Abstract
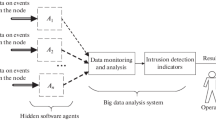
In this paper, we propose a novel distributed intrusion detection system based on multi-living agent inspired by the research method of multi-living agent complex information system for improving the security of distributed intrusion detection system using mobile agent. The previous two-layer distributed intrusion detection system has been expanded into a three-layer structure, the new layer of which can monitor the livelihood of each detection agent and utilize the negotiation-coordination mechanism to adjust the working way of each agent for protecting the security of system. In this paper, we propose a quantitative analysis method of agent livelihood in distributed intrusion detection system and further present the design method of living agent. Finally, through the analysis of system working flow and the detection effect of distributed denial of service attack, we have shown that the security and stability of the novel distributed intrusion detection system is effectively enhanced and the agent can work normally in strict restraint strong countermeasure environment.
Similar content being viewed by others
References
Patil N, Chhaya D, Shreya P, et al. Analysis of distributed intrusion detection system using mobile agents. In: Proceedings of the 2008 First International Conference on Emerging Trends in Engineering and Technology, Washington, DC, USA, 2008. 1255–1260
Snapp S R, Brentano J, Dias G V, et al. DIDS (distributed intrusion detection system)-motivation,architecture, and an early prototype. In: Proceedings of the 14th National Computer Security Conference. New York, USA, 1991. 167–176
Chandler J A. Security in cyberspace: combating distributed denial of service attacks. Univ Ottawa Law Tech J, 2003, 1: 231–261
Kruegel C, Toth T. Applying mobile agent technology to intrusion detection. In: ICSE Workshop on Software Engineering and Mobility, Toronto, 2001. 1–5
Borselius N. Mobile agent security. Electr Commun Eng J, 2002, 14: 211–218
Zhong S C, Song Q, Cheng X C, et al. A safe mobile agent system for distributed intrusion detection. In: Proceedings of Second International Conference on Machine Learning and Cybernetics. Xi’an, 2003. 2009–2014
Wang Y, Tao R, Li B Z. Using the multi-living agent concept to investigate complex information systems. Sci China Ser F-Inf Sci, 2009, 52: 1–17
Xu G H. Stochastic Service System (in Chinese). Beijing: Science Press, 1980
White J. Telescript technology: Mobile agents. In: Bradshaw J, ed. Software Agents. New York: MIT Press, 1996. 1871–1879
Vu Anh Pham, Karmouch A. Mobile software agents: an overview. Commun Magaz, IEEE, 1998, 36: 26–37
Horvat D, Cvetkovic D, Milutinovic V, et al. Mobile agents and Java mobile agents toolkits. In: Proceedings of the 33th Hawaii International Conference on System Sciences, 2000, 4–7: 1–10
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Wang, Y., Tao, R. & Zhang, H. Research on distributed intrusion detection system based on multi-living agent. Sci. China Inf. Sci. 53, 1067–1077 (2010). https://doi.org/10.1007/s11432-010-0086-9
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11432-010-0086-9