Abstract
Social networks are fundamental mediums for diffusion of information and contagions appear at some node of the network and get propagated over the edges. Prior researches mainly focus on each contagion spreading independently, regardless of multiple contagions’ interactions as they propagate at the same time. In the real world, simultaneous news and events usually have to compete for user’s attention to get propagated. In some other cases, they can cooperate with each other and achieve more influences.
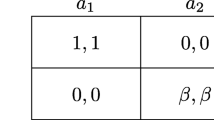
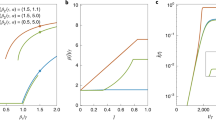
In this paper, an evolutionary game theoretic framework is proposed to model the interactions among multiple contagions. The basic idea is that different contagions in social networks are similar to the multiple organisms in a population, and the diffusion process is as organisms interact and then evolve from one state to another. This framework statistically learns the payoffs as contagions interacting with each other and builds the payoff matrix. Since learning payoffs for all pairs of contagions IS almost impossible (quadratic in the number of contagions), a contagion clustering method is proposed in order to decrease the number of parameters to fit, which makes our approach efficient and scalable. To verify the proposed framework, we conduct experiments by using real-world information spreading dataset of Digg. Experimental results show that the proposed game theoretic framework helps to comprehend the information diffusion process better and can predict users’ forwarding behaviors with more accuracy than the previous studies. The analyses of evolution dynamics of contagions and evolutionarily stable strategy reveal whether a contagion can be promoted or suppressed by others in the diffusion process.
Similar content being viewed by others
References
Pastor-Satorras R, Vespignani A. Epidemic spreading in scale-free networks. Physical Review Letters, 2001, 86(14): 3200–3203
Galuba W, Aberer K, Chakraborty D, Despotovic Z, Kellerer W. Outtweeting the twitterers-predicting information cascades in microblogs. In: Proceedings of the 3rd Conference on Online Social Networks. 2010, 3–11
Leskovec J, McGlohon M, Faloutsos C, Glance N, Hurst M. Patterns cascading behavior in large blog graphs. In: Proceedings of the 7th SIAM International Conference on Data Mining. 2007, 551–556
Yang J, Leskovec J. Modeling information diffusion in implicit networks. In: Proceedings of the 10th International Conference on Data Mining. 2010, 599–608
Centola D, Macy M. Complex contagions and the weakness of long ties. American Journal of Sociology, 2007, 113(3): 702–734
Cosley D, Huttenlocher D, Kleinberg J M, Lan X, Suri S. Sequential influence models in social networks. In: Proceedings of the 4th International AAAI Conference on Weblogs and Social Media. 2010, 26–33
Wu S, Hofman J M, Mason W A, Watts D J. Who says what to whom on twitter. In: Proceedings of the 20th International Conference on World Wide Web. 2011, 705–714
Kempe D, Kleinberg J, Tardos É. Maximizing the spread of influence through a social network. In: Proceedings of the 9th ACM SIGKDD International Conference on Knowledge Discovery and Data Mining. 2003, 137–146
Kempe D, Kleinberg J, Tardos É. Influential nodes in a diffusion model for social networks. Automata, Languages and Programming, 2005, 1127–1138
Weng L, Flammini A, Vespignani A, Menczer F. Competition among memes in a world with limited attention. Scientific Reports, 2012, 2
Myers S A, Leskovec J. Clash of the contagions: cooperation and competition in information diffusion. In: Proceedings of the 12th International Conference on Data Mining. 2012, 539–548
Smith J M, Price G R. The logic of animal conflict. Nature, 1973, 246: 15–18
McNamara J M, Gasson C E, Houston A I. Incorporating rules for responding into evolutionary games. Nature, 1999, 401(6751): 368–371
May R M, Leonard W J. Nonlinear aspects of competition between three species. SIAM Journal on Applied Mathematics, 1975, 29(2): 243–253
Doebeli M, Knowlton N. The evolution of interspecific mutualisms. In: Proceedings of the National Academy of Sciences, 1998, 95(15): 8676–8680
Axelrod R, Hamilton W D. The evolution of cooperation. Science, 1981, 211(4489): 1390–1396
Nowak M A, Sigmund K. Evolution of indirect reciprocity. Nature, 2005, 437(7063): 1291–1298
Nowak M A, Komarova N L, Niyogi P. Computational and evolutionary aspects of language. Nature, 2002, 417(6889): 611–617
Easley D, Kleinberg J. Networks, crowds, and markets: reasoning about a highly connected world. Cambridge University Press, 2010
Weibull J W. Evolutionary game theory. MIT Press, 1997
Gomez-Rodriguez M, Leskovec J, Krause A. Inferring networks of diffusion and influence. ACM Transactions on Knowledge Discovery from Data, 2012, 5(4): 21
Sadikov E, Medina M, Leskovec J, Garcia-Molina H. Correcting for missing data in information cascades. In: Proceedings of the 4th ACM International Conference on Web Search and Data Mining. 2011, 55–64
Zheng X, Zhong Y, Zeng D, Wang F Y. Social influence and spread dynamics in social networks. Frontiers of Computer Science, 2012, 6(5): 611–620
Bakshy E, Hofman J M, Mason W A, Watts D J. Everyone’s an influencer: quantifying influence on twitter. In: Proceedings of the 4th ACM International Conference on Web Search and Data Mining. 2011, 65–74
