Abstract
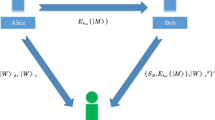
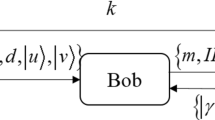
This paper proposes a new way of Quantum signature masked authentication, in which both user and certifying authority is needed for generating final signature. Our scheme uses decoy particle to protect key from all the attacks in the transmission process and does not require encryption of each key. The paper also shows that our scheme is protected against impersonation, forgery and outside attack and is more efficient than the other masked schemes existing in quantum cryptography.




Similar content being viewed by others
Data availability
Provided.
References
Bennett, C. H., & Brassard, G. (1984). Quantum cryptography: Public key distribution and coin tossing. In Proceedings of the IEEE international conference on computers, systems and signal processing, Bangalore, India (pp 175–179).
Ekert, A. (1991). Quantum cryptography based on Bell’s theorem. Physical Review Letters, 67(6), 661–663
Bennett, C. (1992). Quantum cryptography using any two non-orthogonal states. Physical Review Letters, 68(21), 3121–3124
Bechmann-Pasquinucci, H., & Gisin, N. (1999). Incoherent and coherent eavesdropping in the six-state protocol of quantum cryptography. Physical Review A, 59(6), 4238–4248
Inoue, K., Waks, E., & Yamanoto, Y. (2003). Differential-phase-shift quantum key distribution using coherent light. Physical Review A, 68, 022317
Scarani, V., Acin, A., Ribordy, G., & Gisin, N. (2004). Quantum cryptography protocols robust against photon number splitting attack. Physical Review Letters, 92, 057901
Gisin, N., Ribordy, G., Zbinden, H., Stucki, D., Brunner, N., & Scarani, V. (2004). Towards practical and fast quantum cryptography.
Khan, M. M., Khan, M. M., & Arfeen, T. M. A. (2009). High error-rate quantum key distribution for long distance communication. New Journal of Physics, 11, 063043
Esteban, E., & Serna, H. (2012). Quantum key distribution protocol with private- public key. arXiv: 0908.2146v4quant-ph May 12, 2012.
Zhang, X. L. (2009). One-way quantum identity authentication based on public key. Chinese Science Bulletin, 54, 2018–2021
Serna, E. H. (2013). Quantum key distribution from a random seed. arXiv: 1311.1582v2quant-ph November 12, 2013.
Shi, W., Yang, Y., & Zhou, Y. (2015). Quantum signature-masked authentication schemes. Optik, 126, 3544–3548
Fatahi, N., & Afsheh, H. (2018). Secure electronic voting scheme by the new quantum signature-masked authentication. Physics & Astronomy International Journal, 2(6), 586–591
Gottesman, D., & Chuang, I. (2019). Quantum digital signatures. https://arxiv.org/abs/quant-ph/0105032 (2001). Accessed September 2, 2019.
Debnath, B., Das, J. C., De, D., Mondal, S. P., Ahmadian, A., Salimi, M., & Ferrara, M. (2020). Security analysis with novel image masking based quantum-dot cellular automata information security model. IEEE Access (pp. 117159–117172). Digital Object Identifier. https://doi.org/10.1109/ACCESS.2020.3002081
Liu-Jun, W., Kai-Yi, Z., Jia-Yong, W., Jie, C., Yong-Hua, Y., Shi-Biao, T., Di, Y., Yan-Lin, T., Zhen, L., Yu, Y., Qiang, Z., & Jian-Wei, P. (2020). Experimental authentication of quantum key distribution with post-quantum cryptography (pp. 1–8). arXiv:2009.04662.
Liu, B., Gao, Z., Xiao, Di., Huang, W., Zhang, Z., & Bingjie, Xu. (2019). Quantum identity authentication in the counterfactual quantum key distribution protocol. Entropy (Basel), 21(5), 518
Yang, L., Yang, B., & Pan, J. (2010). Quantum public-key encryption protocols with information-theoretic security. In T. Durt & V. N. Zadkov (Eds.), Proceedings of SPIE—The international society for optical engineering. (pp. 88401–88407). SPIE Press. https://doi.org/10.1117/12.922444
Xin, X., Wang, Z., & Yang, Q. (2019). Identity-based quantum signature scheme with strong security. Optical and Quantum Electronics, 51, 393. https://doi.org/10.1007/s11082-019-2072-9
Yang, Y. G., Lei, A. H., Liu, A. Z., Zhou, Y. H., & Shi, W. M. (2016). Arbitrated quantum signature scheme based on cluster states. Quantum Information Processing, 15, 2487–2497
Ekert, A., Hayden, P., & Inamori, H. (2000). Basic concepts in quantum computation. arXiv:quant-ph/0011013.
Funding
NA.
Author information
Authors and Affiliations
Contributions
We have proposed new quantum Quantum signature masked authentication protocol which is more secure than previously existing schemes.
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Verma, V., Malhotra, K. A New Secure Quantum Signature Masked Authentication Scheme. Wireless Pers Commun 120, 1659–1674 (2021). https://doi.org/10.1007/s11277-021-08527-8
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-021-08527-8