Abstract
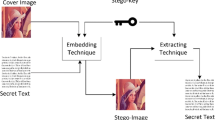
Security and imperceptibility are fundamental issues for steganography. This paper presents a multi-level steganography system based on concealing and deception. Basically, the secret image is embedded in a cover image, which in turn is embedded in another higher-level cover image. Each steganography level provides additional security, with lower levels implemented using stronger steganography methods. Furthermore, in the event that the higher level steganography is compromised, it would include misleading information to deceive the attacker that he/she is successfully eavesdropping. One challenge of hierarchical system is retaining hidden data in lower level in a higher level stenographic technique. To mitigate this issue, we designed a novel technique which combines discrete cosine transform and least significant bit (LSB). The technique objective is to maximize the capacity and invisibility of the secret image with minimal modification to the cover image (at most k-bits per block). The performance (capacity and peak signal-to-noise ratio) of the proposed method has superior performance compared with LSB since it combines the benefits of 1-bit and 3-bit LSBs. Furthermore, the paper demonstrates that the secret message is successfully embedded and extracted in two-level steganography system with peak signal-to-nose ratio greater than 20 dB.
Similar content being viewed by others
References
Johnson, N.F., Jajodia, S.: Exploring Steganography: Seeing the Unseen. IEEE Computers, George Mason University, pp. 26–34 (1998)
Morkel, T., Eloff, J., Olivier, M.: An overview of image steganography. In: The Fifth Annual Information Security South Africa Conference (ISSA2005), Sandton, June/July 2005, pp. 1–11
Provos N., Honeyman P.: Seek and hide: an introduction to steganography. IEEE Secur. Priv. 1, 32–44 (2003)
Wang H., Wang S.: Cyber warfare: steganography vs. steganalysis. Commun. ACM 47(10), 76–82 (2004)
Walia E., Jain P., Jain P.: An analysis of LSB & DCT based steganography. Glob. J. Comput. Sci. Technol. 10, 4–8 (2010)
Thomos, N., Boulgouris, N.V., Strintzis, M.G.: Optimized transmission of JPEG2000 streams over wireless channels. IEEE Transaction on Image Processing, pp. 54–67 (2006)
Deshpande, N., Sneha, K., Jacobs, D.: Implementation of LSB steganography and its evaluation for various bits. In: 2006 1st International Conference on Digital Information Management. pp. 173–178 (2007)
Varsaki, E., Fotopoulos, V., Skodras, A.: Data hiding based on image texture classification. Signal Image Video Process., Online, 18 May 2011. doi:10.1007/s11760-011-0229-5
Fridrich, J., Soukal, D.: Matrix embedding for large payloads. In: SPIE, Electronic Imaging, Security, Steganography, and Watermarking of Multimedia Contents VIII, vol. 6072, pp. W1–W15. San Jose, CA, January 16–19 (2006)
Raja, K., Chowdary, C., Venugopal, R., Patnaik, L.: A secure image steganography using LSB, DCT and compression techniques on raw images. In: 3rd International Conference on Intelligent Sensing and Information Processing, pp. 170–176, (2005)
Eggers, J., Bauml, R., Girod, B.: A communications approach to image steganography. In: Proceedings of SPIE, Security and Watermarking of Multimedia Contents IV, vol. 4675, pp. 1–12, San Jose (2002)
Tseng, H., Chang, C.: High capacity data hiding in JPEG compressed images. Informatica 1(1), 127–142, 2004, 0868–4952 (2004)
Fridrich, J., Goljan, M., Du, R.: Steganalysis based on JPEG compatibility. In: Proceedings of SPIE Multimedia Systems and Applications IV, vol. 4518, pp. 275–280. Colorado (2001)
Jain, A., Gupta, I.: A JPEG compression resistant steganography scheme for raster graphics images. in: TENCON 2007–2007 IEEE Region 10 Conference, vol. 2