Sneppen K, Trusina A, Jensen M H, Bornholdt S. A minimal model for multiple epidemics and immunity spreading. PloS One, 2010, 5(10): e13326
Kuhlman C J, Kumar V S A, Marathe M V, Swarup S, Tuli G, Ravi S S, Rosenkrantz D J. Inhibiting the diffusion of contagions in bi-threshold systems: analytical and experimental results. AAAI Fall Symposium: Complex Adaptive Systems, 2011
Wang F, Wang H Y, Xu K. Diffusive logistic model towards predicting information diffusion in online social networks. In: Proceedings of the 32nd International Conference on Distributed Computing Systems Workshops. 2012, 133–139
Granovetter M. Threshold models of collective behavior. American Journal of Sociology, 1978: 1420–1443
Schelling T. Micromotives and macromotives. Norton, 1978
Goldenberg J, Libai B, Muller E. Talk of the network: a complex systems look at the underlying process of word-of-mouth. Marketing Letters, 2001, 12(3): 211–223
Hethcote H W. The mathematics of infectious diseases. SIAM Review, 2000, 42(4): 599–653
Newman M E. The structure and function of complex networks. SIAM Review, 2003, 45(2): 167–256
Pathak N, Banerjee A, Srivastava J. A generalized linear threshold model for multiple cascades. In: Proceedings of the 10th International Conference on Data Mining. 2010, 965–970
Prakash B, Beutel A, Rosenfeld R, Faloutsos C. Winner takes all: competing viruses or ideas on fair-play networks. In: Proceedings of the 21st International Conference on World Wide Web. 2012, 1037–1046
Karrer B, Newman M E J. Competing epidemics on complex networks. Physical Review E, 2011, 84(3): 036106
Bharathi S, Kempe D, Salek M. Competitive influence maximization in social networks. Internet and Network Economics, 2007: 306–311
Budak C, Agrawal D, EL Abbadi A. Limiting the spread of misinformation in social networks. In: Proceedings of the 20th International Conference on World Wide Web. 2011, 665–674
Narayanam R, Narahari Y. A shapley value-based approach to discover influential nodes in social networks. IEEE Transactions on Automation Science and Engineering, 2010, 99: 1–18
Chen W, Liu Z M, Sun X R, Wang Y J. A game-theoretic framework to identify overlapping communities in social networks. Data Mining and Knowledge Discovery, 2010, 21(2): 224–240
Jiang C X, Chen Y, Liu K J R. Evolutionary information diffusion over social networks. 2013, arXiv preprint arXiv:1309.2920
Ferrara E, JafariAsbagh M, Varol O, Qazvinian V, Menczer F, Flammini A. Clustering memes in social media. In: Proceedings of the 2013 IEEE/ACM International Conference on Advances in Social Networks Analysis and Mining. 2013, 548–555
Hogg T, Lerman K. Social dynamics of digg. EPJ Data Science, 2012, 1(1): 1–26
Lerman K, Ghosh R. Information contagion: an empirical study of the spread of news on digg and twitter social networks. ICWSM, 2010, 10: 90–97
Davis J, Goadrich M. The relationship between precision-recall and roc curves. In: Proceedings of the 23rd International Conference on Machine Learning. 2006, 233–240
Author information
Authors and Affiliations
Corresponding author
Additional information
Yuan Su received his Master degree in computer science and technology from Beijing University of Posts and Telecommunications (BUPT), China in 2012. He is currently a PhD candidate there. His research interest is social network analysis and data mining. He is currently working on modeling and predicting the information diffusion in social networks.
Xi Zhang received his BS degree from Harbin Institute of Technology, China in 2006, and his PhD degree from Tsinghua University, China in 2012. He is now an assistant professor in School of Computer Science at Beijing University of Posts and Telecommunications (BUPT), China. He is also in Key Laboratory of Trustworthy Distributed Computing and Service ofMinistry of Education, China. He has worked in the areas of data mining and computer architecture.
Lixin Liu received his BS degree in software engineering from Hebei University of Technology, China in 2012 and is currently a master student in Beijing University of Posts and Telecommunications (BUPT), China. His research interest is data mining. He is currently working on large scale graph mining.
Shouyou Song received his BS degree in computer science and technology from Huaqiao University, China in 2012 and is currently a master student in Beijing University of Posts and Telecommunications (BUPT), China. His research interest is complex networks and data mining. He is currently working on community detection in social networks.
Binxing Fang is a member of the Chinese Academy of Engineering and a professor in School of Computer Science at Beijing University of Posts and Telecommunications (BUPT), China. He received his PhD from Harbin Institute of Technology, China in 1989. He is currently the chief scientist of State Key Development Program of Basic Research of China, with the name Basic Research of Social Network Analysis and Network Information Diffusion. His current interests include social network analysis, IOT search, and information security.
Electronic supplementary material
Rights and permissions
About this article
Cite this article
Su, Y., Zhang, X., Liu, L. et al. Understanding information interactions in diffusion: an evolutionary game-theoretic perspective. Front. Comput. Sci. 10, 518–531 (2016). https://doi.org/10.1007/s11704-015-5008-y
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11704-015-5008-y