Abstract
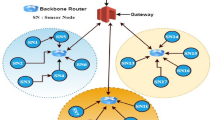
As the basis of the Internet of Things (IoT), sensor networks have materialized its computation and communication capability into anything in our modern lives. Service composition provides us a promising way to cooperate various sensors to build more powerful IoT applications over sensor networks. However, the limited capability of sensor node poses great challenges not only to trustworthy service composition but also to secure data aggregation. The complex composite structure, computation-intensive evaluation, and massive data transmission become burdens for service composition in sensor networks. To overcome these issues, this paper proposes a distributed approach to enable efficient trustworthy service composition with secure data transmission in sensor networks. By analyzing dependency relationships, the rules for computing service trust and data trust are proposed based a multi-level trust model. Then, each target component service can be evaluated independently through a model checker. Moreover, an identity-based aggregate signature is introduced in the composite evaluation to guarantee the secure data transmission among different components. The experimental results show that our approach not only achieves efficient trustworthy service composition with complex invocation structures, but also reduces the costs in the secure data transmission.







Similar content being viewed by others
References
Atzori, L., Iera, A., Morabito, G.: The internet of things: A survey. Comput. Netw. 54(15), 2787 – 2805 (2010). doi:10.1016/j.comnet.2010.05.010
Boyle, D.E., Yates, D.C., Yeatman, E.M.: Urban sensor data streams: London 2013. IEEE Internet Comput. 17(6), 12–20 (2013). doi:10.1109/MIC.2013.85
Holzmann, G.J.: The model checker spin. IEEE Trans. Softw. Eng. 23(5), 279–295 (1997). doi:10.1109/32.588521
Huang, J., Peng, M., Wang, H., Cao, J., Gao, W., Zhang, X.: A probabilistic method for emerging topic tracking in microblog stream. World Wide Web 20(2), 325–350 (2017). doi:10.1007/s11280-016-0390-4
Hutter, D., Volkamer, M.: Information flow control to secure dynamic web service composition, pp 196–210. Springer Berlin Heidelberg, Berlin, Heidelberg (2006)
Jøsang, A., Ismail, R., Boyd, C.: A survey of trust and reputation systems for online service provision. Decis. Support. Syst. 43(2), 618 – 644 (2007). doi:10.1016/j.dss.2005.05.019
Kyusakov, R., Eliasson, J., Delsing, J., Van Deventer, J., Gustafsson, J.: Integration of wireless sensor and actuator nodes with it infrastructure using service-oriented architecture. IEEE Trans. Indust. Inform. 9(1), 43–51 (2013). doi:10.1109/TII.2012.2198655
Li, L., Wang, Y.: Trust evaluation in composite services selection and discovery SCC, pp 482–485 (2009). doi:10.1109/SCC.2009.70
Liang, X., Li, X., Lu, R., Lin, X., Shen, X.: Seer: A secure and efficient service review system for service-oriented mobile social networks. In: 2012 IEEE 32nd International Conference on Distributed Computing Systems (ICDCS), pp. 647–656 (2012). doi:10.1109/ICDCS.2012.46
Liu, X., Zhu, H., Ma, J., Li, Q., Xiong, J.: Efficient attribute based sequential aggregate signature for wireless sensor networks. Int. J. Sensor Netw. 16(3), 172–184 (2014)
Malik, Z., Bouguettaya, A.: Rateweb: Reputation assessment for trust establishment among web services. VLDB J. 18(4), 885–911 (2009)
Shen, L., Ma, J., Liu, X., Wei, F., Miao, M.: A secure and efficient id-based aggregate signature scheme for wireless sensor networks. IEEE Internet Things J. PP(99), 1–1 (2016). doi:10.1109/JIOT.2016.2557487
Sherchan, W., Nepal, S., Paris, C.: A survey of trust in social networks. ACM Comput. Surv. 45(4), 47:1–47:33 (2013). doi:10.1145/2501654.2501661
Snelting, G., Robschink, T., Krinke, J.: Efficient path conditions in dependence graphs for software safety analysis. ACM Trans. Softw. Eng. Methodol. 15(4), 410–457 (2006). doi:10.1145/1178625.1178628
Wang, Y., Li, L.: Two-dimensional trust rating aggregations in service-oriented applications. IEEE Trans. Serv. Comput. 4(4), 257–271 (2011). doi:10.1109/TSC.2010.39
Wang, Y., Lin, K.J.: Reputation-oriented trustworthy computing in e-commerce environments. IEEE Internet Comput. 12(4), 55–59 (2008). doi:10.1109/MIC.2008.84
Xi, N., Ma, J., Sun, C., Zhang, T.: Decentralized information flow verification framework for the service chain composition in mobile computing environments. In: 2013 IEEE 20th International Conference on Web Services (ICWS), pp. 563–570 (2013). doi:10.1109/ICWS.2013.81
Xi, N., Sun, C., Ma, J., Shen, Y.: Secure service composition with information flow control in service clouds. Futur. Gener. Comput. Syst. 49, 142 – 148 (2015). doi:10.1016/j.future.2014.12.009
Yan, Z., Zhang, P., Vasilakos, A.V.: A survey on trust management for internet of things. J. Netw. Comput. Appl. 42, 120 – 134 (2014). doi:10.1016/j.jnca.2014.01.014
Yang, P., Yang, Z., Lu, S.: Formal modeling and analysis of scientific workflows using hierarchical state machines. In: IEEE International Conference on e-Science and Grid Computing. doi:10.1109/E-SCIENCE.2007.35 (2007)
Yu, H., Shen, Z., Leung, C., Miao, C., Lesser, V.R.: A survey of multi-agent trust management systems. IEEE Access 1, 35–50 (2013). doi:10.1109/ACCESS.2013.2259892
Zhang, T., Ma, J., Li, Q., Xi, N., Sun, C.: Trust-based service composition in multi-domain environments under time constraint. Sci. China Inf. Sci. 57(9), 1–16 (2014). doi:10.1007/s11432-014-5104-x
Zhang, T., Ma, J., Sun, C., Li, Q., Xi, N.: Service composition in multi-domain environment under time constraint. In: ICWS, pp. 227–234 (2013). doi:10.1109/ICWS.2013.39
Zhang, T., Ma, J., Xi, N., Liu, X., Liu, Z., Xiong, J.: Trustworthy service composition in service-oriented mobile social networks. In: 2014 IEEE International Conference on Web Services (ICWS), pp. 684–687 (2014). doi:10.1109/ICWS.2014.102
Acknowledgements
We wish to thank the anonymous reviewers for their highly valuable and constructive comments. This paper is supported by the National Natural Science Foundation of China (No. 61602365, U1536202, 61571352, 61373173 and 61602364), the Open Fund of the Chinese Key Laboratory of the Grain Information Processing and Control (No. KFJJ-2015-202), and the Fundamental Research Funds for the Central Universities (No. XJS15075).
Author information
Authors and Affiliations
Corresponding author
Additional information
This article belongs of the Topical Collection: Special Issue on Security and Privacy of IoT
Guest Editors: Tarik Taleb, Zonghua Zhang, and Hua Wang
Rights and permissions
About this article
Cite this article
Zhang, T., Zheng, L., Wang, Y. et al. Trustworthy service composition with secure data transmission in sensor networks. World Wide Web 21, 185–200 (2018). https://doi.org/10.1007/s11280-017-0465-x
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11280-017-0465-x