Abstract
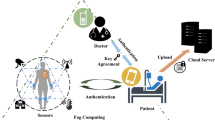
Because of its closeness to users, fog computing responds faster than cloud computing. Thus, it has been deployed to various applications, such as healthcare system. Recently, to ensure the secure communication of the fog-based healthcare system, Jia et al. proposed an authenticated key agreement scheme. Moreover, in view of the high computation cost existing in Jia et al.’s scheme, Ma et al. presented an efficient one using elliptic curve cryptography. In this paper, we observe that both the two schemes may potentially risk ephemeral key compromise attacks and need improving. Therefore, to overcome this potential risk, we propose a new authenticated scheme based on Jia et al.’s scheme using elliptic curve computational Diffie-Hellman hypothesis and hash functions. Additionally, we provide provable security under the adopted adversarial model and ProVerif simulation, and also analyze the performance in terms of computation and communication costs by comparisons. The analysis results show that the improved scheme resists the common attacks, reduces computation overhead, and has a certain significance.
Similar content being viewed by others
Explore related subjects
Discover the latest articles and news from researchers in related subjects, suggested using machine learning.References
Bellavista P, Berrocal J, Corradi A, Das S, Foschini L, Zanni A. A survey on fog computing for the Internet of Things. Pervasive and Mobile Computing, 2019, 52: 71–99
Dastjerdi A V, Buyya R. Fog computing: helping the Internet of Things realize its potential. Computer, 2016, 49(8): 112–116
Rocha Filho G P, Meneguette R I, Maia G, Pessin G, Gonçalves V P, Weigang L, Ueyama J, Villas L A. A fog-enabled smart home solution for decision-making using smart objects. Future Generation Computer Systems, 2020, 103: 18–27
Hou X, Li Y, Chen M, Wu D, Jin D, Chen S. Vehicular fog computing: a viewpoint of vehicles as the infrastructures. IEEE Transactions on Vehicular Technology, 2016, 65(6): 3860–3873
Mutlag A A, Ghani M K A, Arunkumar Na, Mohammed M A, Mohd O. Enabling technologies for fog computing in healthcare IoT systems. Future Generation Computer Systems, 2019, 90: 62–78
Kartheek D N, Bhushan B. Security issues in fog computing for Internet of Things. In: Architecture and Security Issues in Fog Computing Applications. IGI Global, 2020, 53–63
Mukherjee M, Matam R, Shu L, Maglaras L, Ferrag M A, Choudhury N, Kumar V. Security and privacy in fog computing: challenges. IEEE Access, 2017, 5: 19293–19304
Odelu V, Das A K, Wazid M, Conti M. Provably secure authenticated key agreement scheme for smart grid. IEEE Transactions on Smart Grid, 2016, 9(3): 1900–1910
Jia X, He D, Kumar N, Choo K K R. Authenticated key agreement scheme for fog-driven IoT healthcare system. Wireless Networks, 2019, 25(8): 4737–4750
Ma M, He D, Wang H, Kumar N, Choo K K R. An efficient and provably secure authenticated key agreement protocol for fog-based vehicular ad-hoc networks. IEEE Internet of Things Journal, 2019, 6(5): 8065–8075
Catarinucci L, De Donno D, Mainetti L, Palano L, Patrono L, Stefanizzi M L, Tarricone L. An IoT-aware architecture for smart healthcare systems. IEEE Internet of Things Journal, 2015, 2(6): 515–526
Abouelmehdi K, Beni-Hessane A, Khaloufi H. Big healthcare data: preserving security and privacy. Journal of Big Data, 2018, 5(1): 1–18
Handler D T, Hauge L, Spognardi A, Dragoni N. Security and privacy issues in healthcare monitoring systems: a case study. In: Proceedings of the 10th International Joint Conference on Biomedical Engineering Systems and Technologies. 2017, 383–388
Mahapatra B, Krishnamurthi R, Nayyar A. Healthcare models and algorithms for privacy and security in healthcare records. In: Tanwar S, Tyagi S, Kumar N, eds. Security and Privacy of Electronic Healthcare Records: Concepts, Paradigms and Solutions, IET, 2019, 183
Brandão P. The importance of authentication and encryption in cloud computing framework security. International Journal on Data Science and Technology, 2018, 4(1): 1–5
Chen T, Cheng Q, Li X. An anonymous key agreement protocol with robust authentication for smart grid infrastructure. Science China Information Sciences, 2022, 65(9): 1–3
Kumari S, Li X, Wu F, Das A K, Choo K K R, Shen J. Design of a provably secure biometrics-based multi-cloud-server authentication scheme. Future Generation Computer Systems, 2017, 68: 320–330
Li Y, Cheng Q, Liu X, Li X. A secure anonymous identity-based scheme in new authentication architecture for mobile edge computing. IEEE Systems Journal, 2020, 15(1): 935–946
Zhu Z. An efficient authentication scheme for telecare medicine information systems. Journal of Medical Systems, 2012, 36(6): 3833–3838
Arya K, Vidwansh A. A robust authentication scheme for telecare medicine information systems. International Journal of Computer Applications, 2015, 123(6): 5–10
Kang D, Lee D, Cho S, Jung J, Won D. Cryptanalysis and improvement of robust authentication scheme for telecare medicine information systems. In: Proceedings of the 11th International Conference on Ubiquitous Information Management and Communication. 2017, 1–8
