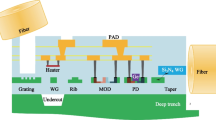
Abstract
Intellectual property (IP) protection is one of the hardcore problems in hardware security. Semiconductor industry still lacks effective and proactive defense to shield IPs from reverse engineering (RE) based attacks. Integrated circuit (IC) camouflaging technique fills this gap by replacing some conventional logic gates in the IPs with specially designed logic cells (called camouflaged gates) without changing the functions of the IPs. The camouflaged gates can perform different logic functions while maintaining an identical look to RE attackers, thus preventing them from obtaining the layout information of the IP directly from RE tools. Since it was first proposed in 2012, circuit camouflaging has become one of the hottest research topics in hardware security focusing on two fundamental problems. How to choose the types of camouflaged gates and decide where to insert them in order to simultaneously minimize the performance overhead and optimize the RE complexity? How can an attacker de-camouflage a camouflaged circuit and complete the RE attack? In this article, we review the evolution of circuit camouflaging through this spear and shield race. First, we introduce the design methods of four different kinds of camouflaged cells based on true/dummy contacts, static random access memory (SRAM), doping, and emerging devices, respectively. Then we elaborate four representative de-camouflaging attacks: brute force attack, IC testing based attack, satisfiability-based (SAT-based) attack, and the circuit partition based attack, and the corresponding countermeasures: clique-based camouflaging, CamoPerturb, AND-tree camouflaging, and equivalent class based camouflaging, respectively. We argue that the current research efforts should be on reducing overhead introduced by circuit camouflaging and defeating de-camouflaging attacks. We point out that exploring features of emerging devices could be a promising direction. Finally, as a complement to circuit camouflaging, we conclude with a brief review of other state-of-the-art IP protection techniques.
Similar content being viewed by others
References
Qu G, Potkonjak M. Intellectual Property Protection in VLSI Designs: Theory and Practice. Kluwer Academic Publishers, 2003.
Rostami M, Koushanfar F, Karri R. A primer on hardware security: Models, methods, and metrics. Proceedings of the IEEE, 2014, 102(8): 1283-1295.
Jin Y E. Introduction to hardware security. Electronics, 2015, 4(4): 763-784.
Lv Y Q, Zhou Q, Cai Y C, Qu G. Trusted integrated circuits: The problem and challenges. Journal of Computer Science and Technology, 2014, 29(5): 918-928.
Quadir S E, Chen J L, Forte D, Asadizanjani N, Shahbazmohamadi S, Wang L, Chandy J, Tehranipoor M. A survey on chip to system reverse engineering. ACM Journal on Emerging Technologies in Computing Systems (JETC), 2016, 13(1): Article No. 6.
Adee S. The hunt for the kill switch. IEEE Spectrum, 2008, 45(5): 34-39.
Qu G, Potkonjak M. Fingerprinting intellectual property using constraint-addition. In Proc. the 37th Annual Design Automation Conf., June 2000, pp.587-592.
Dunbar C, Qu G. Satisfiability Don’t Care condition based circuit fingerprinting techniques. In Proc. the 20th Asia and South Pacific Design Automation Conf., January 2015, pp.815-820.
Kahng A B, Lach J, Mangione-Smith W H, Mantik S, Markov I L, Potkonjak M, Tucker P, Wang H, Wolfe G. Constraint-based watermarking techniques for design IP protection. IEEE Trans. Computer-Aided Design of Integrated Circuits and Systems, 2001, 20(10): 1236-1252.
Dunbar C, Qu G. A practical circuit fingerprinting method utilizing observability Don’t Care conditions. In Proc. the 52nd ACM/EDAC/IEEE Design Automation Conf., June 2015.
Chow L W, Baukus J P, Wang B J, Cocchi R P. Camouflaging a standard cell based integrated circuit: US Patent 8151235, April 3, 2012. http://www.freepatentsonline.com/8151235.html, Dec. 2017.
Rajendran J, Sam M, Sinanoglu O, Karri R. Security analysis of integrated circuit camouflaging. In Proc. ACM SIGSAC Conf. Computer & Communications Security, November 2013, pp.709-720.
Wang X Y, Gao M Z, Zhou Q, Cai Y C, Qu G. Gate camouflaging-based obfuscation. In Hardware Protection through Obfuscation, Forte D, Bhunia S, Tehranipoor M M (eds.), Springer, 2017, pp.89-102.
Subramanyan P, Ray S, Malik S. Evaluating the security of logic encryption algorithms. In Proc. IEEE Int. Symp. Hardware Oriented Security and Trust, May 2015, pp.137-143.
