Abstract
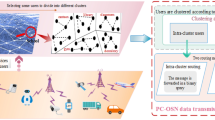
With the rapid development of 5G technology, mobile smart devices have become ubiquitous in daily life. The opportunistic social network composed of these mobile smart devices is a manifestation of the current network technology being upgraded to a new level. How to better perceive the spatiotemporal movement stated information about opportunistic social network nodes and establishing a suitable information prediction model is the key for the current research of opportunistic social networks. In the social network environment where widely distributed terminal carriers are members of the society, the network has the characteristics of sparsely distributed nodes, fast movement, and highly dynamic typologies, etc. Data transmission of nodes will cause great energy and overhead during the transmission. Aiming at this problem, this paper proposes an efficient path-sense message transmission strategy (EPST) based on Internet of Things systems in opportunistic social networks. It is a strategy proposed combining the social relationship and mobility characteristics of nodes. Furthermore, it proposes the problem of how to use the locally connected paths in opportunistic social networks. By studying the connectivity of network topology, it gives the identification method of stable locally connected subnets in the network and the method of effective path sensing. Simulation experiments show that this strategy can effectively improve the delivery ratio and greatly reduce network delay and overhead.











Similar content being viewed by others
Availability of data and materials
All data analyzed during the current study are included in the submission.
References
Cai L, Xiang S, Luo Y, Pan J (2011) Scalable modulation for video transmission in wireless net- works. IEEE Trans Veh Tech 60(9):4314–4323
Wang X, Cai L (2013) Proportional fair scheduling in hierarchical modulation aided wireless networks. IEEE Trans Wirel Commun 12(4):1584–1593
Zhang H, Cai L (2017) Bi-directional multi-hop wireless pipeline using physical-layer network coding. IEEE Trans Wireless Commun 16(12):7950–7965
Wu J, Yu G, Guan P (2019) Interest characteristic probability predicted method in social opportunistic networks. IEEE ACCESS 7(1):59002–59012
Wu J, Chen Z, Zhao M (2019) Information cache management and data transmission algorithm in opportunistic social networks. Wirel Netw 25(6):2977–2988
Peiyuan GUAN, Jia WU (2019) Effective data communication based on social community in social opportunistic networks. IEEE ACCESS 7(1):12405–12414
Wang X et al (2017) A novel approach for inhibiting misinformation propagation in human mobile opportunistic networks. Peer-to-Peer Netw Appl 10(2):377–394
Zhuang Y, Pan J, Luo Y, Cai L (2011) Time and location-critical emergency message dissemina- tion for vehicular ad-hoc networks. IEEE JSAC, special issue on Veh Commun Netw 29(1):187–196
Juang P, Oki H, Wang Y, Martonosi M, Peh LS, Rubenstein D (2002) Energy-Efficient computing for wildlife tracking: Design tradeoffs and early experiences with ZebraNet. In: Proc. of the 10th Int’l Conf. on Architectural Support for Programming Languages and Operating Systems. New York: ACM, 96−107
Gou F, Wu J (2022) Triad link prediction method based on the evolutionary analysis with IoT in opportunistic social networks. Comput Commun 12th Oct, 181C:143–155
Yang W, Luo J (2021) Application of information transmission control strategy based on incremental community division in IoT platform. IEEE Sensors J Oct 1st, 21(19):21968–21978. https://doi.org/10.1109/JSEN.2021.3102683
Dong Y, Chang L, Luo J et al (2021) A routing query algorithm based on time-varying relationship group in opportunistic social networks. Electronics 10:1595. https://doi.org/10.3390/electronics10131595
Wu S et al (2016) Node Service Ability Aware Packet Forwarding Mechanism in Intermittently Connected Wireless Networks. IEEE Trans Wirel Commun 15(12):1–1
Chen K, Shen H (2017) FaceChange: Attaining neighbor node anonymity in mobile opportunistic social networks with fine-grained control. IEEE/ACM Trans Netw 25(2):176–1189