Chen C M, Xiang B, Ke E W, Wu T Y, Lin J C W. Improvement of an anonymous and lightweight authentication scheme for TMIS. Journal of Applied Mathematics and Physics, 2018, 6(1): 18–28
Madhusudhan R, Nayak C S. An improved user authentication scheme for telecare medical information systems. In: Proceedings of IEEE/ACM International Conference on Connected Health: Applications, Systems and Engineering Technologies. 2018, 100–105
Jiang Q, Chen Z, Ma J, Ma X, Shen J, Wu D. Optimized fuzzy commitment based key agreement protocol for wireless body area network. IEEE Transactions on Emerging Topics in Computing, 2021, 9(2): 839–853
Kumari S, Renuka K. A provably secure biometrics and ECC-based authentication and key agreement scheme for WSNs. International Journal of Communication Systems, 2020, 33(3): e4194
Jiang Q, Zhang N, Ni J, Ma J, Ma X, Choo K K R. Unified biometric privacy preserving three-factor authentication and key agreement for cloud-assisted autonomous vehicles. IEEE Transactions on Vehicular Technology, 2020, 69(9): 9390–9401
Computing F. The Internet of Things: extend the cloud to where the things are. Cisco White Paper, 2015
Bonomi F, Milito R, Zhu J, Addepalli S. Fog computing and its role in the Internet of Things. In: Proceedings of the 1st Edition of the MCC Workshop on Mobile Cloud Computing. 2012, 13–16
Barzegaran M, Cervin A, Pop P. Towards quality-of-control-aware scheduling of industrial applications on fog computing platforms. In: Proceedings of the Workshop on Fog Computing and the IoT. 2019, 1–5
Singh S P, Nayyar A, Kaur H, Singla A. Dynamic task scheduling using balanced VM allocation policy for fog computing platforms. Scalable Computing: Practice and Experience, 2019, 20(2): 433–456
Mahmud R, Koch F L, Buyya R. Cloud-fog interoperability in IoT-enabled healthcare solutions. In: Proceedings of the 19th International Conference on Distributed Computing and Networking. 2018, 1–10
Negash B, Gia T N, Anzanpour A, Azimi I, Jiang M, Westerlund T, Rahmani A M, Liljeberg P, Tenhunen H. Leveraging fog computing for healthcare IoT. In: Rahmani A, Liljeberg P, Preden J S, Jantsch A, eds. Fog Computing in the Internet of Things. Springer, Cham, 2018, 145–169
Chen T, Li X, Cheng Q. An enhanced key exchange protocol exhibiting key compromise impersonation attacks resistance in mobile commerce environment. Science China Information Sciences, 2021, 64(9): 1–3
Liu C L, Tsai W J, Chang T Y, Liu T M. Ephemeral-secret-leakage secure ID-based three-party authenticated key agreement protocol for mobile distributed computing environments. Symmetry, 2018, 10(4): 84
Bellare M, Pointcheval D, Rogaway P. Authenticated key exchange secure against dictionary attacks. In: Proceedings of International Conference on the Theory and Applications of Cryptographic Techniques. 2000, 139–155
Blanchet B. An efficient cryptographic protocol verifier based on prolog rules. In: Proceedings of the 14th IEEE Computer Security Foundations Workshop. 2001, 82–96
Acknowledgements
This work was supported by the National Natural Science Foundation of China (Grant Nos. U1708262, U1736203, 61872449).
Author information
Authors and Affiliations
Corresponding author
Additional information
Xinghua Li received the ME and PhD degrees in computer science from Xidian University, China in 2004 and 2007, respectively. He is currently a professor in the School of Cyber Engineering, Xidian University, China. His research interests include wireless networks security, privacy protection, cloud computing, and security protocol formal methodology. He is a member of the IEEE.
Ting Chen received the BS degree in Internet of Things Engineering from East China Jiaotong University, China in 2018. She is currently working toward the MS degree in Security of Cyberspace in Xidian University, China. Her research interests include authentication and security protocol.
Qingfeng Cheng received the MS degree from National University of Defense Technology, China in 2004 and PhD degree from Information Engineering University, China in 2011. He is now an associate professor in the State Key Laboratory of Mathematical Engineering and Advanced Computing, China. His research interests include cryptography and information security.
Jianfeng Ma received the ME and PhD degrees in computer software and communications engineering from Xidian University, China in 1988 and 1995, respectively. He is currently a professor in the School of Cyber Engineering, Xidian University, China. His research interests include information and network security, coding theory and cryptography. He is a member of the IEEE.
Electronic supplementary material
Rights and permissions
About this article
Cite this article
Li, X., Chen, T., Cheng, Q. et al. An efficient and authenticated key establishment scheme based on fog computing for healthcare system. Front. Comput. Sci. 16, 164815 (2022). https://doi.org/10.1007/s11704-021-0537-z
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11704-021-0537-z