Abstract
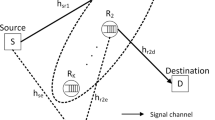
In this paper, we investigate secure communication in a two-hop wireless network, where multiple buffer-aided relays assist to securely forward data from the sender to the destination threatened by a passive eavesdropper. To satisfy the security and delay requirements, we propose a novel link selection policy without the instantaneous wiretap channel state information. Different from the most current link selection policies, the proposed link selection policy is designed by joint considering the link secrecy outage probability and the buffer states. To evaluate the secrecy performance, we first characterize the system state transition matrix and the stationary state probability, and then derive the closed-form expressions for the secrecy outage probability and the secrecy rate. Moreover, we formulate a framework based on the queuing theory to analyze the end-to-end information delay at the source, the relays, and the queues, and derive the closed-form expression for the information delay. Finally, we conduct simulations to validate our theoretical performance analysis, and verify the performance improvement of the proposed outage-driven secure transmission scheme in terms of secrecy outage probability and information delay.
Similar content being viewed by others
References
Wang G, Lin Y, Meng C, et al. Secrecy energy efficiency optimization for AN-aided SWIPT system with power splitting receiver. Sci China Inf Sci, 2019, 62: 029301
Wang L, Wong K K, Jin S, et al. A new look at physical layer security, caching, and wireless energy harvesting for heterogeneous ultra-dense networks. IEEE Commun Mag, 2018, 56: 49–55
Xu C, Zeng P, Liang W, et al. Secure resource allocation for green and cognitive device-to-device communication. Sci China Inf Sci, 2018, 61: 029305
Qi X H, Huang K Z, Li B, et al. Physical layer security in multi-antenna cognitive heterogeneous cellular networks: a unified secrecy performance analysis. Sci China Inf Sci, 2018, 61: 022310
Wyner A D. The wire-tap channel. Bell Syst Tech J, 1975, 54: 1355–1387
Csiszar I, Korner J. Broadcast channels with confidential messages. IEEE Trans Inform Theory, 1978, 24: 339–348
Leung-Yan-Cheong S, Hellman M. The Gaussian wire-tap channel. IEEE Trans Inform Theory, 1978, 24: 451–456
Rodriguez L J, Tran N H, Duong T Q, et al. Physical layer security in wireless cooperative relay networks: state of the art and beyond. IEEE Commun Mag, 2015, 53: 32–39
Arafa A, Shin W, Vaezi M, et al. Secure relaying in non-orthogonal multiple access: trusted and untrusted scenarios. IEEE Trans Inform Forensic Secur, 2020, 15: 210–222
Lim J T, Lee K, Han Y. Secure communication with outdated channel state information via untrusted relay capable of energy harvesting. IEEE Trans Veh Technol, 2020, 69: 11323–11337
Abdullah Z, Chen G, Abdullah M A M, et al. Enhanced secrecy performance of multihop IoT networks with cooperative hybrid-duplex jamming. IEEE Trans Inform Forensic Secur, 2021, 16: 161–172
Lin J, Li Q, Yang J, et al. Physical-layer security for proximal legitimate user and eavesdropper: a frequency diverse array beamforming approach. IEEE Trans Inform Forensic Secur, 2018, 13: 671–684
Deng Z, Li Q, Zhang Q, et al. Beamforming design for physical layer security in a two-way cognitive radio IoT network with SWIPT. IEEE Int Things J, 2019, 6: 10786–10798
Zhao R, Lin H, He Y C, et al. Secrecy performance of transmit antenna selection for MIMO relay systems with outdated CSI. IEEE Trans Commun, 2018, 66: 546–559
Fan L, Lei X, Yang N, et al. Secrecy cooperative networks with outdated relay selection over correlated fading channels. IEEE Trans Veh Technol, 2017, 66: 7599–7603
Zhu F C, Gao F F, Zhang T, et al. Physical-layer security for full duplex communications with self-interference mitigation. IEEE Trans Wirel Commun, 2016, 15: 329–340
Zheng T X, Wang H M, Yuan J, et al. Physical layer security in wireless ad hoc networks under a hybrid full-/half-duplex receiver deployment strategy. IEEE Trans Wirel Commun, 2017, 16: 3827–3839
Ni W, Zhang J A, Fang Z, et al. Analysis of finite buffer in two-way relay: a queueing theoretic point of view. IEEE Trans Veh Technol, 2018, 67: 3690–3694
Manoj B R, Mallik R K, Bhatnagar M R. Performance analysis of buffer-aided priority-based max-link relay selection in DF cooperative networks. IEEE Trans Commun, 2018, 66: 2826–2839
