Abstract
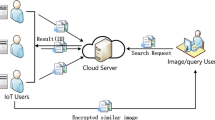
Internet of Things (IoT) has drawn much attention in recent years. However, the image data captured by IoT terminal devices are closely related to users’ personal information, which are sensitive and should be protected. Though traditional privacy-preserving outsourced computing solutions such as homomorphic cryptographic primitives can support privacy-preserving computing, they consume a significant amount of computation and storage resources. Thus, it becomes a heavy burden on IoT terminal devices with limited resources. In order to reduce the resource consumption of terminal device, we propose an edge-assisted privacy-preserving outsourced computing framework for image processing, including image retrieval and classification. The edge nodes cooperate with the terminal device to protect data and support privacy-preserving computing on the semi-trusted cloud server. Under this framework, edge-assisted privacy-preserving image retrieval and classification schemes are proposed in this paper. The security analysis and performance evaluation show that the proposed schemes greatly reduce the computational, communication and storage burden of IoT terminal device while ensuring image data security.
Similar content being viewed by others
Explore related subjects
Discover the latest articles and news from researchers in related subjects, suggested using machine learning.References
Liu B, Li Y, Zeng B, Lei C. An efficient trust negotiation strategy towards the resource-limited mobile commerce environment. Frontiers of Computer Science, 2016, 10(3): 543–558
Chen X, Huang X, Li J, Ma J, Lou W, Wong D. New algorithms for secure outsourcing of large-scale systems of linear equations. IEEE Transactions on Information Forensics and Security, 2015, 10(1): 69–78
Shen J, Wang C, Li T, Chen X, Huang X, Zhan Z H. Secure data uploading scheme for a smart home system. Information Sciences, 2018, 453: 186–197
Xiong J, Ren J, Chen L, Yao Z, Lin M, Wu D, Niu B. Enhancing privacy and availability for data clustering in intelligent electrical service of IoT. IEEE Internet of Things Journal, 2018
Wu D, Si S, Wu S, Wang R. Dynamic trust relationships aware data privacy protection in mobile crowd-sensing. IEEE Internet of Things Journal, 2018, 5(4): 2958–2970
Peng S, Yang A, Cao L, Yu S, Xie D. Social influence modeling using information theory in mobile social networks. Information Sciences, 2017, 379: 146–159
Cai Z, Yan H, Li P, Huang Z A, Gao C. Towards secure and flexible EHR sharing in mobile health cloud under static assumptions. Cluster Computing, 2017, 20(3): 2415–2422
Wang H, Zheng Z, Wu L, Li P. New directly revocable attribute-based encryption scheme and its application in cloud storage environment. Cluster Computing, 2017, 20(3): 2385–2392
Satyanarayanan M, Simoens P, Xiao Y, Pillai P, Chen Z, Ha K, Hu W L, Amos B. Edge analytics in the Internet of Things. IEEE Pervasive Computing, 2015, 14(2): 24–31
Li J, Huang X, Li J, Chen X, Xiang Y. Securely outsourcing attributebased encryption with checkability. IEEE Transactions on Parallel and Distributed Systems, 2014, 25(8): 2201–2210
Li J, Li J, Chen X, Jia C, Lou W. Identity-based encryption with outsourced revocation in cloud computing. IEEE Transactions on Computers, 2015, 64(2): 425–437
Li H, Liu D, Dai Y, Luan T. Engineering searchable encryption of mobile cloud networks: when QoE meets QoP. IEEE Wireless Communications, 2015, 22(4): 74–80
Xiong J, Zhang Y, Li X, Lin M, Yao Z, Liu G. RSE-PoW: a role symmetric encryption PoW scheme with authorized deduplication for multimedia data. Mobile Networks and Applications, 2018, 23(3): 650–663
Li X, Li J, Huang F. A secure cloud storage system supporting privacypreserving fuzzy deduplication. Soft Computing, 2016, 20(4): 1437–1448
Li J, Li J, Xie D, Cai Z. Secure auditing and deduplicating data in cloud. IEEE Transactions on Computers, 2016, 65(8): 2386–2396
