Abstract
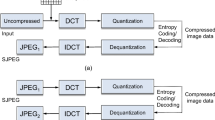
Non-intrusive digital image forensics (NIDIF) is a novel approach to authenticate the trustworthiness of digital images. It works by exploring varieties of intrinsic characteristics involved in the digital imaging, editing, storing processes as discriminative features to reveal the subtle traces left by a malicious fraudster. The NIDIF for the lossy JPEG image format is of special importance for its pervasive application. In this paper, we propose an NIDIF framework for the JPEG images. The framework involves two complementary identification methods for exposing shifted double JPEG (SD-JPEG) compression artifacts, including an improved ICA-based method and a First Digits Histogram based method. They are designed to treat the detectable conditions and a few special undetectable conditions separately. Detailed theoretical justifications are provided to reveal the relationship between the detectability of the artifacts and some intrinsic statistical characteristics of natural image signal. The extensive experimental results have shown the effectiveness of the proposed methods. Furthermore, some case studies are also given to demonstrate how to reveal certain types of image manipulations, such as cropping, splicing, or both, with our framework.
Similar content being viewed by others
References
Mehdi K L, Sencar H T, Memon N. Blind source camera identification. In: Proceedings of the IEEE International Conference on Image Processing, Singapore, 2004. 709–712
Fridrich J, Soukal D, Lukáš J. Detection of copy-move forgery in digital images. In: Proceedings of Digital Forensic Research Workshop, Cleveland, 2003
Farid H. Image forgery detection. Signal Process Mag, 2009, 26: 16–25
Farid H. Detecting digital forgeries using bispectral analysis. Technical Report AIM-1657. 1999
Popescu A C, Farid H. Exposing digital forgeries by detecting traces of resampling. IEEE Trans Signal Process, 2005, 53: 758–767
Shi Y Q, Chen C H, Chen W. A natural image model approach to splicing detection. In: Proceedings of ACM Workshop on Multimedia and Security, Dallas, 2007. 51–62
Kee E, Farid H. Digital image authentication from thumbnails. In: Proceedings of SPIE 7541, Media Forensics and Security II, San Francisco, 2010. 75410E
Kee E, Johnson M K, Farid H. Digital image authentication from jpeg headers. IEEE Trans Inf Forens Secur, 2011, 6: 1066–1075
Bayram S, Sencar H, Memon N. Identifying digital cameras using cfa interpolation. In: Proceedings of IFIP International Conference on Digital Forensics. New York: Springer, 2006. 289–299
Johnson M K, Farid H. Exposing digital forgeries through chromatic aberration. In: Proceedings of ACM Workshop on Multimedia and Security, Geneva, 2006. 48–55
Chen M, Fridrich J, Lukáš J, et al. Imaging sensor noise as digital X-ray for revealing forgeries. In: Proceedings of the 9th Information Hiding Workshop, Saint Malo, 2007. 342–358
Ng T T, Chang S F, Tsui M P. Using geometry invariants for camera response function estimation. In: Proceedings of IEEE Conference on Computer Vision and Pattern Recognition, Minneapolis, 2007. 1–8
Johnson M K, Farid H. Exposing digital forgeries in complex lighting environments. IEEE Trans Inf Forens Secur, 2007, 2: 450–461
Kee E, Farid H. Exposing digital forgeries from 3-d lighting environments. In: Proceedings of IEEE International Workshop on Information Forensics and Security, Seattle, 2010. 1–6
O’Brien F J, Farid H. Exposing photo manipulation with inconsistent reflections. ACM Trans Graph, 2012, 31: 4
Johnson M K, Farid H. Detecting photographic composites of people. Digital Watermark, 2008, 19–33
Lukáš J, Fridrich J. Estimation of primary quantization matrix in double compressed jpeg images. In: Proceedings of Digital Forensic Research Workshop, Cleveland, 2003
Popescu A C. Statistical tools for digital image forensics. Dissertation for Ph.D. Degree. Hanover: Dartmouth College, 2005
Fu D D, Shi Y Q, Su W. A generalized benford’s law for jpeg coefficients and its applications in image forensics. In: Proceedings of SPIE 6505, Steganography, and Watermarking of Multimedia Contents IX, San Francisco, 2007. 65051L
He J F, Lin Z C, Wang L F, et al. Detecting doctored jpeg images via dct coefficient analysis. In: Proceedings of European Conference on Computer Vision, Graz, 2006. 423–435
Luo W Q, Qu Z H, Huang J W, et al. A novel method for detecting cropped and recompressed image block. In: Proceedings of the IEEE International Conference on Acoustics Speech and Signal Processing, Hawaii, 2007. 217–220
Qu Z H, Luo W Q, Huang J W. A convolutive mixing model for shifted double jpeg compression with application to passive image authentication. In: IEEE International Conference on Acoustics Speech and Signal Processing, Las Vegas, 2008. 1661–1664
Qu Z H, Luo W Q, Huang J W. Identifying shifted double jpeg compression artifacts for non-intrusive digital image forensics. In: Processing of International Conference on Computational Visual Media, Beijing, 2012. 1–8
Hyvärinen A, Oja E. Independent component analysis: algorithms and applications. Neural Netw, 2000, 13: 411–430
Bell A J, Sejnowski T J. An information-maximization approach to blind separation and blind deconvolution. Neural Comput, 1995, 7: 1129–1159
Chang C C, Lin C J. LIBSVM: a library for support vector machines. ACM Trans Intell Syst Techn, 2011, 2: 27
Li B, Shi Y Q, Huang J W. Detecting doubly compressed jpeg images by using mode based first digit features. In: Processings of IEEE Workshop on Multimedia Signal Processing, 2008. 730–735
Fan Z G, Queiroz de R L. Identification of bitmap compression history: JPEG detection and quantizer estimation. IEEE Trans Image Process, 2003, 12: 230–235
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Qu, Z., Luo, W. & Huang, J. A framework for identifying shifted double JPEG compression artifacts with application to non-intrusive digital image forensics. Sci. China Inf. Sci. 57, 1–18 (2014). https://doi.org/10.1007/s11432-013-5046-8
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11432-013-5046-8