Abstract
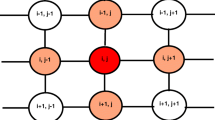
In this article, we secure the healthcare data using low complexity hybrid cellular automata (CA) algorithm while enabling remote monitoring of patients using IoT (Internet of Things) network. Since IoT devices are limited to power and memory space, the traditional encryption and decryption algorithms, called as ciphers, cannot be executed owing to the inherent implementation complexities and power requirements. The results show that the encrypted data sequence passes the randomness tests as prescribed by the National Institute of Standards and Technology (NIST) and is suitable for cryptography. Comparison with the state-of-the-art methods proves the superiority of our proposed method in terms of run-time complexity. Using the proposed hybrid CA algorithm, we achieve an average execution time of 0.3892 seconds per kilobit (kb) of data.










Similar content being viewed by others
References
Kumar, R., Khan, P., Kumar, S. (2019). A cellular automata-based healthcare data encryption technique for iot networks. In 2019 IEEE 16th India Council International Conference (INDICON) (pp. 1–4). https://doi.org/10.1109/INDICON47234.2019.9030349
Al Ameen, M., Liu, J., & Kwak, K. (2012). Security and privacy issues in wireless sensor networks for healthcare applications. Journal of Medical Systems, 36(1), 93–101.
Islam, S. R., Kwak, D., Kabir, M. H., Hossain, M., & Kwak, K.-S. (2015). The internet of things for health care: A comprehensive survey. IEEE Access, 3, 678–708.
Sharma, P. K., Chen, M.-Y., & Park, J. H. (2017). A software defined fog node based distributed blockchain cloud architecture for IoT. IEEE Access, 6, 115–124.
Meingast, M., Roosta, T., Sastry, S. (2006). Security and privacy issues with health care information technology. In 2006 International Conference of the IEEE Engineering in Medicine and Biology Society (pp. 5453–5458). IEEE.
Fuster-Sabater, A., & Caballero-Gil, P. (2006). On the use of cellular automata in symmetric cryptography. Acta Applicandae Mathematica, 93(1–3), 215–236.
Díaz Len, R., Hernández Encinas, A., Hernández Encinas, L., Martín del Rey, Á., Rodríguez Sánchez, G., Visus Ruiz, I. (2003). Wolfram cellular auto mata and their cryptographic use as pseudorandom bit generators.
Roy, S., Karjee, J., Rawat, U., Dey, N., et al. (2016). Symmetric key encryption technique: A cellular automata based approach in wireless sensor networks. Procedia Computer Science, 78, 408–414.
Roy, S., Nandi, S., Dansana, J., Pattnaik, P. K. (2014). Application of cellular automata in symmetric key cryptography. In 2014 International Conference on Communication and Signal Processing (pp. 572–576). IEEE.
Roy, S., Rawat, U., & Karjee, J. (2019). A lightweight cellular automata based encryption technique for IoT applications. IEEE Access, 7, 39782–39793.
Fensli, R., Gunnarson, E., Hejlesen, O. (2004). A wireless ecg system for continuous event recording and communication to a clinical alarm station. In The 26th Annual International Conference of the IEEE Engineering in Medicine and Biology Society, vol. 1 (pp. 2208–2211). IEEE.
Ng, H., Sim, M., & Tan, C. (2006). Security issues of wireless sensor networks in healthcare applications. BT Technology Journal, 24(2), 138–144.
Hodge, J. G., Jr. (2003). Health information privacy and public health. The Journal of Law, Medicine & Ethics, 31(4), 663–671.
Shah, K. T. (2019). Privacy and security issues of wearables in healthcare. PhD thesis, Flinders University, College of Science and Engineering.
Alagar, V., Alsaig, A., Ormandjiva, O., Wan, K. (2018). Context-based security and privacy for healthcare IoT. In 2018 IEEE International Conference on Smart Internet of Things (SmartIoT) (pp. 122–128). IEEE.
Jangra, P., Gupta, M. (2018). A design of real-time multilayered smart healthcare monitoring framework using IoT. In 2018 International Conference on Intelligent and Advanced System (ICIAS) (pp. 1–5). IEEE.
Alaba, F. A., Othman, M., Hashem, I. A. T., & Alotaibi, F. (2017). Internet of things security: A survey. Journal of Network and Computer Applications, 88, 10–28.
Conti, M., Dehghantanha, A., Franke, K., Watson, S. (2018). Internet of Things security and forensics: Challenges and opportunities. Elsevier.
Nandi, S., Kar, B. K., & Chaudhuri, P. P. (1994). Theory and applications of cellular automata in cryptography. IEEE Transactions on Computers, 43(12), 1346–1357.
Sarkar, P. (2000). A brief history of cellular automata. Acm Computing Surveys (csur), 32(1), 80–107.
Wolfram, S. (1986). Theory and applications of cellular automata. World Scientific.
Das, A. K., Sanyal, A., & Palchaudhuri, P. (1992). On characterization of cellular automata with matrix algebra. Information Sciences, 61(3), 251–277.
Martin, O., Odlyzko, A. M., & Wolfram, S. (1984). Algebraic properties of cellular automata. Communications in Mathematical Physics, 93(2), 219–258.
Pries, W., Thanailakis, A., & Card, H. C. (1986). Group properties of cellular automata and VLSI applications. IEEE Transactions on Computers, 12, 1013–1024.
Rukhin, A., Soto, J., Nechvatal, J., Smid, M., & Barker, E. (2001). A statistical test suite for random and pseudorandom number generators for cryptographic applications. Booz-allen and hamilton inc mclean va: Technical report.
Smid, E.B., Leigh, S., Levenson, M., Vangel, M., DavidBanks, A., JamesDray, S. (2001). A statistical test suite for random and pseudorandom number generators for cryptographic applications.
Das, D., Misra, R. (2011). Programmable cellular automata based efficient parallel AES encryption algorithm. arXiv preprint arXiv:1112.2021
Singh, S., Maakar, S. K., & Kumar, S. (2013). A performance analysis of DES and RSA cryptography. International Journal of Emerging Trends & Technology in Computer Science (IJETTCS), 2(3), 418–423.
Singh, A., Marwaha, M., Singh, B., & Singh, S. (2013). Comparative study of DES, 3DES, AES and RSA. International Journal of Computers & Technology, 9(3), 1164–1170.
Funding
This work acknowledges the support rendered by the Early Career Research (ECR) award scheme project “Cyber-Physical Systems for M-Health" (ECR/2016/001532) (duration 2017-2020), under Science and Engineering Research Board (SERB), Govt. of India.
Author information
Authors and Affiliations
Contributions
All authors contributed to the study conception and design. Data collection was performed by Pritam Khan and analysis was performed by Ritesh Kumar. Material preparation, revision, and correction were performed by Ritesh Kumar, Pritam Khan, and Sudhir Kumar. The first draft of the manuscript was written by Ritesh Kumar and all authors commented on previous versions of the manuscript. All authors read and approved the final manuscript.
Corresponding author
Ethics declarations
Conflicts of Interests
The authors have no relevant financial or non-financial interests to disclose.
Data Availability
No database is associated with the present work. However, the sample ECG data used as example in the work, is already disclosed in detail inside the manuscript.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Kumar, R., Khan, P. & Kumar, S. Healthcare Data Encryption Technique Using Hybrid Cellular Automata in IoT Networks. Wireless Pers Commun 126, 3021–3039 (2022). https://doi.org/10.1007/s11277-022-09850-4
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-022-09850-4