Abstract
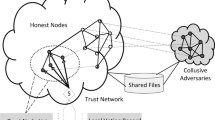
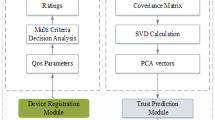
In recent days, Mobile Edge Computing (MEC) emerges as a new computing paradigm that pushes computing resources towards the edge of the Internet and close to end users and more scholars begin to carry out their different kinds of research under the framework of edge computing. Unlike cloud computing however, edge computing often lacks a centralized security mechanism, which increases the security risks of resource consumers. Therefore, to address security issues for facilitating MEC well, we focus on the establishment of an effective trust evaluation system in this paper. We presented a Reputation-based Trust Evaluation and Management (RTEM) system for a secure and efficient MEC network, wherein the edge servers are adopted to execute reputation data management for mobile edge nodes. In this system, a three-tier trust evaluation framework (identity trust, capability trust, behavior trust) was proposed to ensure the edge nodes that join the network system for service interaction are qualified, capable, and reliable. In order to update and calculate reputation data more accurately, we designed a reputation-based trust evaluation model and evaluated the effectiveness and robustness of our designed model on the OMNeT++ platform. The results show that our proposed mechanism can increase the transaction success rate of the edge network by more than two times compared with the network without trust evaluation mechanism, and perform better than the traditional subject logic (TSL) trust evalaution mechanism.










Similar content being viewed by others
References
Garcia Lopez P, Montresor A, Epema D et al (2015) Edge-centric computing: vision and challenges[J]. ACM SIGCOMM Computer Communication Review 45(5):37–42
Roman R, Lopez J, Mambo M (2016) Mobile edge computing, fog et al.: A survey and analysis of security threats and challenges[J]. Futur Gener Comput Syst 78(Part 2):680–698
Wang S, Zhang X, Zhang Y, Wang L, Yang J, Wang W (2017) A survey on mobile edge networks: convergence of computing, caching and communications. IEEE Access 5:67576779
Chen Y, Zhang N, Zhang Y, Chen X, Wu W, Shen X (2019) TOFFEE: task offloading and frequency scaling for energy efficiency of Mobile devices in Mobile edge computing. IEEE Transactions on Cloud Computing. https://doi.org/10.1109/TCC.2019.2923692
Chen Y, Zhang N, Zhang Y, Chen X, Wu W, Shen X (2019) Energy efficient dynamic offloading in Mobile edge computing for internet of things. IEEE Transactions on Cloud Computing. https://doi.org/10.1109/TCC.2019.2898657
Zhang D, Tan L, Ren J, Awad MK, Zhang S, Zhang Y Near-optimal and truthful online auction for computation offloading in green edge-computing systems. IEEE Trans Mob Comput to appear. https://doi.org/10.1109/TMC.2019.2901474
Duan S, Zhang D, Wang Y, Li L, Zhang Y (2019) JointRec: A deep learning-based joint cloud video recommendation framework for mobile IoTs. IEEE Internet Things J. https://doi.org/10.1109/JIOT.2019.2944889
Zhang D, Shen R, Ren J, Zhang Y Delay-optimal proactive service framework for block-stream as a service. IEEE Wireless Commun Lett 7(4):598–601. https://doi.org/10.1109/LWC.2018.2799935
Deyu Zhang, Ying Qiao, Liang She, Ruyin Shen, Ju Ren, and Yaoxue Zhang, Two timescale resource management for green internet of things networks”, IEEE Internet Things J to appear. DOI: https://doi.org/10.1109/JIOT.2018.2842766
Yan Z, Zhang P, Vasilakos AV (2014) A survey on trust management for internet of things[J]. Journal Netw Comput Appl 42(3):120–134
Gong S F, Zhu J L (2012) A Survey of Reputation and Trust Mechanism in Peer-to-Peer Network[C]// International Conference on Industrial Control and Electronics Engineer- ing.Xi'an:IEEE. 116–119
