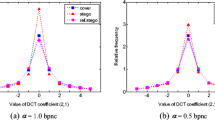
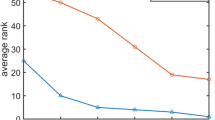
Abstract
This work proposes an improvement solution in identifying malicious user (or steganographer) who try to deliver hidden information in a batch of natural images. In this solution, a sampling construction strategy is proposed firstly. We design a probability calculation model by analying the principle of adaptive steganography, and then select DCT blocks with higher embedding probability to reconstruct a sample image, which is considered as the proof of extracting steganalysis features. Furthermore, inspired by the classical PEV-193 feature space, we reform a reduced PEV feature set including histogram features and intra-block co-occurrence features, which can capture more steganographic changes and match the sampling construction strategy well. Comprehensive experimental results show that comparing with the state-of-the-arts, the proposed scheme has a significant improvement in identifying potential steganographers in large-scale social media networks, and therefore is believed to be able to resist adaptive steganography with small payload.









Similar content being viewed by others
Notes
To ease notation, we assume that the number of images from each actor is the same. This assumption can be relaxed, and our method is still applicable.
References
JSTeg algorithm. Available from: http://zooid.org/%7epaul/crypto/jsteg/ [Accessed on 2011]
Westfeld A (2001) High capacity despite better steganalysis (f5-a steganographic algorithm). In: Proceedings of 4th international workshop on information hiding. Pittsburgh, PA, April 25–27, pp 289–302
Fridrich J, Pevný T, Kodovský J (2007) Statistically undetectable JPEG steganography: dead ends, challenges, and opportunities. In: Proceedings of the 9th ACM multimedia & security workshop, Dallas, TX, September 20–21, pp 3–14
Qin C, Chang C, Huang Y, Liao L (2013) An inpainting-assisted reversible steganographic scheme using a histogram shifting mechanism. IEEE Trans Circuits Syst Video Technol 23(7):1109–1118
Filler T, Fridrich J (2011) Design of adaptive steganographic schemes for digital images. In: Proceedings of SPIE, electronic imaging, media watermarking, security, and forensics XIII, San Francisco, CA, January 23–26
Guo L, Ni J, Shi Y (2014) Uniform embedding for efficient JPEG steganography. IEEE Trans Inf Forensics Secur 9(5):814–825
Holub V, Fridrich J, Denemark T (2014) Universal distortion function for steganography in an arbitrary domain. EURASIP J Inf Secur 1:1–16
Qin C, Zhang X (2015) Effective reversible data hiding in encrypted image with privacy protection for image content. J Vis Commun Image Represent 31:154–164
Shi Y, Chen C, Chen W (2006) A Markov process based approach to effective attacking JPEG steganography. In: Information hiding, 8th international workshop, vol 4437, pp 249–264
Pevný T, Fridrich J (2007) Merging Markov and DCT features for multi-class JPEG steganalysis. In: Proceedings of SPIE, Electronic Imaging, Security, Steganography, and Watermarking of Multimedia Contents IX, vol 6505, pp 3–14
Kodovský J, Fridrich J, Holub V (2012) Ensemble classifier for steganalysis of digital media. IEEE Trans Inf Forensics Secur 7(2):432–444
Pevný T, Ker A (2013) The challenges of rich features in universal steganalysis. In: Proceedings of SPIE, media watermarking, security, and forensics, vol 8665, pp M01–M15
Liu Q, Chen Z (2014) Improved approaches with calibrated neighboring joint density to steganalysis and seam-carved forgery detection in JPEG images. ACM Trans Intell Syst Technol (TIST) 5(4):63
Holub V, Fridrich J (2015) Low-complexity features for JPEG steganalysis using undecimated DCT. IEEE Trans Inf Forensics Secur 10(2):219–228
Holub V, Fridrich J (2015) Phase-aware projection model for steganalysis of JPEG images. In: Proceedings of SPIE, electronic imaging, media watermarking, security, and forensics XVII, San Francisco, CA, February 8–12, vol 9409
[Online]. http://www.flickr.com. [Accessed on March, 2016]
[Online]. http://www.instagram.com. [Accessed on March, 2016]
Ker A, Pevný T (2011) A new paradigm for steganalysis via clustering. In: Proceedings of SPIE, media watermarking, security, and forensics III. 78800U, vol 7880
Ker A, Pevný T (2012) Identifying a steganographer in realistic and heterogeneous data sets. In: Proceedings of SPIE, media watermarking, security, and forensics XIV, vol 8303, pp 0N 1–13
Ker A, Pevný T (2014) The steganographer is the outlier: realistic large-scale steganalysis. IEEE Trans Inf Forensics Secur 9(9):1424–1435
Li F, Wu K, Lei J, Wen M, Bi Z, Gu C (2016) Steganalysis over large-scale social networks with high-order joint features and clustering ensembles. IEEE Trans Inf Forensics Secur 11(2):344–357
Hou X, Zhang T, Xu C (2016) New framework for unsupervised universal steganalysis via SRISP-aided outlier detection. Signal Process Image Commun 47:72–85
Li F, Wu K, Lei J, Wen M, Ren Y (2017) Unsupervised steganalysis over social networks based on multi-reference sub-image sets. Multimedia Tools and Applications 1–19, to appear. https://doi.org/10.1007/s11042-017-4759-x
Böhme R (2008) Improved statistical steganalysis using models of heterogeneous cover signals. PhD thesis, Faculty of Computer Science, Technische Universität Dresden, Germany
Holub V (2014) Content adaptive steganography - design and detection. PhD thesis, Binghamton University, May 2014
Gretton A, Borgwardt K, Rasch M, Scholkopf B, Smola A (2007) A kernel method for the two-sample-problem. Advances in neural information processing systems 19. MIT Press, Cambridge, MA, pp 513–520
Kodovský J, Fridrich J (2009) Calibration revisited. In: Proceedings of the 11th ACM multimedia & security workshop, pp 63–74
Ker A, Pevný T (2012) Batch steganography in the real world. In: Proceedings of 14th ACM workshop multimedia security (MM&Sec), pp 1–10
DDE Download. Available from: http://dde.binghamton.edu/download/ [Accessed on March, 2016]
Li H, Liu D, Dai Y, Luan T (2015) Engineering searchable encryption of mobile cloud networks: when QoE meets QoP. IEEE Wirel Commun 22(4):74–80
Li H, Yang Y, Luan T, Liang X, Zhou L, Shen X (2016) Enabling fine-grained multi-keyword search supporting classified sub-dictionaries over encrypted cloud data. IEEE Trans Dependable Secure Comput 13 (3):312–325
Li H, Lin X, Yang H, Liang X, Lu R, Shen X (2014) An efficient privacy-preserving demand response scheme with adaptive key evolution in smart grid. IEEE Trans Parallel Distrib Syst 25(8):2053–2064
Yu J, Li F, Cheng H, Zhang X (2016) Spatial steganalysis using contrast of residuals. IEEE Signal Process Lett 23(7):989–992
Acknowledgements
This work was supported by Natural Science Foundation of China under Grants (61602295, 61572311, 615 72309, 61472236), Innovation Program of Shanghai Municipal Education Commission (14ZZ150,14YZ129), Natural Science Foundation of Shanghai (16ZR1413100) and the Excellent University Young Teachers Training Program of Shanghai Municipal Education Commission (ZZsdl15105).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Li, F., Wen, M., Lei, J. et al. Efficient steganographer detection over social networks with sampling reconstruction. Peer-to-Peer Netw. Appl. 11, 924–939 (2018). https://doi.org/10.1007/s12083-017-0603-3
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12083-017-0603-3