Abstract
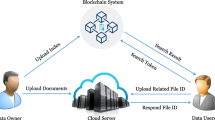
In data outsourcing services, to ensure data security and user privacy, data is usually stored in cloud servers in ciphertext form. This method makes users face the problem of how to search the keywords in the ciphertexts. Although the Dynamic Searchable Symmetric Encryption (DSSE) schemes can solve this problem, most DSSE schemes assume that all the data is stored in a single cloud server. The assumption is not realistic since data may be stored in multiple servers. Furthermore, the cloud servers are usually considered “honest-but-curious”, though malicious servers can actively attack and return incomplete or incorrect results. In this paper, we propose a Blockchain-based DSSE under the Multiple Clouds (BDSSE-MC) scheme. The scheme enables the data owner to generate encrypted local file indexes and merges the local indexes into a global index through a smart contract. The search operation is also performed by the smart contract based on the global index. In this scheme, the attacker cannot obtain the original files and search results, only knows the number of clouds and the number of files. We provide security and privacy analysis. We also compare the experiments results with those of traditional solutions.






Similar content being viewed by others
References
Chamani JG, Papadopoulos D, Papamanthou C, Rasool J (2018) New constructions for forward and backward private symmetric searchable encryption. In: Lie D, Mannan M, Backes M, Wang XF (eds) Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, CCS Toronto, ON, Canada, October 15-19, 2018. ACM, p 2018
He K, Chen J, Zhou Q, Du R, Xiang Y (2021) Secure dynamic searchable symmetric encryption with constant client storage cost. IEEE Trans Inf Forensics Secur 16:1538–1549
Wang J, Chow SSM (2019) Forward and backward-secure range-searchable symmetric encryption. IACR Cryptol ePrint Arch 2019:497
Du L., Li K, Liu Q, Wu Z, Zhang S (2020) Dynamic multi-client searchable symmetric encryption with support for boolean queries. Inf Sci 506:234–257
Demertzis I, Chamani JG, Papadopoulos D, Papamanthou C (2020) Dynamic searchable encryption with small client storage. In: 27th Annual network and distributed system security symposium, NDSS 2020, San Diego, California, USA, February 23-26, 2020. The Internet Society
Amjad G, Kamara S, Moataz T (2019) Forward and backward private searchable encryption with SGX. In: Proceedings of the 12th European workshop on systems security, EuroSec@EuroSys 2019, Dresden, Germany, March 25, 2019. ACM, pp 4:1– 4:6
Li J, Wen M, Wu K, Lu K, Li F, Li H (2019) Secure, flexible and high-efficient similarity search over encrypted data in multiple clouds. Peer Peer Netw Appl 12(4):893–911
Liu C, Zhu L, Chen J (2017) Efficient searchable symmetric encryption for storing multiple source dynamic social data on cloud. J Netw Comput Appl 86:3–14
Zhang C, Fu S, Ao W (2019) A blockchain based searchable encryption scheme for multiple cloud storage. In: Vaidya J, Zhang X, Li J (eds) Cyberspace safety and security - 11th international symposium, CSS 2019, Guangzhou, China, December 1-3, 2019. Cyberspace Safety and Security - 11th International Symposium, CSS 2019, Guangzhou, China, December 1-3, 2019, Proceedings, Part I, volume 11982 of Lecture Notes in Computer Science. Springer
Zarezadeh M, Mala H, Ashouri-Talouki M (2020) Multi-keyword ranked searchable encryption scheme with access control for cloud storage. Peer Peer Netw Appl 13(1):207–218
Wang H, Dong X, Cao Z (2019) Secure and efficient encrypted keyword search for multi-user setting in cloud computing. Peer Peer Netw Appl 12(1):32–42