Massad M E, Garg S, Tripunitara M V. Integrated circuit (IC) decamouflaging: Reverse engineering camouflaged ICs within minutes. In Proc. the 22nd Annual Network and Distributed System Security Symp., February 2015.
Liu D, Yu C X, Zhang X Y, Holcomb D. Oracle-guided incremental SAT solving to reverse engineer camouflaged logic circuits. In Proc. Design Automation & Test in Europe Conf. Exhibition, March 2016, pp.433-438.
Wang X Y, Zhou Q, Cai Y C, Qu G. Is the secure IC camouflaging really secure? In Proc. IEEE Int. Symp. Circuits and Systems, May 2016, pp.1710-1713.
Liu B,Wang B. Embedded reconfigurable logic for ASIC design obfuscation against supply chain attacks. In Proc. Design Automation & Test in Europe Conf. Exhibition, March 2014.
Wang X Y, Jia X T, Zhou Q, Cai Y C, Yang J L, Gao M Z, Qu G. Secure and low-overhead circuit obfuscation technique with multiplexers. In Proc. the 26th Edition on Great Lakes Symp. VLSI, May 2016, pp.133-136.
Yasin M, Mazumdar B, Sinanoglu O, Rajendran J. Camoperturb: Secure IC camouflaging for minterm protection. In Proc. the 35th Int. Conf. Computer-Aided Design, November 2016, Article No. 29.
Li M, Shamsi K, Meade T, Zhao Z, Yu B, Jin Y E, Pan D Z. Provably secure camouflaging strategy for IC protection. In Proc. the 35th Int. Conf. Computer-Aided Design, November 2016, Article No. 28.
Chow L W, Baukas J P, Clark Jr W M. Integrated circuits protected against reverse engineering and method for fabricating the same using an apparent metal contact line terminating on field oxide. US Patent 20020096776, Jul. 25, 2002. http://www.freepatentsonline.com/20020096776.pdf, Jan. 2018.
Baukus J P, Chow L W, Clark Jr W M. Method and apparatus using silicide layer for protecting integrated circuits from reverse engineering. US Patent 6117762, Sept. 12, 2000. http://www.freepatentsonline.com/6117762.html, Dec. 2017.
Cocchi R P, Baukus J P, Wang B J, Chow L W, Ouyang P. Building block for a secure CMOS logic cell library. US Patent 8111089, Feb. 7, 2012. http://www.freepatentsonline.com/8111089.html, Dec. 2017.
Chow L W, Clark Jr W M, Harbison G J, Baukus J P. Conductive channel pseudo block process and circuit to inhibit reverse engineering. US Patent 7049667, May 23, 2006. http://www.freepatentsonline.com/8258583.html, Dec. 2017.
Clark Jr W M, Chow L W, Harbison G, Ouyang P. Programmable connection and isolation of active regions in an integrated circuit using ambiguous features to confuse a reverse engineer. US Patent 8564073, Oct. 22, 2013. http://www.freepatentsonline.com/8564073.html, Dec. 2017.
Clark Jr W M, Baukus J, Chow L W. Implanted hidden interconnections in a semiconductor device for preventing reverse engineering. US Patent 7166515, Jan. 23, 2007. http://www.freepatentsonline.com/7166515.html, Dec. 2017.
Liu B, Wang B. Reconfiguration-based VLSI design for security. IEEE Journal on Emerging and Selected Topics in Circuits and Systems, 2015, 5(1): 98-108.
Becker G T, Regazzoni F, Paar C, Burleson W P. Stealthy dopant-level hardware trojans: Extended version. Journal of Cryptographic Engineering, 2014, 4(1): 19-31.
Chow L W, Clark Jr W M, Baukus J P. Covert transformation of transistor properties as a circuit protection method. US Patent 7217977, May 15, 2007. http://www.freepatentsonline.com/7217977.html, Dec. 2017.
Ma K S, Liu H C, Xiao Y, Zheng Y, Li X Q, Gupta S K, Xie Y, Narayanan V. Independently-controlled-gate Fin-FET 6T SRAM cell design for leakage current reduction and enhanced read access speed. In Proc. IEEE Computer Society Annual Symp. VLSI, July 2014, pp.296-301.
Sedighi B, Hu X S, Nahas J J, Niemier M. Nontraditional computation using beyond-CMOS tunneling devices. IEEE Journal on Emerging and Selected Topics in Circuits and Systems, 2014, 4(4): 438-449.