Tang W, Ren J, Zhang Y (2019) Enabling trusted and privacy-preserving healthcare Services in Social Media Health Networks. IEEE Trans Multimedia 21(3):579–590
Tang W, Ren J, Zhang K, Zhang D, Zhang Y, Shen XS (2019) Efficient and privacy-preserving fog-assisted health data sharing scheme. ACM Trans Intell Syst Technol. https://doi.org/10.1145/3341104 to appear
Marsh S P (1994) Formalising trust as a computational concept[J]. University of Stirling,
T.Beth, M.Borcherding, B.Klein (1994) Valuation of trust in open network[C]//Proceedings of the European Symposium on Research in Security (ESOR ICS) 3–18
M.Blaze, J.Feigenbaum, J.Lacy Decentralized trust management[C]//Proceedings of IEEE symposium on security and privacy. Los Alamitos: IEEE 164–173
Xiong L, Liu L PeerTrust: Supporting reputation-based trust for peer-to-peer electronic communities[C]//Proceedings of IEEE Transactions on knowledge and Data Engineering, 2004: 843–857
Xiong L, Liu L. A reputation-based trust model for peer-to-peer ecommerce Commu- nities[C] Proceedings of IEEE international Conference on electronic commerce, New York: ACM, 2003: 228–229
Kamvar SD, Scholosser Mt, Molina HG. The Eigen trust algorithm for reputation management in P2P networks[C]]//Proceedings of the 12th international world wide web Conf, New York: ACM, 2003: 640–651
Damiani E, Di Vimercati SDC, Paraboschi S et al (2003) Managing and sharing servants' reputations in P2P systems[J]. IEEE Trans Knowl Data Eng 15(4):840–854
Mrmol FG, Prez GM (2012) TRIP, a trust and reputation infrastructure-based proposal for vehicular ad hoc networks[J]. J Netw Comput Appl 35(3):934–941
Huang X, Yu R, Kang J, et al. (2017) Distributed reputation management for secure and efficient vehicular edge computing and networks[J]. IEEE Access pp(99):1–1
Kantert J, Edenhofer S, Tomforde S, et al. (2015) Representation of trust and reputation in self-managed computing systems[C]//2015 IEEE international conference on computer and information technology; ubiquitous computing and communications; dependable, autonomic and secure computing; pervasive intelligence and computing. IEEE 1827–1834
Li W, Song H (2016) ART: an attack-resistant trust management scheme for securing vehicular ad hoc networks[J]. IEEE Trans Intell Transp Syst 17(4):960–969
Li Z, Chigan CT (2014) On joint privacy and reputation assurance for vehicular ad hoc networks[J]. IEEE Trans Mob Comput 13(10):2334–2344
Noor TH, Sheng QZ, Yao L et al (2016) CloudArmor: supporting reputation-based trust management for cloud services[J]. IEEE Trans Parallel Distrib Syst 27(2):367–380
Resnick P, Zeckhauser R (2002) Trust among strangers in internet transactions: Empirical analysis of eBay's reputation system[M]//. In: The economics of the Internet and E-Commerce, Emerald Group Publishing Limited, pp 127–157
Mousa H, Mokhtar SB, Hasan O et al (2015) Trust management and reputation systems in mobile participatory sensing applications: a survey[J]. Comput Netw 90:49–73
Xu G, Zhang Y, Jiao L, Panaousis E, Liang K, Wang H, Li X (2019) DT-CP: a double-TTPs based contract-signing protocol with lower computational cost. IEEE Access. https://doi.org/10.1109/ACCESS.2019.2952213
Acknowledgements
The author gratefully acknowledges support from National Natural Science Foundation of China projects of grant No. 61772553, 61379058.
Author information
Authors and Affiliations
Corresponding author
Additional information
This article is part of the Topical Collection: Special Issue on Emerging Trends on Data Analytics at the Network Edge
Guest Editors: Deyu Zhang, Geyong Min, and Mianxiong Dong
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Deng, X., Liu, J., Wang, L. et al. A trust evaluation system based on reputation data in Mobile edge computing network. Peer-to-Peer Netw. Appl. 13, 1744–1755 (2020). https://doi.org/10.1007/s12083-020-00889-3
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12083-020-00889-3