Solanki, K., Sarkar, A., Manjunath, B.S.: Further study On Yass: steganography based on randomized embedding to resist blind steganalysis. In: Proceedings of Spie—Security, Steganography, And Watermarking Of Multimedia Contents (X), San Jose (2008)
Su P.-C., Kuo C.-C.J.: Steganography in JPEG2000 compressed images. IEEE Trans. Consumer Electron. 49(4), 824–832 (2003)
Noda H., Tsukamizu Y., Niimi M.: JPEG2000 steganography which preserves histograms of DWT coefficients. IEICE Trans. Inform. Syst. E90-D(4), 783–786 (2007)
Ishida, T., Yamawaki, K., Noda, H., Niimi, M.: Performance improvement of JPEG2000 steganography using QIM. J. Commun. Comput. 6:155–158, ISSN1548-7709, USA (2009)
Kekre, H., Athawale, A., Halankar, P., Banura, V.: Performance comparison of DCT and Walsh transform for steganography. In: ICWET Conference, India, pp. 81–88 (2010)
Fridrick, J., Kodovský, J., Goljan, M., Holub, V.: Steganalysis of content-adaptive steganography in spatial domain. In: 13th Information Hiding Conference, Prague, Czech Republic, May 18–20, 2011, LNCS vol. 6958, pp. 102–117. Springer, New York
Pevný, T., Filler, T., Bas, P.: Using high-dimensional image models to perform highly undetectable steganography. In: Fong, P. W. L., Böhme, R., Safavi-Naini R. (eds.) Information Hiding, 12th International Workshop, Lecture Notes in Computer Science, pp. 161–177, Calgary, June 28–30 (2010)
Westfeld, A., Pfitzmann, A.: Attacks on steganographic systems. In: Proceedings of Information Hiding—3rd Int’l Workshop, pp. 61–76. Springer, New York (1999)
Lyu, S., Farid, H.: Detecting hidden messages using higher-order statistics and support vector machines. Proceedings of 5th Int’l Workshop on Information Hiding, Springer, New York (2002)
Kodovsky, J., Pevný, T., Fridrick, J.: Modern Steganalysis Can Detect YASS, with Proceedings of SPIE, Electronic Imaging, Media Forensics and Security XII, San Jose, January 17–21, pp. 02-01–02-11, (2010)
Pevný, T., Bas, P., Fridrich, J.: Steganalysis by subtractive pixel adjacency matrix. In: Dittmann, J., Craver, S., Fridrich, J. (eds.) Proceedings of the 11th ACM Multimedia and Security Workshop, pp. 75–84, Princeton, September 7–8, 2009
Fridrick, J., Kodovský, J.: Steganalysis in high dimensions: fusing classifiers built on random subspaces. In: Proceedings of SPIE, Electronic Imaging, Media Watermarking, Security, and Forensics XIII, San Francisco, January 23–26, 2011. PDF
Park Y., et al.: Integrity verification of secret information in image steganography. In: Symposium on Information Theory and its Applications, Hakodate, Hokkaido, Japan, pp. 1–4 (2006)
Prasad K., Jyothsna V., Raju S., Indranell S.: High security image steganography in BCBS using DCT and fractal compression. IJCSNS 10, 162–170 (2010)
Shreelekshmi, R., Wilscy, M., Veni Madhavan, C.E.: Improved LSB steganalysis based on analysis of pixel pairs. Signal Image Video Process., Online, 17 October, 2011, doi:10.1007/s11760-011-0270-4
Provos, N., Honeyman, P.: Detecting steganographic content on the internet. In: Proceedings of 2002 Network and Distributed System Security Symposium, Internet Society, (2002)
Mohd, B., Abed, S., Al-Naami, B., Alouneh, S.: Image steganography optimization technique. In: International Joint Conference on Advances in Signal Processing and Information Technology, 2011, Amsterdam (to appear)
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Mohd, B.J., Abed, S., Na’ami, B. et al. Hierarchical steganography using novel optimum quantization technique. SIViP 7, 1029–1040 (2013). https://doi.org/10.1007/s11760-012-0301-9
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11760-012-0301-9