Zhang C, Zhu L, Xu C, Zhang C, Sharif K, Wu H, Westermann H (2020) BSFP: blockchain-enabled smart parking with fairness, reliability and privacy protection. IEEE Trans Veh Technol 69(6):6578–6591
Shengshan H u, Cai C, Wang Q, Wang C, Luo X, Ren K (2018) Searching an encrypted cloud meets blockchain: A decentralized, reliable and fair realization. In: 2018 IEEE conference on computer communications, INFOCOM 2018, Honolulu, HI, USA, April 16-19, 2018. IEEE, pp 792–800
Li M, Zhu L, Lin X (2019) Efficient and privacy-preserving carpooling using blockchain-assisted vehicular fog computing. IEEE Internet Things J 6(3):4573–4584
Chen B, Wu L, Wang H, Zhou L, He D (2020) A blockchain-based searchable public-key encryption with forward and backward privacy for cloud-assisted vehicular social networks. IEEE Trans Veh Technol 69(6):5813–5825
Yan X, Yuan X, Ye Q, Tang Y (2020) Blockchain-based searchable encryption scheme with fair payment. IEEE Access 8:109687–109706
Yang Y, Lin H, Liu X, Guo W, Zheng X, Liu Z (2019) Blockchain-based verifiable multi-keyword ranked search on encrypted cloud with fair payment. IEEE Access 7:140818–140832
Jiang S, Liu J, Wang L, Yoo S-M (2019) Verifiable search meets blockchain: A privacy-preserving framework for outsourced encrypted data. In: 2019 IEEE International conference on communications, ICC 2019, Shanghai, China, May 20-24, 2019. IEEE, pp 1–6
Song DX, Wagner DA, Perrig A (2000) Practical techniques for searches on encrypted data. In: 2000 IEEE Symposium on security and privacy, Berkeley, California, USA, May 14-17, 2000. pp 44–55
Goh E-J (2003) Secure indexes. IACR Cryptol ePrint Arch 2003:216
Bloom BH (1970) Space/time trade-offs in hash coding with allowable errors. Commun ACM 13 (7):422–426
Curtmola R, Garay JA, Kamara S, Ostrovsky R (2006) Searchable symmetric encryption: improved definitions and efficient constructions. In: Proceedings of the 13th ACM conference on computer and communications security, CCS 2006, Alexandria, VA, USA, Ioctober 30 - November 3, 2006. pp 79–88
Kamara S, Papamanthou C, Roeder T (2012) Dynamic searchable symmetric encryption. In: the ACM Conference on computer and communications security, CCS’12, Raleigh, NC, USA, October 16-18, 2012, pp 965–976
Stefanov E, Papamanthou C, Shi E (2014) Practical dynamic searchable encryption with small leakage. In: 21st Annual network and distributed system security symposium, NDSS 2014, San Diego, California, USA, February 23-26, 2014. The Internet Society
Cash D, Jaeger J, Jarecki S, Jutla CS, Krawczyk H, Rosu M-C, Steiner M (2014) Dynamic searchable encryption in very-large databases: Data structures and implementation. In: 21st Annual network and distributed system security symposium, NDSS 2014, San Diego, California, USA, February 23-26, 2014. The Internet Society
Naveed M, Prabhakaran M, Gunter CA (2014) Dynamic searchable encryption via blind storage. In: 2014 IEEE Symposium on security and privacy, SP 2014, Berkeley, CA, USA, May 18-21, 2014. pp 639–654
Kamara S, Papamanthou C (2013) Parallel and dynamic searchable symmetric encryption. In: Financial cryptography and data security - 17th International Conference, FC 2013, Okinawa, Japan, April 1-5, 2013, Revised Selected Papers. pp 258– 274
Kurosawa K, Ohtaki Y (2013) How to update documents verifiably in searchable symmetric encryption. In: Abdalla M, Nita-Rotaru C, Dahab R (eds) Cryptology and network security - 12th International Conference, CANS 2013, Paraty, Brazil, November 20-22, 2013. Proceedings, volume 8257 of Lecture Notes in Computer Science. Springer, pp 309– 328
