Abstract
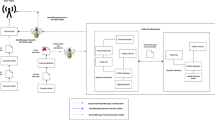
It is of great significance for headquarters in warfare to address the weapon-target assignment (WTA) problem with distributed computing nodes to attack targets simultaneously from different weapon units. However, the computing nodes on the battlefield are vulnerable to be attacked and the communication environment is usually unreliable. To solve the WTA problems in unreliable environments, this paper proposes a scheme based on decentralized peer-to-peer architecture and adapted artificial bee colony (ABC) optimization algorithm. In the decentralized architecture, the peer computing node is distributed to each weapon units and the packet loss rate is used to simulate the unreliable communication environment. The decisions made in each peer node will be merged into the decision set to carry out the optimal decision in the decentralized system by adapted ABC algorithm. The experimental results demonstrate that the decentralized peer-to-peer architecture perform an extraordinary role in the unreliable communication environment. The proposed scheme preforms outstanding results of enemy residual value (ERV) with the packet loss rate in the range from 0 to 0.9.
Similar content being viewed by others
Explore related subjects
Discover the latest articles and news from researchers in related subjects, suggested using machine learning.References
Guo D, Liang Z, Jiang P. Weapon-target assignment for multi-to-multi interception with grouping constraint. IEEE Access, 2019, 7: 34838–34849
Cao M, Fang W. Swarm intelligence algorithms for weapon-target assignment in a multilayer defense scenario: a comparative study. Symmetry, 2020, 12(5): 824
Sahin A M, Kemal L. Rule-based weapon target assignment on the battlefield. IFAC Proceedings Volumes, 2011, 44(1): 13600–13605
Ni M, Yu Z, Ma F, Wu X. A lagrange relaxation method for solving weapon-target assignment problem. Mathematical Problems in Engineering, 2011, 2011: 1–10
Ruan C, Zhou Z, Liu H, Yang H. Task assignment under constraint of timing sequential for cooperative air combat. Journal of Systems Engineering and Electronics, 2016, 27(4): 836–844
Kline A, Ahner D, Hill R. The weapon-target assignment problem. Computers & Operations Research, 2019, 105: 226–236
Shojaeifard A. Projection recurrent neural network model: a new strategy to solve weapon-target assignment problem. Neural Processing Letters, 2019, 50(3): 3045–3057
Gao C Q, Kou Y X. Multi-objective weapon target assignment based on D-NSGA-III-A. IEEE Access, 2019, 7: 50240–50254
Goldberg D E. Genetic algorithm in search optimization and machine learning. In: Proceedings of Genetic Algorithms in Search Optimization and Machine Learning. 1989, 2104–2116
Shi Y. Particle swarm optimization: developments, applications and resources. In: Proceedings of the 2001 Congress on Evolutionary Computation. 2001, 81–86
Karaboga D, Akay B. A comparative study of Artificial Bee Colony algorithm. Applied Mathematics and Computation, 2009, 214(1): 108–132
Lee Z J, Su S F, Lee C Y. A genetic algorithm with domain knowledge for weapon-target assignment problems. Journal of the Chinese Institute of Engineers, 2002, 25(3): 287–295
Lee Z J, Su S F, Lee C Y. Efficiently solving general weapon-target assignment problem by genetic algorithms with greedy eugenics. IEEE Transactions on Systems Man, and Cybernetics Part B (Cybernetics), 2003, 33(1): 113–121
Song Z H, Zhu F S, Zhang D L. A heuristic genetic algorithm for solving constrained Weapon-Target Assignment problem. In: Proceedings of IEEE International Conference on Intelligent Computing and Intelligent Systems. 2009, 336–341
Zeng X P, Zhu Y L, Nan L. Solving weapon-target assignment problem using discrete particle swarm optimization. In: Proceedings of World Congress on Intelligent Control & Automation. 2006, 3562–3565
Yang L, Zhai Z Z, Li Y H, Huang Y T. A multi-information particle swarm optimization algorithm for weapon target assignment of multiple kill vehicle. In: Proceedings of IEEE/ASME International Conference on Advanced Intelligent Mechatronics. 2018, 1160–1165
Lee Z J, Lee C Y, Su S F. An immunity-based ant colony optimization algorithm for solving weapon-target assignment problem. Applied Soft Computing, 2002, 2(1): 39–47
Karaboga D, Basturk B. A powerful and efficient algorithm for numerical function optimization: artificial bee colony (ABC) algorithm. Journal of Global Optimization, 2007, 39(3): 459–471
Cui L. A novel artificial bee colony algorithm with an adaptive population size for numerical function optimization. Information Science, 2017, 414: 53–67
Dean J, Ghemawat S. MapReduce: simplified data processing on large clusters. Communications of the ACM, 2008, 51(1): 107–113
Coulouris G, Dollimore J, Kindberg T, Blair G. Distributed System: Concepts and Design. Pearson Education, 2005
Lloyd S P, Witsenhausen H S. Weapons allocation is NP-complete. In: Proceedings of Summer Computer Simulation Conference. 1986, 1054–1058
Bianchi L, Dorigo M, Gambardella L M, Gutjahr W J. A survey on metaheuristics for stochastic combinatorial optimization. Natural Computing, 2009, 8(2): 239–287
Erik M, Pedersen H, Pedersen M. Good parameters for particle swarm optimization. Hvass Laboratories Technical Report HL1001. 2010, 1–12
Acknowledgements
This work was supported by the Foundation for Distinguished Young Scholars of Fujian Agriculture and Forestry University (xjq201809), MOST of Taiwan (107-2623-E-009-006-D).
Author information
Authors and Affiliations
Corresponding authors
Additional information
Xiaolong Liu received his BS degree from Xiamen University, China in 2011, his MS degree in Computer Science and Information Management from Providence University, China in 2013, his PhD degree in Institute of Computer Science and Engineering, Chiao Tung University, China in 2016. Since 2016, he has been an Associate Professor with the College of Computer and Information Sciences, Fujian Agriculture and Forestry University, China. He is the author of more than 40 peer-reviewed international journal and conference papers. His research interests include distributed computing, artificial intelligence and software security.
Jinchao Liang is now studying for his BS degree from College of Computer and Information Sciences, Fujian Agriculture and Forestry University, China. His current research interests include distributed computing, artificial intelligence.
De-Yu Liu received his BS degree and MS from Institute of Computer Science and Engineering, Chiao Tung University, China in 2016 and 2019, respectively. His current research interests include distributed computing, artificial intelligence.
Riqing Chen received the BEng degree in communication engineering from Tongji University, China in 2001, the MSc degree in communications and signal processing from Imperial College London, UK in 2004, and the DPhil degree in engineering science from the University of Oxford, UK in 2010. Since 2014, he has been a professor with Fujian Agriculture and Forestry University, China. His current research interests include cloud computing, wireless modulation, and transmission security.
Shyan-Ming Yuan received his PhD degree in Computer Science from the University of Maryland, USA in 1989. Since 1995, he has been a professor at the Department of Computer Science, Chiao Tung University, China. He is also the Director of Library at Chiao Tung University, China. He has authored or co-authored over 200 peer-reviewed papers. His current research interests include distance learning, internet technologies and distributed computing.
Electronic Supplementary Material
Rights and permissions
About this article
Cite this article
Liu, X., Liang, J., Liu, DY. et al. Weapon-target assignment in unreliable peer-to-peer architecture based on adapted artificial bee colony algorithm. Front. Comput. Sci. 16, 161103 (2022). https://doi.org/10.1007/s11704-021-0395-8
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11704-021-0395-8