Lin S, Kim Y B, Lombardi F. CNTFET-based design of ternary logic gates and arithmetic circuits. IEEE Trans. Nanotechnology, 2011, 10(2): 217-225.
Zhao P, Feenstra R M, Gu G, Jena D. SymFET: A proposed symmetric graphene tunneling field-effect transistor. IEEE Trans. Electron Devices, 2013, 60(3): 951-957.
Chua L. Memristor—the missing circuit element. IEEE Trans. Circuit Theory, 1971, 18(5): 507-519.
Strukov D B, Snider G S, Stewart D R, Williams R S. The missing memristor found. Nature, 2008, 453(7191): 80-83.
Roy K, Sharad M, Fan D L, Yogendra K. Computing with spin-transfer-torque devices: Prospects and perspectives. In Proc. IEEE Computer Society Annual Symp. VLSI, July 2014, pp.398-402.
Chen A, Hu X S, Jin Y E, Niemier M, Yin X Z. Using emerging technologies for hardware security beyond PUFs. In Proc. Design Automation & Test in Europe Conf. Exhibition, March 2016, pp.1544-1549.
Shamsi K, Jin Y. Security of emerging non-volatile memories: Attacks and defenses. In Proc. the 34th IEEE VLSI Test Symp., April 2016.
Arafin M T, Qu G. RRAM based lightweight user authentication. In Proc. IEEE/ACM Int. Conf. Computer-Aided Design, November 2015, pp.139-145.
Arafin M T, Dunbar C, Qu G, McDonald N, Yan L. A survey on memristor modeling and security applications. In Proc. the 16th Int. Symp. Quality Electronic Design, March 2015, pp.440-447.
Winograd T, Salmani H, Mahmoodi H, Gaj K, Homayoun H. Hybrid STT-CMOS designs for reverse-engineering prevention. In Proc. the 53rd ACM/EDAC/IEEE Design Automation Conf., June 2016.
Bi Y, Shamsi K, Yuan J S, Gaillardon P E, De Micheli G, Yin X Z, Hu X S, Niemier M, Jin Y. Emerging technologybased design of primitives for hardware security. ACM Journal on Emerging Technologies in Computing Systems, 2016, 13(1): Article No. 3.
Bi Y, Gaillardon P E, Hu X S, Niemier M, Yuan J S, Jin Y. Leveraging emerging technology for hardware securitycase study on silicon nanowire fets and graphene symfets. In Proc. the 23rd IEEE Asian Test Symp., November 2014, pp.342-347.
Shamsi K, Wen W J, Jin Y. Hardware security challenges beyond CMOS: Attacks and remedies. In Proc. IEEE Computer Society Annual Symp. VLSI, July 2016, pp.200-205.
Bobba S, De Marchi M, Leblebici Y, De Micheli G. Physical synthesis onto a sea-of-tiles with double-gate silicon nanowire transistors. In Proc. the 49th Annual Design Automation Conf., June 2012, pp.42-47.
Suzuki D, Natsui M, Ikeda S, Hasegawa H, Miura K, Hayakawa J, Endoh T, Ohno H, Hanyu T. Fabrication of a nonvolatile lookup-table circuit chip using magneto/semiconductor-hybrid structure for an immediatepower-up field programmable gate array. In Proc. Symp. VLSI Circuits, June 2009, pp.80-81.
Mahmoodi H, Lakshmipuram S S, Arora M, Asgarieh Y, Homayoun H, Lin B, Tullsen D M. Resistive computation: A critique. IEEE Computer Architecture Letters, 2014, 13(2): 89-92.
Rajendran J, Sinanoglu O, Karri R. VLSI testing based security metric for IC camouflaging. In Proc. IEEE Int. Test Conf., September 2013.
Lee H K, Ha D S. HOPE: An efficient parallel fault simulator for synchronous sequential circuits. IEEE Trans. Computer-Aided Design of Integrated Circuits and Systems, 1996, 15(9): 1048-1058.
Jarvis R W, Mcintyre M G. Split manufacturing method for advanced semiconductor circuits. US Patent 7195931, March 27, 2007. http://www.freepatentsonline.com/7195931.html, Dec. 2017.
Imeson F, Emtenan A, Garg S, Tripunitara M V. Securing computer hardware using 3D integrated circuit (IC) technology and split manufacturing for obfuscation. In Proc. the 22nd USENIX Conf. Security, August 2013, pp.495-510.
Valamehr J, Sherwood T, Kastner R, Marangoni-Simonsen D, Huffmire T, Irvine C, Levin T. A 3-D split manufacturing approach to trustworthy system development. IEEE Trans. Computer-Aided Design of Integrated Circuits and Systems, 2013, 32(4): 611-615.
