, Y.-P., & Hsiao, C.-M. (2014). A secure ECC-based RFID authentication scheme integrated with ID-verifier transfer protocol. Ad Hoc Networks, 18, 133–146.
Turkanović, M., Brumen, B., & Hölbl, M. (2014). A novel user authentication and key agreement scheme for heterogeneous ad hoc wireless sensor networks, based on the Internet of Things notion. Ad Hoc Networks, 20, 96–112.
Farash, M. S., Turkanović, M., Kumari, S., & Hölbl, M. (2016). An efficient user authentication and key agreement scheme for heterogeneous wireless sensor network tailored for the Internet of Things environment. Ad Hoc Networks, 36, 152–176.
Kalra, S., & Sood, S. K. (2015). Secure authentication scheme for IoT and cloud servers. Pervasive and Mobile Computing, 24, 210–223.
Chang, C.-C., Wu, H.-L., & Sun, C.-Y. (2017). Notes on Secure authentication scheme for IoT and cloud servers. Pervasive and Mobile Computing, 38, 275–278.
Von Oheimb, D. (2005). The high-level protocol specification language HLPSL developed in the EU project AVISPA. In Proceedings of APPSEM 2005 workshop, (pp. 1–17).
Abadi, M., Blanchet, B., & Comon-Lundh, H. (2009). Models and proofs of protocol security: A progress report. International Conference on Computer Aided Verification, Springer, (pp. 35–49).
Chaudhry, S. A., Farash, M. S., Naqvi, H., Kumari, S., & Khan, M. K. (2015). An enhanced privacy preserving remote user authentication scheme with provable security. Security and Communication Networks, 8(18), 3782–3795.
Maitra, T., Obaidat, M. S., Amin, R., Islam, S. H., Chaudhry, S. A., & Giri, D. (2017). A robust ElGamal-based password-authentication protocol using smart card for client-server communication. International Journal of Communication Systems, 30(11), e3242.
Dhillon, P. K., & Kalra, S. (2018). Multi-factor user authentication scheme for IoT-based healthcare services. Journal of Reliable Intelligent Environments, 4(3), 141–160.
Xue, K., Hong, P., & Ma, C. (2014). A lightweight dynamic pseudonym identity based authentication and key agreement protocol without verification tables for multi-server architecture. Journal of Computer and System Sciences, 80(1), 195–206.
Feng, Y., Wang, W., Weng, Y. & Zhang, H. (2017) A replay-attack resistant authentication scheme for the internet of things. in 2017 IEEE International Conference on Computational Science and Engineering (CSE) and IEEE International Conference on Embedded and Ubiquitous Computing (EUC), vol. 1, IEEE, (pp. 541–547).
Nikooghadam, M., Jahantigh, R., & Arshad, H. (2017). A lightweight authentication and key agreement protocol preserving user anonymity. Multimedia Tools and Applications, 76(11), 13401–13423.
Kumari, S., Khan, M. K., & Li, X. (2014). An improved remote user authentication scheme with key agreement. Computers & Electrical Engineering, 40(6), 1997–2012.
Alkuhlani, A. M. I., & Thorat, S. (2017). Lightweight anonymity-preserving authentication and key agreement protocol for the internet of things environment. International Conference on Intelligent Information Technologies, Springer, (pp. 108–125).
He, D., & Zeadally, S. (2014). An analysis of RFID authentication schemes for internet of things in healthcare environment using elliptic curve cryptography. IEEE Internet of Things Journal, 2(1), 72–83.
Kalra, S., & Sood, S. K. (2011). Elliptic curve cryptography: survey and its security applications. In Proceedings of the International Conference on Advances in Computing and Artificial. Intelligence, (pp. 102–106).
Wu, S.-T., Chiu, J.-H. & Chieu, B.-C. (2005). ID-based remote authentication with smart cards on open distributed system from elliptic curve cryptography. In textit2005 IEEE International Conference on Electro Information Technology, IEEE,(vol. 5).
Tian, X., Wong, D. S., & Zhu, R. W. (2005). Analysis and improvement of an authenticated key exchange protocol for sensor networks. IEEE Communications Letters, 9(11), 970–972.
Abi-Char, P. E., Mhamed, A. & Bachar, E.-H. (2007). A fast and secure elliptic curve based authenticated key agreement protocol for low power mobile communications. In The 2007 International Conference on Next Generation Mobile Applications, Services and Technologies (NGMAST 2007), IEEE, (pp. 235–240).
Yang, J.-H., & Chang, C.-C. (2009). An ID-based remote mutual authentication with key agreement scheme for mobile devices on elliptic curve cryptosystem. Computers & Security, 28(3–4), 138–143.
Islam, S. H., & Biswas, G. (2011). A more efficient and secure ID-based remote mutual authentication with key agreement scheme for mobile devices on elliptic curve cryptosystem. Journal of Systems and Software, 84(11), 1892–1898.
Ray, S. & Biswas, G. (2012). Establishment of ECC-based initial secrecy usable for IKE implementation. In Proceedings of the World Congress on Engineering, (vol. 1).
Granjal, J., Monteiro, E. & Silva, J. S. (2013). End-to-end transport-layer security for Internet-integrated sensing applications with mutual and delegated ECC public-key authentication. In 2013 IFIP Networking Conference, IEEE, (pp. 1–9).
Jiang, R., Lai, C., Luo, J., Wang, X., & Wang, H. (2013). EAP-based group authentication and key agreement protocol for machine-type communications. International Journal of Distributed Sensor Networks, 9(11), 304601.
Hankerson, D., Menezes, A. J., & Vanstone, S. (2006). Guide to elliptic curve cryptography. Berlin: Springer.
Li, X., Niu, J., Kumari, S., Liao, J., Liang, W., & Khan, M. K. (2016). A new authentication protocol for healthcare applications using wireless medical sensor networks with user anonymity. Security and Communication Networks, 9(15), 2643–2655.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Kumar, A., Abhishek, K., Liu, X. et al. An Efficient Privacy-Preserving ID Centric Authentication in IoT Based Cloud Servers for Sustainable Smart Cities. Wireless Pers Commun 117, 3229–3253 (2021). https://doi.org/10.1007/s11277-020-07979-8
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-020-07979-8