Razlighi M M, Zlatanov N. Buffer-aided relaying for the two-hop full-duplex relay channel with self-interference. IEEE Trans Wirel Commun, 2018, 17: 477–491
Morsi R, Michalopoulos D S, Schober R. Performance analysis of near-optimal energy buffer aided wireless powered communication. IEEE Trans Wirel Commun, 2018, 17: 863–881
Tian Z, Gong Y, Chen G J, et al. Buffer-aided relay selection with reduced packet delay in cooperative networks. IEEE Trans Veh Technol, 2017, 66: 2567–2575
Lan X L, Ren J J, Chen Q C, et al. Achievable secrecy rate region for buffer-aided multiuser MISO systems. IEEE Trans Inform Forensic Secur, 2020, 15: 3311–3324
Ren J J, Lei X F, Diamantoulakis P D, et al. Buffer-aided secure relay networks with SWIPT. IEEE Trans Veh Technol, 2020, 69: 6485–6499
Wan J, Qiao D, Wang H M, et al. Buffer-aided two-hop secure communications with power control and link selection. IEEE Trans Wirel Commun, 2018, 17: 7635–7647
Wang D W, Ren P Y, Cheng J L. Cooperative secure communication in two-hop buffer-aided networks. IEEE Trans Commun, 2018, 66: 972–985
Zhang Q, Liang Z J, Li Q Z, et al. Buffer-aided non-orthogonal multiple access relaying systems in Rayleigh fading channels. IEEE Trans Commun, 2017, 65: 95–106
Chen G J, Tian Z, Gong Y, et al. Max-ratio relay selection in secure buffer-aided cooperative wireless networks. IEEE Trans Inform Forensic Secur, 2014, 9: 719–729
Nakai R, Sugiura S. Physical layer security in buffer-state-based max-ratio relay selection exploiting broadcasting with cooperative beamforming and jamming. IEEE Trans Inform Forensic Secur, 2019, 14: 431–444
Gong Y, Chen G J, Xie T. Using buffers in trust-aware relay selection networks with spatially random relays. IEEE Trans Wirel Commun, 2018, 17: 5818–5826
Tang X X, Cai Y M, Huang Y Z, et al. Secrecy outage analysis of buffer-aided cooperative MIMO relaying systems. IEEE Trans Veh Technol, 2018, 67: 2035–2048
Liao X N, Zhang Y Y, Wu Z Q, et al. On security-delay trade-off in two-hop wireless networks with buffer-aided relay selection. IEEE Trans Wirel Commun, 2018, 17: 1893–1906
Liao X N, Zhang Y Y, Wu Z Q, et al. Buffer-aided relay selection for secure two-hop wireless networks with decode-and-forward relays and a diversity-combining eavesdropper. Ad Hoc Netw, 2020, 98: 102039
Zhang H S, Zhang H J, Liu W, et al. Energy efficient user clustering, hybrid precoding and power optimization in terahertz MIMO-NOMA systems. IEEE J Sel Areas Commun, 2020, 38: 2074–2085
Zhang H J, Zhang J M, Long K P. Energy efficiency optimization for NOMA UAV network with imperfect CSI. IEEE J Sel Areas Commun, 2020, 38: 2798–2809
Ke M L, Gao Z, Wu Y P, et al. Massive access in cell-free massive MIMO-based Internet of Things: cloud computing and edge computing paradigms. IEEE J Sel Areas Commun, 2021, 39: 756–772
Liao A W, Gao Z, Wang D M, et al. Terahertz ultra-massive MIMO-based aeronautical communications in space-air-ground integrated networks. IEEE J Sel Commun, 2021. doi: https://doi.org/10.1109/JSAC.2021.3071834
Cao K R, Wang B H, Ding H Y, et al. On the security enhancement of uplink NOMA systems with jammer selection. IEEE Trans Commun, 2020, 68: 5747–5763
Yue X W, Liu Y W, Yao Y Y, et al. Secure communications in a unified non-orthogonal multiple access framework. IEEE Trans Wirel Commun, 2020, 19: 2163–2178
Jiang W Y, Huang K Z, Xiao S F, et al. Secure transmission for heterogeneous cellular network with limited feedback. Sci China Inf Sci, 2020, 63: 220304
Gradshteyn I S, Ryzhik I M. Table of Integrals, Series, and Products. Orlando: Academic Press, 2014
Acknowledgements
This work was supported in part by National Natural Science Foundation of China (Grant Nos. 61901379, 61941119, 62071223, 62031012), in part by National Key Research and Development Project (Grant No. 2020YFB1807602), in part by Young Elite Scientist Sponsorship Program by CAST, in part by Open Research Fund of National Mobile Communications Research Laboratory, Southeast University (Grant No. 2020D04), and in part by Foundation of the Science, Technology, and Innovation Commission of Shenzhen Municipality (Grant No. JCYJ20190806160218174).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Wang, D., He, T., Zhou, F. et al. Outage-driven link selection for secure buffer-aided networks. Sci. China Inf. Sci. 65, 182303 (2022). https://doi.org/10.1007/s11432-021-3262-3
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11432-021-3262-3