Rajendran J, Sinanoglu O, Karri R. Is split manufacturing secure? In Proc. Design Automation & Test in Europe Conf. Exhibition, March 2013, pp.1259-1264.
Vaidyanathan K, Liu R Z, Sumbul E, Zhu Q L, Franchetti F, Pileggi L. Efficient and secure intellectual property (IP) design with split fabrication. In Proc. IEEE Int. Symp. Hardware-Oriented Security and Trust, May 2014, pp.13-18.
Jagasivamani M, Gadfort P, Sika M, Bajura M, Fritze M. Split-fabrication obfuscation: Metrics and techniques. In Proc. IEEE Int. Symp. Hardware-Oriented Security and Trust, May 2014, pp.7-12.
Roy J A, Koushanfar F, Markov I L. EPIC: Ending piracy of integrated circuits. In Proc. Design Automation and Test in Europe, March 2008, pp.1069-1074.
Rajendran J, Pino Y, Sinanoglu O, Karri R. Security analysis of logic obfuscation. In Proc. the 49th ACM/EDAC/IEEE Design Automation Conf. June 2012, pp.83-89.
Baumgarten A, Tyagi A, Zambreno J. Preventing IC piracy using reconfigurable logic barriers. IEEE Design & Test of Computers, 2010, 27(1): 66-75.
Alkabani Y M, Koushanfar F. Active hardware metering for intellectual property protection and security. In Proc. the 16th USENIX Security Symp., August 2007.
Chakraborty R S, Bhunia S. HARPOON: An obfuscationbased SoC design methodology for hardware protection. IEEE Trans. Computer-Aided Design of Integrated Circuits and Systems, 2009, 28(10): 1493-1502.
Zamanzadeh S, Jahanian A. Automatic netlist scrambling methodology in ASIC design flow to hinder the reverse engineering. In Proc. the 21st IFIP/IEEE Int. Conf. Very Large Scale Integration, October 2013, pp.52-53.
Yasin M, Rajendran J J, Sinanoglu O, Karri R. On improving the security of logic locking. IEEE Trans. Computer-Aided Design of Integrated Circuits and Systems, 2016, 35(9): 1411-1424.
Yasin M, Mazumdar B, Rajendran J J V, Sinanoglu O. Sarlock: SAT attack resistant logic locking. In Proc. IEEE Int. Symp. Hardware Oriented Security and Trust, May 2016, pp.236-241.
Suh G E, Devadas S. Physical unclonable functions for device authentication and secret key generation. In Proc. the 44th ACM/IEEE Design Automation Conf., June 2007, pp.9-14.
Herder C, Yu M D, Koushanfar F, Devadas S. Physical unclonable functions and applications: A tutorial. Proceedings of the IEEE, 2014, 102(8): 1126-1141.
Yamamoto D, Takenaka M, Sakiyama K, Torii N. A technique using PUFs for protecting circuit layout designs against reverse engineering. In Proc. the 9th International Workshop on Security, August 2014, pp.158-173.
Wendt J B, Potkonjak M. Hardware obfuscation using PUFbased logic. In Proc. IEEE/ACM Int. Conf. Computer- Aided Design, November 2014, pp.270-277.
Lee J W, Lim D, Gassend B, Suh G E, Van Dijk M, Devadas S. A technique to build a secret key in integrated circuits for identification and authentication applications. In Proc. Symp. VLSI Circuits Digest of Technical Papers, June 2004, pp.176-179.
Zhang J L, Qu G, Lv Y Q, Zhou Q. A survey on silicon PUFs and recent advances in ring oscillator PUFs. Journal of Computer Science and Technology, 2014, 29(4): 664-678.
Forte D, Bhunia S, Tehranipoor M M. Hardware Protection through Obfuscation. Springer, 2017.
Yasin M, Sinanoglu O. Transforming between logic locking and IC camouflaging. In Proc. the 10th Int. Design & Test Symp., December 2015.
Author information
Authors and Affiliations
Corresponding author
Electronic supplementary material
Below is the link to the electronic supplementary material.
ESM 1
(PDF 863 kb)
Rights and permissions
About this article
Cite this article
Wang, XY., Zhou, Q., Cai, YC. et al. Spear and Shield: Evolution of Integrated Circuit Camouflaging. J. Comput. Sci. Technol. 33, 42–57 (2018). https://doi.org/10.1007/s11390-018-1807-6
Received:
Revised:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11390-018-1807-6