Gao C, Cheng Q, He P, Susilo W, Li J. Privacy-preserving Naive Bayes classifiers secure against the substitution-then-comparison attack. Information Sciences, 2018, 444: 72–88
Li T, Li J, Liu Z, Li P, Jia C. Differentially private Naive Bayes learning over multiple data sources. Information Sciences, 2018, 444: 89–104
Li P, Li J, Huang Z, Li T, Gao C, Yiu S, Chen K. Multi-key privacypreserving deep learning in cloud computing. Future Generation Computer Systems, 2017, 74: 76–85
Seo S H, Nabeel M, Ding X, Bertino E. An efficient certificateless encryption for secure data sharing in public clouds. IEEE Transactions on Knowledge and Data Engineering, 2014, 26(9): 2107–2119
Ali M, Dhamotharan R, Khan E, Khan S U, Vasilakos A V, Li K, Zomaya A Y. SeDaSC: secure data sharing in clouds. IEEE Systems Journal, 2017, 11(2): 395–404
Wu Z, Tian L, Li P, Wu T, Jiang M, Wu C. Generating stable biometric keys for flexible cloud computing authentication using finger vein. Information Sciences, 2018, 433–434: 431–447
Zhang L, Jung T, Liu K, Li X, Ding X, Gu J, Liu Y. PIC: enable largescale privacy preserving content-based image search on cloud. IEEE Transactions on Parallel and Distributed Systems, 2017, 28(11): 3258–3271
Li J, Chen X, Li M, Li J, Lee P P C, Lou W. Secure deduplication with efficient and reliable convergent key management. IEEE Transactions on Parallel and Distributed Systems, 2014, 25(6): 1615–1625
Chen X, Li J, Huang X, Ma J, Lou W. New publicly verifiable databases with efficient updates. IEEE Transactions on Dependable and Secure Computing, 2015, 12(5): 546–556
Chen X, Li J, Weng J, Ma J, Lou W. Verifiable computation over large database with incremental updates. IEEE Transactions on Computers, 2016, 65(10): 3184–3195
Hahn F, Kerschbaum F. Searchable encryption with secure and efficient updates. In: Proceedings of the 2014 ACM SIGSAC Conference on Computer and Communications Security. 2014, 310–320
Kuzu M, Islam M S, Kantarcioglu M. Efficient similarity search over encrypted data. In: Proceedings of the 28th IEEE International Conference on Data Engineering. 2012, 1156–1167
Gao C, Lv S, Wei Y, Wang Z, Liu Z, Cheng X. M-SSE: an effective searchable symmetric encryption with enhanced security for mobile devices. IEEE Access, 2018, 6: 38860–38869
Cheng B, Zhuo L, Bai Y, Peng Y, Zhang J. Secure index construction for privacy-preserving large-scale image retrieval. In: Proceedings of the 4th IEEE International Conference on Big Data and Cloud Computing. 2014, 116–120
Ferreira B, Rodrigues J, Leitao J, Domingos H. Privacy-preserving content-based image retrieval in the cloud. In: Proceedings of the 34th IEEE Symposium on Reliable Distributed Systems (SRDS). 2015, 11–20
Xia Z, Wang X, Zhang L, Qin Z, Sun X, Ren K. A privacy-preserving and copy-deterrence content-based image retrieval scheme in cloud computing. IEEE Transactions on Information Forensics and Security, 2016, 11(11): 2594–2608
Cheng H, Zhang X, Yu J, Li F. Markov process-based retrieval for encrypted JPEG images. EURASIP Journal on Information Security, 2016, 2016(1): 1–9
Yan H, Li X, Wang Y, Jia C. Centralized duplicate removal video storage system with privacy preservation in IoT. Sensors, 2018, 18(6): 1814
Li Y, Wang G, Nie L, Wang Q, Tan W. Distance metric optimization driven convolutional neural network for age invariant face recognition. Pattern Recognition, 2018, 75: 51–62
Ferreira B, Rodrigues J, Leitao J, Domingos H. Practical privacypreserving content-based retrieval in cloud image repositories. IEEE Transactions on Cloud Computing, 2017, 99: 1
Zhang L, Jung T, Liu C, Ding X, Li X, Liu Y. EPPA: an efficient and privacy-preserving aggregation scheme for secure smart grid communications. In: Proceedings of the 35th International Conference on Distributed Computing Systems. 2015, 308–317