Bost R (2016) \(\sum \textit {o}\varphi \textit {o}{\varsigma }\): Forward secure searchable encryption. In: Weippl ER, Katzenbeisser S, Kruegel C, Myers AC, Halevi S (eds) Proceedings of the 2016 ACM SIGSAC Conference on computer and communications security, Vienna, Austria, October 24-28, 2016. ACM, pp 1143–1154
Wang H, Fan K, Li H, Yang Y (2020) A dynamic and verifiable multi-keyword ranked search scheme in the P2P networking environment. Peer Peer Netw Appl 13(6):2342–2355
Sharma D, Jinwala D (2021) Simple index based symmetric searchable encryption with result verifiability. Front Comput Sci 15(2):152805
Ge X, Yu J, Zhang H, Hu C, Li Z, Qin Z, Hao R (2021) Towards achieving keyword search over dynamic encrypted cloud data with symmetric-key based verification. IEEE Trans Dependable Secur Comput 18(1):490–504
Sisi Z, Souri A Blockchain technology for energy-aware mobile crowd sensing approaches in internet of things. Trans Emerg Telecommun Technol :e4217. e4217 ETT-20-1277.R1
Chen Y, Bai J, Hao Y, Liao S, Yi Z, Zhang H (2020) Blockchain-based dynamic group management for multiple keywords searchable encryption technology. In: International conference on cyber-enabled distributed computing and knowledge discovery, CyberC 2020, Chongqing, China, October 29-30, 2020. IEEE, pp 1–6
Li D, Deng L, Cai Z, Souri A Blockchain as a service models in the internet of things management: Systematic review. Trans Emerg Telecommun Technol :e4139. e4139 ETT-20-0827.R1
Shahidinejad A, Ghobaei-Arani M, Souri A, Shojafar M (2021) Saru Kumari. A technical report for light-edge A lightweight authentication protocol for iot devices in an edge-cloud environment. arXiv:2101.06676
Lv S, Huang Y, Li B, Wei Y, Liu Z, Liu J, Lee DH (2018) Forward secure searchable encryption using key-based blocks chain technique. In: Vaidya J, Li J (eds) Algorithms and architectures for parallel processing - 18th international conference, ICA3PP 2018, Guangzhou, China, November 15-17, 2018, Proceedings, Part IV, volume 11337 of Lecture Notes in Computer Science. Springer, pp 85–97
Li H, Tian H, Zhang F, He J (2019) Blockchain-based searchable symmetric encryption scheme. Comput Electr Eng 73:32–45
Lashkami SR, Atani RE, Arabnouri A, Salemi G (2020) A blockchain based framework for complete secure data outsourcing with malicious behavior prevention. In: 2020 28th Iranian conference on electrical engineering (ICEE). pp 1–7
Cai C, Yuan X, Wang C (2017) Hardening distributed and encrypted keyword search via blockchain. In: IEEE Symposium on Privacy-Aware Computing, PAC 2017, Washington, DC, USA, August 1-4, 2017. IEEE, pp 119–128
Chen L, Lee W-K, Chang C-C, Choo K-KR, Zhang N (2019) Blockchain based searchable encryption for electronic health record sharing. Future Gener Comput Syst 95:420– 429
Zhang C, Zhu L, Xu C, Sharif K, Zhang C, Liu X (2020) PGAS: privacy-preserving graph encryption for accurate constrained shortest distance queries. Inf Sci 506:325–345
Acknowledgements
This research is supported by the National Key Research and Development Program of China (Grant No. 2020YFB1006101) and the National Natural Science Foundation of China (Grant Nos. 61972037, 61872041, U1836212).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Xu, C., Yu, L., Zhu, L. et al. A blockchain-based dynamic searchable symmetric encryption scheme under multiple clouds. Peer-to-Peer Netw. Appl. 14, 3647–3659 (2021). https://doi.org/10.1007/s12083-021-01202-6
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12083-021-01202-6