Deng Y, Gou F (2021) Hybrid data transmission scheme based on source node centrality and community reconstruction in opportunistic social networks. Peer-to-Peer Netwo Appl 1–13. https://doi.org/10.1007/s12083-021-01205-3
Saha BK, Misra S, Pal S (2017) SeeR: Simulated annealing-based routing in opportunistic mobile networks. IEEE Trans Mob Comput 16(10):2876–2888
Huang R, Lin Y, Ying B, Nayak A (2018) ACP: An Efficient User Location Privacy Preserving Protocol for Opportunistic Mobile Social Networks. IEEE 42nd Annual Computer Software and Applications Conference (COMPSAC), Tokyo 610–619
Lu Y, Chang L, Luo J (2021) Routing algorithm based on user adaptive data transmission scheme in opportunistic social networks. Electronics 10:1138. https://doi.org/10.3390/electronics10101138
Newman ME (2004) Analysis of weighted networks. PhRvE 70
Azzuhri SR et al (2016) An efficient hybrid MANET-DTN routing scheme for OLSR. Wirel Pers Commun 89(4):1335–1354
Wu J, Chen Z, Zhao M (2020) An efficient data packet iteration and transmission algorithm in opportunistic social networks. J Ambient Intell Humaniz Comput 11:3141–3153. https://doi.org/10.1007/s12652-019-01480-2
Fang Z, Chang L, Luo J et al (2021) A data transmission algorithm based on triangle link structure prediction in opportunistic social networks. Electronics 10:1128. https://doi.org/10.3390/electronics10091128
Ni M, Pan J, Cai L (2015) Geometrical-based throughput analysis of device-to-device communications in a sector-partitioned cell. IEEE Trans Wirel Commun 14(4):2232–2244
Wu J, Tian X, Tan Y (2019) Hospital evaluation mechanism based on mobile health for IoT system in social networks. Comput Biol Med 109:138–147
Tong F, Wan Y, Zheng L, Pan J, Cai L (2017) A probabilistic distance-based modeling and analysis for cellular networks with underlaying device-to-device communications. IEEE Trans Wirel Commun 16(1):451–463
Wu X, Chang L, Luo J et al (2021) Efficient edge cache collaboration transmission strategy of opportunistic social network in trusted community. IEEE ACCESS 9:51772–51783. https://doi.org/10.1109/ACCESS.2021.3069992
Goel A, Rai S, Krishnamachari B (2004) Sharp thresholds for monotone properties in random geometric graphs. Thirty-sixth ACM Symposium on Theory of Computing ACM
Zhang L, Cai L, Pan J, Tong F (2014) A new approach to the directed connectivity in two- dimensional lattice networks. IEEE Trans Mob Comput 13(11):2458–2472
Fernandez-Marquez JL et al (2014) The ONE-SAPERE simulator: a prototyping tool for engineering self-organisation in pervasive environments. 2014 IEEE 8th International Conference on Self-Adaptive and Self-Organizing Systems (SASO) IEEE
Wu J, Gou F, Xiong W and Zhou X(2021) A Reputation Value-based Task-sharing Strategy in Opportunistic Complex Social Networks. Complexity. Volume 2021 , Article ID 8554351, 15 pages. https://doi.org/10.1155/2021/8554351.
Wang G, Wang B, Gao Y (2010) Dynamic spray and wait routing algorithm with quality of node in delay tolerant network. International Conference on Communications & Mobile Computing IEEE Computer Society
Liu K, Chen Z, Wu J, Wang L (2018) FCNS: A fuzzy routing-forwarding algorithm exploiting comprehensive mode similarity in opportunistic social networks. Symmetry 10.8
Funding
This work was supported in The National Natural Science Foundation of China(61672540, 6180338); Hunan Provincial Natural Science Foundation of China (2018JJ3299, 2018JJ3682); Fundamental Research Funds for the Central Universities of Central South University (2020zzts611).
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interests
The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper. The authors declare none financial interests/personal relationships which may be considered as potential competing interests.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Li, X., Qi, H. & Wu, J. Efficient path-sense transmission based on IoT system in opportunistic social networks. Peer-to-Peer Netw. Appl. 15, 811–826 (2022). https://doi.org/10.1007/s12083-021-01286-0
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12083-021-01286-0