Hsu C Y, Lu C S, Pei S C. Image feature extraction in encrypted domain with privacy-preserving SIFT. IEEE Transactions on Image Processing, 2012, 21(11): 4593–4607
Hu S, Wang Q, Wang J, Qin Z, Ren K. Securing SIFT: privacypreserving outsourcing computation of feature extractions over encrypted image data. IEEE Transactions on Image Processing, 2016, 25(7): 3411–3425
Li T, Chen W, Tang Y, Yan H. A homomorphic network coding signature scheme for multiple sources and its application in IoT. Security and Communication Networks, 2018
Juan Ram T P, Fernando P G. Secure signal processing in the cloud: enabling technologies for privacy-preserving multimedia cloud processing. IEEE Signal Processing Magazine, 2013, 30(2): 29–41
Lin Q, Yan H, Huang Z, Chen W, Shen J, Tang Y. An ID-based linearly homomorphic signature scheme and its application in blockchain. IEEE Access, 2018, 6(1): 20632–20640
Fridrich J. Symmetric ciphers based on two-dimensional chaotic maps. International Journal of Bifurcation and Chaos, 1998, 8(6): 1259–1284
Belazi A, El-Latif A A A, Belghith S. A novel image encryption scheme based on substitution-permutation network and chaos. Signal Processing, 2016, 128: 155–170
Ping P, Xu F, Mao Y, Wang Z. Designing permutation-substitution image encryption networks with Henon map. Neurocomputing, 2018, 283(29): 53–63
Li X, Zhang G, Zhang X. Image encryption algorithm with compound chaotic maps. Journal of Ambient Intelligence and Humanized Computing, 2015, 6(5): 563–570
Paillier P. Public-key cryptosystems based on composite degree residuosity classes. In: Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques. 1999, 223–238
Lu R, Liang X, Li X, Lin X, Shen X. EPPA: an efficient and privacy-preserving aggregation scheme for secure smart grid communications. IEEE Transactions on Parallel and Distributed Systems, 2012, 23(9): 1621–1631
Acknowledgements
This work was supported by the Natural Science Foundation of Fujian Province, China (2017J05099); Science and Technology Planning Project of Guangdong Province, China (2015B010129015), the National Natural Science Foundation of China (Grant Nos. 61472091, 61722203, 61502102), the National Natural Science Foundation for Outstanding Youth Foundation (Grant No. 61722203).
Author information
Authors and Affiliations
Corresponding author
Additional information
Xuan Li received her PhD in computer science from South China University of Technology, China in 2012. Currently, she is an associate professor in College of Mathematics and Informatics at Fujian Normal University, China. Her recent research interests include applied cryptography and privacy protection.
Jin Li received his PhD degree in information security from Sun Yat-sen University in 2007. He is a professor at Guangzhou University, China. His research interests include applied cryptography and security in cloud computing.
Siuming Yiu received his PhD in computer science from The University of Hong Kong, China. Currently, he is an associate professor of the University of Hong Kong, China. His research interests include bioinformatics, computer security and cryptography.
Chongzhi Gao is a professor at the School of Computer Science of Guangzhou University, China. He received his PhD from Sun Yat-sen University, China in applied mathematics in 2004. His research interests include cryptography and privacy in machine learning.
Jinbo Xiong received his PhD degree in Computer System Architecture from Xidian University, China in 2013. Currently, he is working as an associate professor in the College of Mathematics and Informatics at Fujian Normal University, China.
Electronic supplementary material
Rights and permissions
About this article
Cite this article
Li, X., Li, J., Yiu, S. et al. Privacy-preserving edge-assisted image retrieval and classification in IoT. Front. Comput. Sci. 13, 1136–1147 (2019). https://doi.org/10.1007/s11704-018-8067-z
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11704-018-8067-z