Abstract
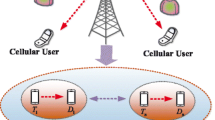
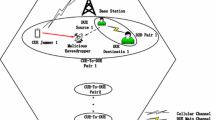
In this paper, we focus on the issue of security due to the open structure of the D2D Communication Underlaying Cellular Networks. In such an open scenario, the problem of interference is very serious. But luckily, the interference can be helpful from a perspective of the physical layer security. The interference caused by D2D communication could be helpful against eavesdroppers to enhance the secure communication of the cellular users when the value of the interference is proper. Note this, the physical layer security of the cellular users can be enhanced with the proper interference management based on the power allocation in D2D communication underlaying cellular networks in a probabilistic eavesdropping scenario. The problem is modeled as a Stackelberg game model. In the model, all cellular users are modeled as followers while the D2D pair is modeled as leader. A semi-centralized power allocation algorithm is proposed to converge to the Stackelberg Equilibrium. And the equilibrium is the final power allocation scheme we want. It is proved that the proposed algorithm can conclude in finite-time iterations. Numerical simulation results show that our proposed power allocation algorithm can obtain larger secrecy data rate, than the other two power allocation algorithms.










Similar content being viewed by others
References
Doppler K, Rinne M, Wijting C, Ribeiro C, Hugl K, Nokia Research Center (2009) Device-to-device communication as an underlay to lte-advanced networks. IEEE Commun Mag 47(12):42–49
Yu C-H, Tirkkonen O, Doppler K, Ribeiro C (2009) On the performance of device-to-device underlay communication with simple power control. In: Proceedings IEEE 69th Vehicular Technology Conference Spring, Barcelona
Lin X, Andrews J, Ghosh A, Ratasuk R (2014) An overview of 3GPP device-to-device proximity services. IEEE Commun Mag 52(4):40–48
Feng D, Lu L, Wu Y, Li G, Li S, Feng G (2014) Device-to-device communications in cellular networks. IEEE Commun Mag 52(4):49–55
Alam M, Yang D, Rodriguez J, Abd-Alhameed R (2014) Secure device-to-device communication in LTE-a. IEEE Commun Mag 52(4):66–73
He Y, Luan X, Wang J, Feng M, Wu J (2014) Power allocation for D2D communications in heterogeneous networks. In: Proceedings of the IEEE International Conference on Advanced Communication Technology, Pyeongchang, Korea
Xu C, Song L, Han Z, Zhao Q, Wang X, Jiao B (2012) Interference-aware resource allocation for device-to-device communications as an underlay using sequential second price auction. In: Proceedings of the IEEE International Conference on Communications, Ottawa
Xu C, Song L, Han Z, Li D, Jiao B (2012) Resource allocation using a reverse iterative combinatorial auction for device-to-device underlay cellular networks. In: Proceedings of the IEEE Global Communications Conference, Anaheim
Wang F, Song L, Han Z, Zhao Q (2013) Joint scheduling and resource allocation for device-to-device underlay communication. In: Proceedings of the IEEE Wireless Communications and Networking Conference, Shanghai, China, pp 732–737
Wang F, Xu C, Song L, Zhao Q, Wang X, Han Z (2013) Energy-aware resource allocation for device-to-device underlay communication. In: Proceedings of the IEEE International Conference on Communications, Budapest, Hungary
Yue J, Ma C, Yu H, Yang Z, Gan X (2013) Secrecy-based channel assignment for deviceto-device communication: an auction approach. In: Proceedings of the Wireless Communications and Signal Processing (WCSP 2013), Hangzhou
Yue J, Ma C, Yu H, Zhou W (2013) Secrecy-based access control for device-to-device communication underlaying cellular networks. IEEE Commun Lett 17(11):2068–2071
Qu J, Cai Y, Wu D, Chen H (2014) Stackelberg game based power allocation for physical layer security of device-to-device communication underlaying cellular networks. Frequenz 68(5-6):285–295
Duan B, Cai Y, Zheng J, Yang W, Yang W (2014) Bargaining-based jammer power allocation for dynamic eavesdropping scenario. Eurasip J Wirel Commun Netw 2014(1):1– 12
Chen H, Cai Y, Wu D (2015) Joint spectrum and power allocation for green d2d communication with physical layer security consideration. KSII Trans Internet Inf Syst 9(3):1057– 1073
Chen H, Wu D, Cai Y, Guan X (2015) Coalition Formation Based on coalition formation game. In: Proceedings Wireless Communications and Signal Processing (WCSP Nanjing)
Acknowledgment
This work is supported by the National Natural Science Foundation of China (No. 61371122, No. 61301162, No. 61301163) and Jiangsu Natural Science Foundation (BK20130067).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Qu, J., Cai, Y., Zheng, J. et al. Power allocation for device-to-device communication underlaying cellular networks under a probabilistic eavesdropping scenario. Ann. Telecommun. 71, 389–398 (2016). https://doi.org/10.1007/s12243-016-0515-x
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12243-016-0515-x